Stagefright: Android bug gives hackers control of your smartphone by sending a message

Last year the world went into meltdown worrying about the Heartbleed vulnerability which exposed a fundamental element of internet communications to hacking attacks, and prompted national newspapers in the UK to cry "CHANGE ALL YOUR PASSWORDS". Now a security research firm has uncovered a set of vulnerabilities within the Android operating system called Stagefright which prompted him to say: "If Heartbleed from the PC era sends chill down your spine, this is much worse."
What is Stagefright?
Stagefright is a media playback tool within Android and is also now the name by which a set of major security flaws in the world's most popular mobile operating system are known. The vulnerabilities could potentially allow any hacker to take remote control of your smartphone simply by knowing what your phone number is and sending you a multimedia message (MMS).
Who discovered it?
Researcher Joshua Drake at mobile security company Zimperium published details of his findings in a blog post called A Unicorn at the heart of Android. The blog post opens by saying the targets for this kind of attack "can be anyone from prime ministers, government officials, company executives, security officers to IT managers".
Drake calls it "the worst Android vulnerabilities discovered to date". Drake will present his finding to the Black Hat and DefCon hacker conferences at the beginning of August. Drake first reported the vulnerabilities to Google in April as well as sending patches for the security flaws.
Who does Stagefright affect?
Zimperium says that just about every active Android phone in use today is vulnerable. In terms of numbers, it says that 95% of 950 million smartphones are vulnerable, making Stagefright one of the most significant security vulnerabilities to affect smartphones ever. The vulnerability affects any Android device running Android 2.2 or higher
How does Stagefright work?
Exploiting Stagefright is a scarily simple process. The vulnerability affects the way Android handles video messages sent via text message. A hacker looking to exploit Stagefright would create a video with the malware embedded in it then send it to the the victim.
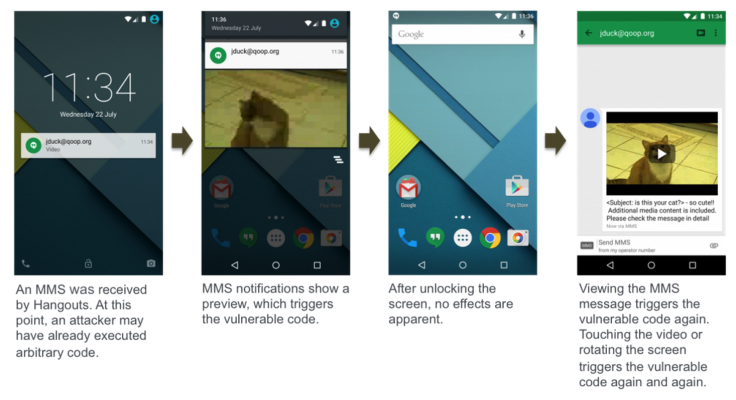
Because Android does the initial processing of video immediately once a message is received (in order that it will be ready for viewing instantly) the exploit is triggered. This means that the victim doesn't even have to watch the malicious video for it to infect the target smartphone.
Drake says that Hangouts, Google's messaging app for Android, processes messages instantly, while the phone's default messaging app may be a "tiny bit less dangerous" as you would actually have to view the message first before the exploit was triggered but crucially you would still not have to play the video for it to work.
What damage can it do?
The set of vulnerabilities discovered by Drake are all "remote code execution" bugs which means they would allow a hacker to gain complete control over your smartphone. Exploiting the vulnerabilities would allow hackers to copy, exfiltrate and delete data; take over your smartphone's microphone and camera to monitor your every word, and move or track your movements through your phone's GPS chip.
Once you gain access to the system, Android vulnerabilities could be "chained" to escalate privileges and give complete access to the system - with many such Android vulnerabilities easy to come by online.
The level of initial access will depend on what phone you are using with certain phones, like the Samsung Galaxy S4, giving system level access with just the initial exploit. "It's really up to their imagination what they do once they get in," Drake told NPR.
Is Stagefright being exploited?
According to Drake, there is no indication that the vulnerabilities he has discovered have been exploited in the wild - but that doesn't mean they won't be now that the flaws have been made public.
Is there a fix for StageFright?
Yes. Google responded to Drakes submission within 48 hours and it says that it has now fixed a total of seven vulnerabilities with patches sent to hardware partners. Google says that the patches will be deployed in the coming weeks or months.
One of the major problems for Android is fragmentation, which is highlighted by the fact that almost a year on from launching Android 5.0, less than 20% of the active user base is running it.
Once Google issues a software update, each manufacturer has to test it with their phones, then push it to networks around the world, who carry out their own testing, before finally pushing it to end users - a long process that sometimes means some phones are simply never updated.
Even Google's own Nexus smartphones, which run a stock version of Android, have not yet been fully patched.
Certain company's have already patched the flaw however, including the Android ROM Cyanogen which has issued a patch for its users; privacy-focused messaging company Silent Circle which has used Drakes patches, and Mozilla, whose Firefox Android browser uses Stagefright to play video, has also patched the bug in version 38.
© Copyright IBTimes 2024. All rights reserved.







