DDoS Attacks Rise by 240% in 2014, Says Security Watchdog

According to a new report distributed denial of service (DDoS) attacks are growing in size and frequency as cybercriminals evolve their attack methods to avoid improved security measures.
The report from security firm Incapsula looks at the two most common type of DDoS attack, network attacks which use huge volumes of traffic to attack critical infrastructure such as servers, and application level attacks, which target specific websites using armies of zombie computers called botnets.
According to the report, traffic created by application-layer DDoS attacks has risen 240% in 2014 compared to the same period in 2013.
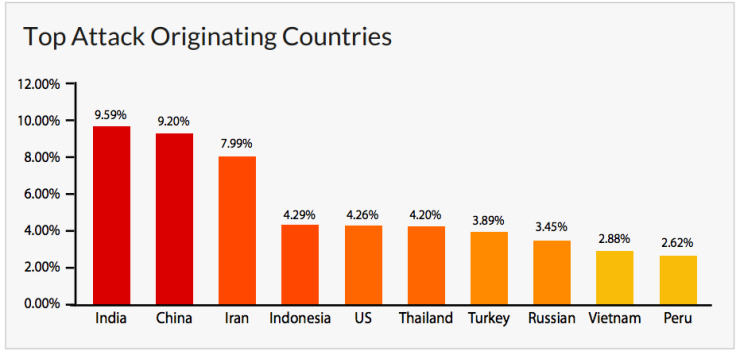
While the zombie computers which make up these botnets are spread around the globe, 50% of all attacks come from a group of just 10 countries, with India, China and Iran accounting for more than 25% of all traffic. The US is ranked fifth in the list of attacking countries.
Most of the devices used in these botnets are traditional computers, there is an increasing trend for cybercriminals to target connected devices, with Incapsula reporting that CCTV cameras are the most common target, thanks to easily guessable, default passwords.
Rent-a-botnet
Incapsula's research also discovered that botnets are being used repeatedly, with 29% hitting more than 50 targets over the 90-day period the security firm monitored them. Cybercriminals in charge of powerful botnets typically rent them out on a per-hour basis rather than using them to repeatedly target the same website.
One of the main uses of botnets is to knock competitor websites offline for a specific period, with botnets available to rent for as little as £5 per hour on underground forums.
Botnets are also evolving, with almost 30% of those observed for this study now accepting website cookies, which was one of the most common methods of botnet filtering. Incapsula even observed 1.8% of botnets which were able to execute JavaScript, another common bonnet filtering method.
"This data points to the reduced efficiency of these commonly used filtering methods. Even in the case of JS challenges, where the numbers are still typically low, the mere existence of "immune" offenders hints at the evolution we expect to see in the near future," the report said.
These application-level attacks seek to overwhelm websites by flooding login pages with requests, with between 50-100 requests per second enough to knock most mid-size websites offline, meaning these type of DDoS attacks don't require a huge volume of traffic - unlike network attacks.
Network DDoS attacks
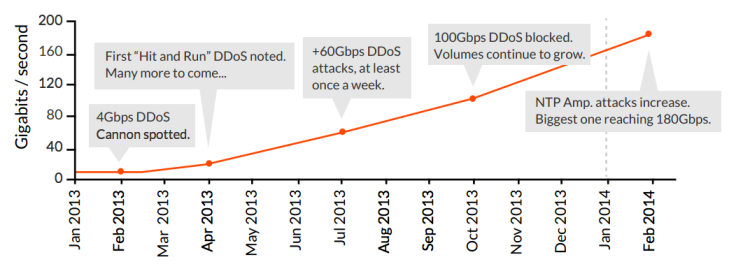
Last month, what has been categorised as the largest attack in the history of the internet peaked at 400Gbps, according to DDoS mitigation experts CloudFlare.
This attack is symptomatic of a trend in network DDoS attacks over the last 12 months, with attack volumes increasing at a rapid pace thanks to the adoption of new techniques (such as NTP reflection) as well as by the development of internet and specifically cloud infrastructures.
As well as increasing the volume of attacks, criminals are now using multi-vector attacks. Incapsula's figures show that 81% of all network attacks employed at least two different attack methods, with almost 39% using three or more different attack methods simultaneously.
As well as improving their chances of success by varying the attack methods, criminals are using this technique to create a smokescreen effect where one attack is used to distract the victim's attention while another attack happens at the same time.
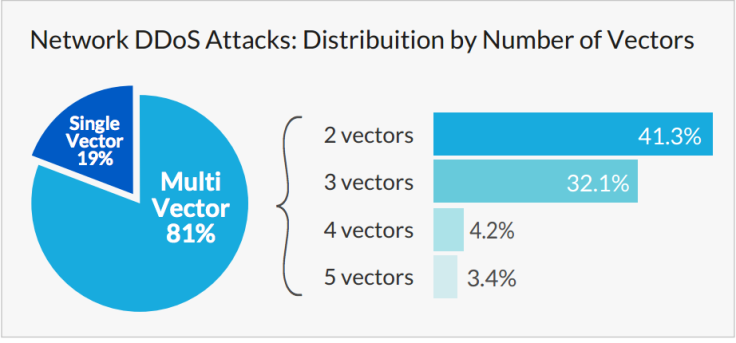
"The nature of the latest attack trends is a good indicator of the direction in which modern network DDoS attacks are now taking. The multi-vector approach, which is already used by the vast majority of all network attacks, is a clear indication of attackers' familiarity with current DDoS protection methods and the ways in which these methods can be bypassed and overcome."
The report was carried out by Incapsula, a security firm which focuses on website protection, and covers the 90 day period from 30 November to 27 February.
© Copyright IBTimes 2025. All rights reserved.





















