Malware Posing as Official Google Play App Found in....Official Google Play Store

Malware posing as Google's own Play Store has been found in the offiical Google Play store and is avoiding detection while stealing your messages and banking details.
The piece of malware disguising itself as the official Google Play Store app is not being detected by the vast majority of security software and cannot be uninstalled from infected devices.
The malware is able to remain running in the background of smartphones it infects and can steal SMS messages, security certificates and even your bank account details.
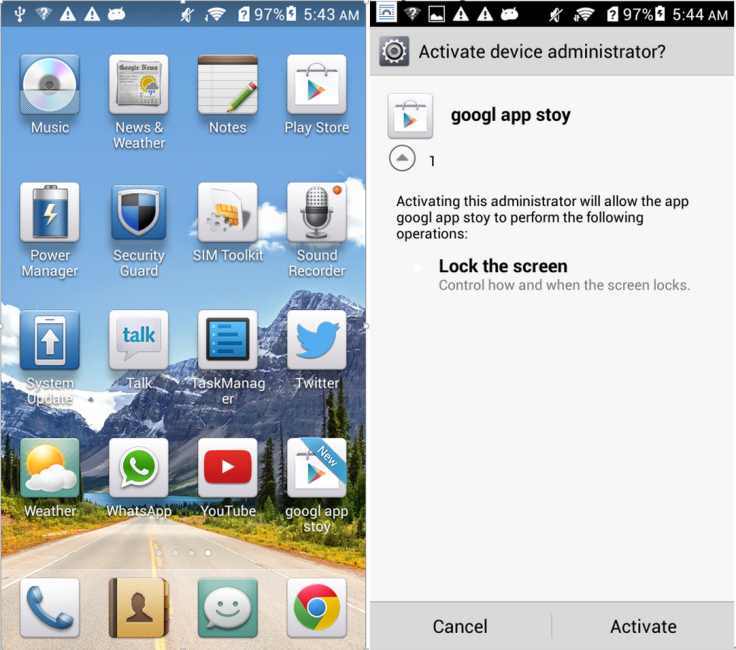
The sophisticated piece of malware - called "Googl app stoy" - was discovered in the official Google Play store by security company FireEye who then worked with Google to remove the app.
The innovative criminals who created the malicious app encrypt the malware module so that it is not detected when the app is being downloaded. FireEye says that just three out of 51 anti-virus vendors were able to detect this as a piece of malware.
The app uses the same icon as the official Google Play store and once downloaded it installs the icon on the homepage of your Android device.
When you click on it, the app asks for administrator privileges of the device. Once opened the sole user interface FireEye observed for the app contains pops up saying "Program Error" and "It's Deleted!" when translated to English from Korean.
Next, the app terminates and a notification message appears reading: "Unfortunately, google app stoy has stopped." After this occurs, the app icon on the homescreen is removed, tricking the user into thinking it's gone.
However the app remains running in the background as a service which cannot be stopped or uninstalled.
The app captures text messages, security certificates and banking details which it then sends to a Gmail address included in the malware - an email address which Google has now terminated.
© Copyright IBTimes 2024. All rights reserved.







