Fireball malware could spark 'global catastrophe' after infecting 250 million computers
Check Point exposes 'sophisticated' malware allegedly spread by Chinese firm.

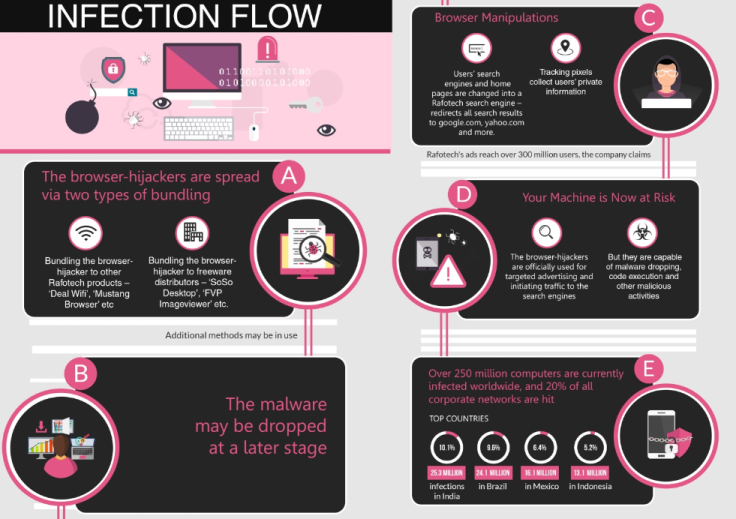
A massive malware campaign that has the power to "initiate a global catastrophe" has currently infected more than 250 million computers worldwide. The software, dubbed "Fireball", can take control of internet browsers, spy on victim's web use and potentially steal personal files.
According to Check Point, a cybersecurity firm, the operation is linked to Rafotech, a Chinese firm claiming to provide digital marketing and game apps to 300 million customers. It is allegedly using Fireball to manipulate victim's browsers, change search engines, and scoop up user data.
But experts warn the malware has the potential to cause a major cybersecurity incident worldwide.
Far from a legitimate service, it has the ability to run code, download files, install plug-ins, change computer configurations, spy on users and even act as an efficient malware dropper.
"How severe is it? Try to imagine a pesticide armed with a nuclear bomb. Yes, it can do the job, but it can also do much more," Check Point researchers wrote in a blog post this week (1 June). "Many threat actors would like to have even a fraction of Rafotech's power."
Rafotech did not immediately respond to a request for comment.
The experts said it observed 25.3 million of infections in India (10.1%), 24.1 million in Brazil (9.6%), 16.1 million in Mexico (6.4%), and 13.1 million in Indonesia (5.2%). In the US it witnessed 5.5 million infections (2.2%). They claimed 20% of all corporate networks globally may be impacted.
How you can be hit by Fireball
A form of "browser-hijacker", Fireball works by bundling itself to seemingly legitimate software. Check Point said Rafotech products such as "Deal WiFi", "Mustang Browser", "Soso Desktop" and "FVP Imageviewer" likely come bundled with the malicious strain of malware.
It is also likely Rafotech is using additional distribution methods, such as spreading freeware under fake names, spam, or even buying installs from threat actors, the security firm added.
The team said that, from a technical perspective, Fireball is sophisticated.
It found evidence of anti-virus evasion techniques and a command-and-control (C&C) infrastructure. Rafotech offers free software, relying on users to agree to install extra features.
In an in-depth research paper, Check Point claimed the massive campaign could possibly be the "largest infection operation in history."
It said the malware distribution is clearly "illegitimate", as the software often cannot be uninstalled by an ordinary user as it can conceal its true nature.
"It doesn't take much to imagine a scenario in which Rafotech decides to harvest sensitive information from all of its infected machines," the team wrote. "Banking and credit card credentials, medical files, patents and business plans can all be widely exposed and abused.
"Rafotech holds the power to initiate a global catastrophe.
"The full distribution of Fireball is not yet known, but it is clear that it presents a great threat to the global cyber-ecosystem. With a quarter billion infected machines and a grip in one of every five corporate networks, Rafotech's activities make it an immense threat."
How to check if you are infected
There are simple ways to check if you are infected with Fireball malware. First, open your internet browser and check if you are able to change it to another such as Chrome, Firefox or Explorer. Second, check your default search engine and ensure that can also be changed. Finally, scan all your browser extensions.
If you are unable to modify the options this is a sign that you're infected with adware, Check Point said.
How to remove Fireball malware
It may be removed from PCs by uninstalling the adware from Programs and Features in Windows Control Panel or by using Mac Finder function in the Applications folder on Apple devices.
All impacted users should restore their internet browser to default settings.
Check Point recently uncovered a number of malware campaigns hitting Google's Play Store, used to download applications. These, which included "FalseGuide" and "BankBot", had slipped through official censors. It also found "Judy", a huge malware strain that hit millions of users.
© Copyright IBTimes 2025. All rights reserved.





















