FBI Lied About How it Obtained Silk Road Server Location Says Security Expert

A security expert claims the FBI is lying about how it located the Icelandic server hosting the Silk Road underground drugs bazaar.
When Ross Ulbricht was arrested by the FBI and charged with being the operator of the billion dollar drugs empire known as Silk Road, one of the most intriguing questions for many was just how the law enforcement agency was able to locate the server hosting the website considering it was running on the anonymous Tor network.
Conspiracy theories quickly multiplied with many suggesting the FBI was informed about the server's location by the NSA after the spying agency had cracked the encryption of the anonymity network, which millions rely on daily to communicate securely and avoid being tracked online.
Ulbricht, who denies that he is the operator of the site - known as Dread Pirate Roberts, has questioned the FBI's methods in identifying the server, which was hosted in an Icelandic data center.
Kingpin
On Friday, the FBI presented its answer in an affidavit filed with the court in New York where Ulbricht is due to stand trial on counts including trafficking in narcotics (a new charge added last week), money laundering conspiracy, and a "kingpin" charge - which is typically laid against the heads of drug cartels and mafia organisations.
In the 58-page response to the defence's motion to suppress evidence, the FBI said that it had used a misconfiguration in the Silk Road login page to reveal the internet protocol (IP) address of the server.
Christopher Tarbell, the FBI agent leading the investigation and who has since left the agency, said the revelation of the IP address did not necessitate accessing any administrative systems or "back door" but simply involved typing "miscellaneous entries" into the username, password, and CAPTCHA fields on the website's login page.
This saw the server send back data to Tarbell's computer which he says contains information to identify the server:
"Upon examining the individual packets of data being sent back from the website, we noticed that the headers of some of the packets reflected a certain IP address not associated with any known Tor node as the source of the packets. This IP address was the only non-Tor source IP address reflected in the traffic we examined."
Unreasonable
And so, the FBI was able to locate the server hosting the Silk Road website and eventually arrest Ulbricht who they say is the mastermind behind the site. The FBI say that because no illegal spying methods were used in the capture of the server, all information gleaned from it is admissible in court.
In the wake of the publication of the FBI affidavit security researcher Nik Cubrilovic has examined the claims made by the agency, and Tarbell specifically, and his conclusion is that there is absolutely no way the information was obtained in the way they have outlined.
"The idea that the CAPTCHA was being served from a live IP is unreasonable. Were this the case, it would have been noticed not only by me – but the many other people who were also scrutinising the Silk Road website. Silk Road was one of the most scrutinised sites on the web, for white hats because it was an interesting challenge and for black hats since it hosted so many bitcoin (with little legal implication if you managed to steal them)," Cubrilovic wrote in an extensive blog post on the matter.
The researcher says that he even went to the effort of attempting to replicate the FBI's claims but found it impossible:
"I setup a virtual machine with a web server running a Tor hidden server. I then accessed the hidden server over Tor and looked at the traffic. No matter how much I intentionally misconfigured the server, or included scripts from clearnet hosts, I never observed traffic from a non-Tor node or a 'real' IP address."
Tor encryption cracked?
So, does this mean the FBI did get its information from the NSA illegally and that Tor's encryption has been broken?
Cubrilov doesn't think so.
As the researcher points out, people had pointed out security loopholes in the Silk Road website long before the FBI shut jot down.
In March 2013, a Reddit user published a post entitled WARNING: The Silk Road Revealed it's Public IP Last Night. The poster claimed to be a penetration tester who periodically tested Tor hidden services for security holes. While the Silk Road was offline for maintenance, the security researcher claims to have seen the public IP address of the website.
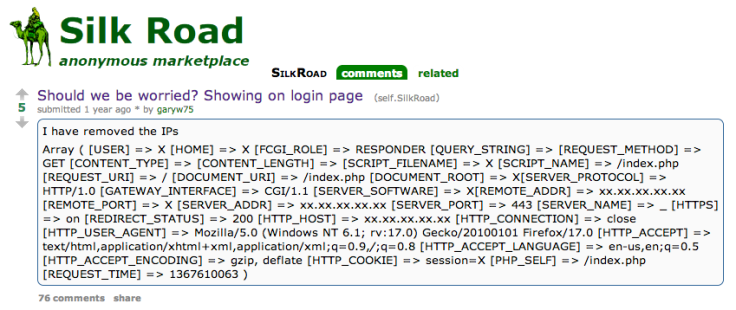
Two months later, another Reddit users posted a further warning that an IP address seemingly linked to the website's server was being posted on the site in error.
The FBI notes that Ulbricht himself logged these two incidents in a diary he kept of activity on the website.
Therefore, Cubrilovic posits that the FBI was monitoring the activity of Silk Road at this time and either saw the debug information or took advantage of security vulnerabilities in the login page. The reason the agency failed to mention this is down to the potential issues about legality it may raise:
"The FBI have good reason to not mention any bugs or forcing the server to do anything, and to pretend that they simply picked up the IP address from the wire, since such actions would raise concerns about how lawful their actions in uncovering the IP address were. What we do know is that their description of 'packet sniffing' for the IP through a 'leak' is impossible," Cubrilovic said.
© Copyright IBTimes 2025. All rights reserved.






















