'Madi' Cyber Espionage Campaign in Middle East Uncovered [VIDEO]
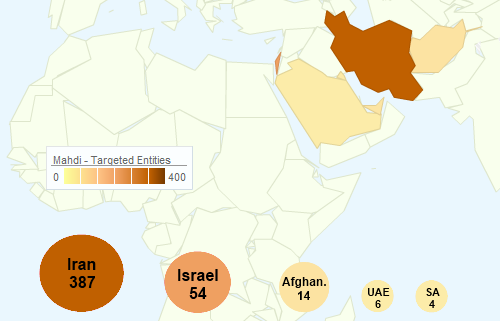
A new cyber espionage threat, known as Madi, has been uncovered targeting over 800 victims in Israel, Iran and Afganistan.
The active cyber-espionage campaign is targetting very specific victims including employees of critical infrastructure companies, financial services and government embassies, which are mainly located in Middle Eastern countries.
So far it is unclear whether or not this is a state-sponsored campaign like Stuxnet and Flame but the security company which first identified it, Seculert, has said the operation could require "a large investment and financial backing." However the Madi info-stealing malware is also technically rudimentary in comparison to Stuxnet and Flame.
Seculert contacted Kaspersky Lab who discovered the highly-sophisticated Flame virus in order to help track the activity of the malware.
Seculert first noticed an interesting, yet simple, spearphishing attack which seemed to be targeting victims in the Middle East and relied on social engineering techniques to spread.
The malware was embedded within documents, such as text files and PowerPoint presentations, sent to specific victims. Once opened the malware would install on the victim's PC and connect with one of four Command and Control (C&C) servers around the world - including Canada and Iran.
Info-stealing trojan
According to Kaspersky Lab, the Madi info-stealing Trojan enables remote attackers to steal sensitive files from infected Windows computers, monitor sensitive communications such as email and instant messages, record audio, log keystrokes, and take screenshots of victims' activities. Data analysis suggests that multiple gigabytes of data have been uploaded from victims' computers.
"While the malware and infrastructure is very basic compared to other similar projects, the Madi attackers have been able to conduct a sustained surveillance operation against high-profile victims," said Nicolas Brulez, Senior Malware Researcher at Kaspersky Lab. "Perhaps the amateurish and rudimentary approach helped the operation fly under the radar and evade detection."
While it is still unclear who is behind the Madi malware, one indicator of its provenance was discovered within the code: "Interestingly, our joint analysis uncovered a lot of Persian strings littered throughout the malware and the C&C tools, which is unusual to see in malicious code. The attackers were no doubt fluent in this language," said Aviv Raff, Chief Technology Officer at Seculert.
While it seems clear that Madi is not directly related to Flame or Stuxnet, it is impossible to say for certain where this malware originated, and considering the range of countries targeted, it could suggest a perpetrator outside the Middle East.
© Copyright IBTimes 2025. All rights reserved.






















