China Arrests 1,500 People for Sending Spam Text Messages from Fake Mobile Base Stations
The black market for illegal telecoms equipment is growing rapidly
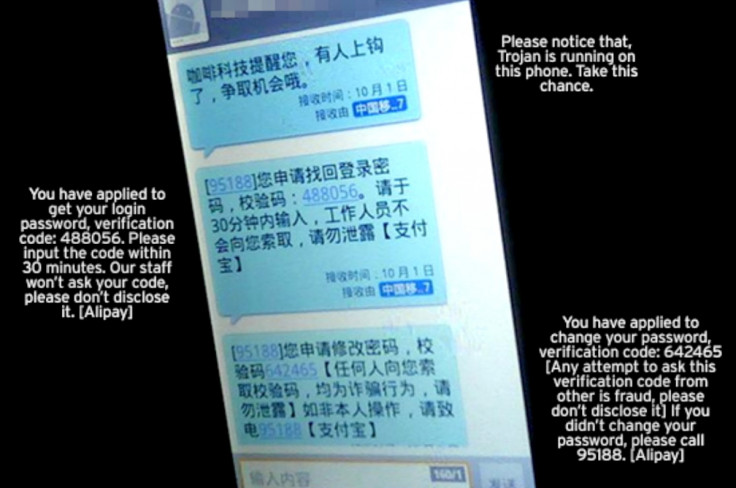
Chinese authorities have detained a total of 1,530 suspects in a crackdown on spam text messages being sent by illegal telecoms equipment, according to Chinese news agency ECNS.
Over 2,600 fake mobile base stations were seized and 24 sites manufacturing illegal telecoms equipment shut down as part of a massive nationwide operation involving nine central government and Communist Party of China departments.
Spam text messages are a big problem in China. Messages with phishing URLs are used to trick users into giving up private data, while SMS forwarders are used to intercept and steal authentication codes or password reset information from real messages sent by online payment providers to a user's registered mobile number.
Users can also be tricked into subscribing to premium text messages by a malicious mobile app, whereby every time they receive the spam text message, they could be charged £1, for example, which adds up but is less noticeable as a single entry on a mobile phone bill.
China's Ministry of Public Security said that it had identified 3,540 cases of suspected crimes, including one case where a Liaoning Province gang is suspected of sending out over 200 million spam messages.
Illegal telecoms equipment
A report released by Trend Micro this month looked into the telecoms equipment black market in China and found that cybercriminals routinely use either a GSM modem, an internet short message gateway and an SMS server to send out spam messages.

A GSM modem sends and receives text messages, with slots for several SIM cards at once. A 16-slot GSM modem can send out 9,600 spam text messages per hour.
An internet short message gateway, which connects to a PC and sends messages out over the internet, is even better for sending out spam messages as the equipment was designed to be used by mobile network operators and is many times faster.
However, would-be cyber criminals can also invest in an SMS server, which pretends to be a mobile base station and uses a high power signal to trick all smartphones in the same geographic location to disconnect from the mobile base stations belonging to actual mobile network operators.
Instead, the signal makes the smartphones connect to the fake base station where the server can send out up to 3,000 malicious spam text messages a minute and even hijack a mobile phone in five seconds.
A lucrative underground market
On the underground market, SMS servers come in "all-in-one" packages that include a laptop, a GSM mobile phone, an SMS server, an antenna to send out the fake signal and a USB cable, all for RMB 45,000 (£4,355).
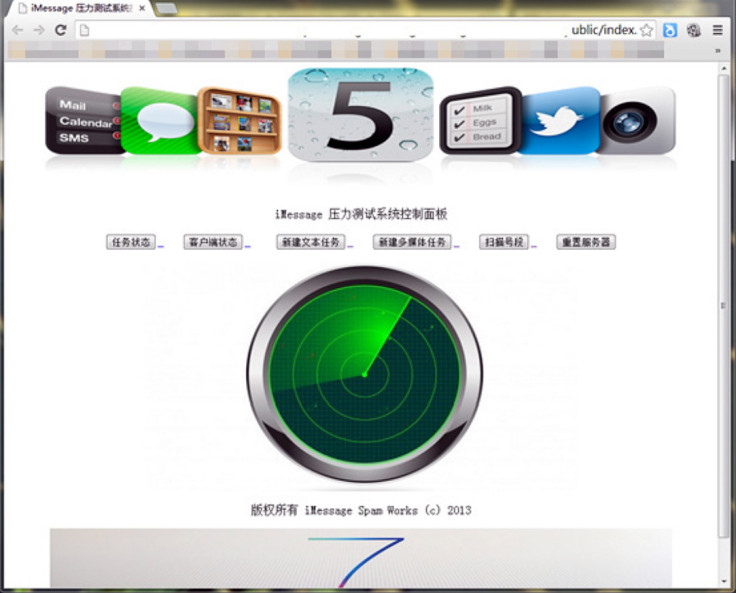
The source code for an SMS forwarder, which can intercept text messages from Android smartphones and even delete messages costs RMB 3,000.
Spamming iPhones is a bit harder as it's only possible if you can find mobile phone numbers connected to Apple IDs that are using the free internet-based iMessage function on the iPhone. iMessage spamming software costs RMB 30,000 or you can pay someone to send out 1,000 spam text messages for RMB 100.
There is even a software program that scans all existing mobile phone numbers to make sure that they are still in use before criminals send out the spam text messages.
"The barriers to launching cybercriminal operations lessened in number more than ever. Toolkits are becoming more available and cheaper; some are even offered free of charge. Prices are lower and features are richer. Underground forums are thriving worldwide, particularly in Russia, China, and Brazil," warned Trend Micro researcher Lion Gu.
"All of these developments mean that the computing public is at risk of being victimised more than ever and must completely reconsider how big a part security should play in their everyday computing behaviours."
© Copyright IBTimes 2024. All rights reserved.







