Adobe Password Security Criticised by Experts
Following a breach of security which saw email addresses and passwords of Adobe customers leaked, experts have criticised the company's lax security policies.

Earlier this week an allegedly Egyptian hacker calling himself ViruS_HimA hacked into an Adobe serverand stole more than 150,000 emails and encrypted passwords of Adobe employees and customers/partners of the firm including members of the US military, Google, Nasa and the UK government.
To validate his claim, ViruS_HimA published a limited set of records for users with email addresses ending in adobe.com, .mil and .gov.
The leaked information, contained the names, phones number, email, company, usernames and hashed or encrypted passwords of members of the Connectusers.com forum - an online community for users of Adobe's Connect video-conferencing service, which was not hacked.
Adobe confirmed the breach and took the Connectusers.com forum offline. It also said it was "in the process of resetting the passwords of impacted Connectusers.com forum members and will reach out to those members with instructions on how to set up new passwords once the forum services are restored."
Apology
Adobe apologised for the "inconvenience" of the breach, adding that "security is of critical importance to us," however some security experts would dispute this claim.
Tal Be'ery, a security researcher at Imperva, has seen some of the leaked information and how the passwords were stored.
"Based on an analysis of the leaked data, the password hashes - encrypted versions of the passwords - stored in the compromised Adobe database had been generated with MD5, a cryptographic hash function that's known to be insecure. This means that they can easily be cracked to recover the original passwords," Be'ery said.
Paul Ducklin, head of technology at security firm Sophos, also points out another issue with the way Adobe was storing their passwords.
"The passwords in the list are hashed, but without any salt. A salt is random content mixed with the password before hashing, so that repeated passwords do not cause repeated hashes.
"You simply must use salted hashes, to stop crackers using a simple pre-computed dictionary to crack your passwords super-fast."
Finally, Ducklin points out that the passwords used by a lot of the compromised account holders were far from ideal - and while this is not entirely Adobe's fault, the company could have insisted on stronger passwords when people are signing up to its service.
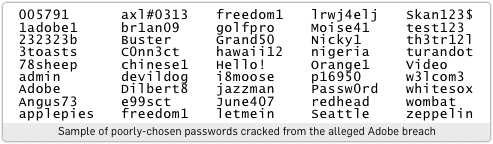
"Cracking this latest password list yields up the words breeze and connect (Adobe product names) four times each. Other repeated passwords include the what-were-they-thinking-of choices 123456, letmein and welcome.
"A few users tried to mix it up a bit: c0ffee introduced a numeric character and Hello! included both upper case and punctuation. But modern password crackers don't even break their stride to figure out that sort of permutation."
© Copyright IBTimes 2024. All rights reserved.







