Hacking Team hacked: Spy tools sold to oppressive regimes Sudan, Bahrain and Kazakhstan

Hacking Team, a controversial Italian company which sells powerful surveillance tools to governments and law enforcement agencies, has had its systems breached and 400GB of internal documents leaked, showing that despite their denials, the company did sell its software to oppressive regimes in Sudan, Bahrain and Saudi Arabia.
The attack was carried out by unknown hackers who posted the internal documents on various file sharing websites, as well as defacing the company's Twitter account and replacing the company's logo to read "Hacked Team".
Hacking Team is one of a number of private companies which develop highly-sophisticated cybertools to allow the monitoring and surveillance of people's smartphones and computers and includes UK-based Gamma International - which itself was hacked back in August 2014.
Hacking Team has yet to respond to a request for comment from IBTimes UK but one of its employees Christian Pozzi has responded on Twitter, claiming that the download links contain viruses and suggesting that most of what the hackers are claiming is not true:
@hackingteam The torrent contains a virus, it's best to let the authorities examine the evidence and stop seeding and spreading false info.
— Christian Pozzi (@christian_pozzi) July 6, 2015
Pozzi also responded to various people on Twitter warning them that posting details of the leak would lead to their arrest as Hacking Team is currently working with the police in the wake of this attack.
From the US to UAE
According to security researchers who have been trawling through the cache of documents - which includes invoices, emails and customers lists - the list of countries which is using or has previously used Hacking Team's surveillance tools ranges from the United States to Saudi Arabia, Ethiopia and Sudan.
Here is the full list of countries using Hacking Team's tools according to the leak:
Egypt, Ethiopia, Morocco, Nigeria, Sudan, Chile, Colombia, Ecuador, Honduras, Mexico, Panama, United States, Azerbaijan, Kazakhstan, Malaysia, Mongolia, Singapore, South Korea, Thailand, Uzbekistan, Vietnam, Australia, Cyprus, Czech Republic, Germany, Hungary, Italy, Luxemburg, Poland, Russia, Spain, Switzerland, Bahrain, Oman, Saudi Arabia, United Arab Emirates
The sale of the cyberweapons to Sudan is one of the most controversial revelations from the data dump, as the United Nations has been investigating a report by Citizen Lab that Hacking Team's tools were being used in the country.
According to one leaked document, which has been posted on text-sharing website Pastebin, Hacking Team's own system has Sudan - and Russia - listed as "not officially supported".
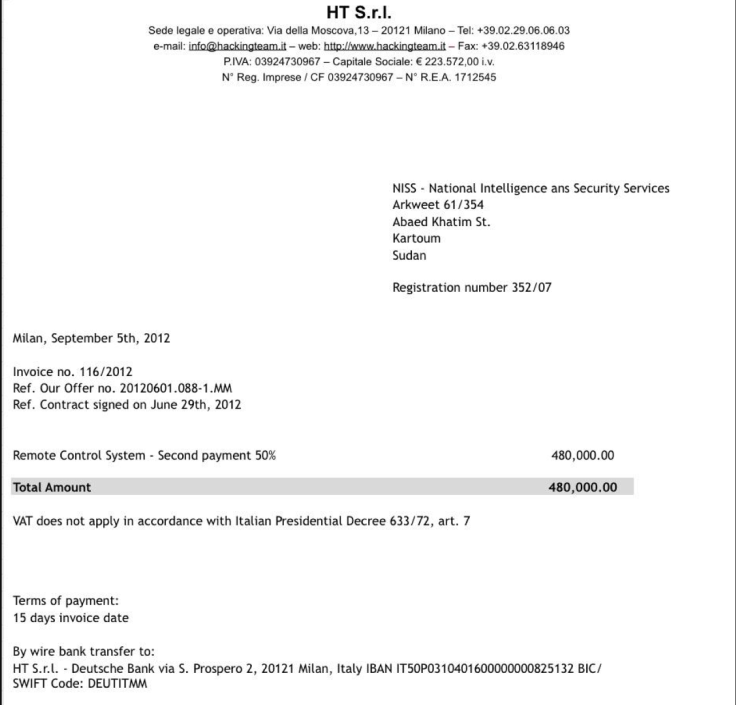
According to Christopher Soghoian from the American Civil Liberties Union (ACLU) the documents show that Hacking Team has been "stonewalling" the one-year long UN investigation and told the investigators that it doesn't have a business relationship with the Sudanese government.
However a leaked invoice (left) for the sum of€480,000 (£341,000) sent by Hacking Team to the Sudanese government for a 50% payment for use of the company's cyber-weapon Remote Control System, would suggest there is a business relationship.
Sudan is currently subject to an arms embargo by the UN which is incorporated into EU and UK law. It bans the export of "arms and related material" to the the country and also prohibits technical assistance, brokering services and other military-related services.
Enemies of the Internet
In the US, agencies using Hacking Team's tools include the FBI, the Drug Enforcement Agency and the Department of Defence.
The identity of the hackers remains a mystery, though some have suggested the same group that hacked Gamma International in 2014 is behind this attack.
Hacking Team has come in for a huge amount of criticism for the way it operates and the countries it reportedly does business with - leading Reporters Without Borders to list the company on its Enemies of the Internet index.
Speaking to IBTimes UK back in 2013, head of communications for Hacking Team Eric Rabe attempted to defend his company's sales' practices:
"The process under which Hacking Team sells its products is designed to make sure they are not abused and they are used in accordance with the applicable laws and international standards such as black lists that restrict where some products like this can be sold."
Research published by Citizen Lab in 2014 highlighted the powerful nature of Hacking Team's "lawful intercept tool" known as Da Vinci, which allows those using it to implant a piece of malware on your smartphone and take control of the device's microphone, camera, keyboard and even services like Facebook, WhatsApp and Skype. The Hacking Team's modules target Android, iOS, Windows Phone and BlackBerry and complement the tools which infect desktop software.
© Copyright IBTimes 2025. All rights reserved.























