Turing Phone: Liquid metal smartphone 'impossible to hack' offering true offline encryption

The Turing Phone is a new smartphone which its creators claim is "impossible to hack" and offers a new type of end-to-end encryption to help users keep phone calls and data completely confidential.
Turing Robotics Industries (TRI), based in San Francisco, US and Shenzhen in China, has announced that it will be launching the Turing Phone – an Android-based smartphone that uses a completely new type of encryption technology than those in use elsewhere today.
Rather than relying on storing encryption keys on third-party servers and relying on outside companies to issue certificates, the Turing Phone will see no encryption keys stored anywhere but the phones themselves.
"Today, we have [security technologies like] Public Key Infrastructure (PKI) and Identity based Encryption (IBE). You submit a private key to a public server where a public certificate is issued to sender and receiver, so we refer to that as a centralised third-party certificate issuer," TRI's chief executive SYL Chao told IBTimes UK.
"The problem with this is the vulnerability with third party servers, which can be hacked [to] can change authentication and swap certificates, which leads to the big SSL certificate flaws today. The issuing of keys is hosted on the third-party server and the way to fix it is to create patches, but that's a passive way of doing security.
"This is why there's this huge problem of cybersecurity, so we took a slightly different approach, focusing on decentralised crypto key distributions."
Issuing crypto keys directly from the phone
Instead, Chao decided to reimagine security by starting with the device and taking the process off the internet so that no keys need to pass through external servers.
"We have what we call a master public key and a master private key, and instead of hosting the keys on a server, we bundle these two keys into a hardware chip on the Turing Key that we call the Turing Imitation Key (TIK)," he explained.
"Basically, the technology allows users to exchange crypto keys in an offline setting, which is called a static key exchange. This means that when I send you information like email, an SMS text message or files, I would first obtain your identity and then the key can be created and authenticated prior to any sort of communication, so you know the information will safely and securely reach only the device intended."
Chao, a fan of famous British war-time cryptologist and mathematician Alan Turing, says that he came up with the concept for the TIK in 2011, and initially he went to all the major smartphone manufacturers in the hope of implementing his technology on their phones, but the manufacturers were all content with the level of mobile security built into their phones.
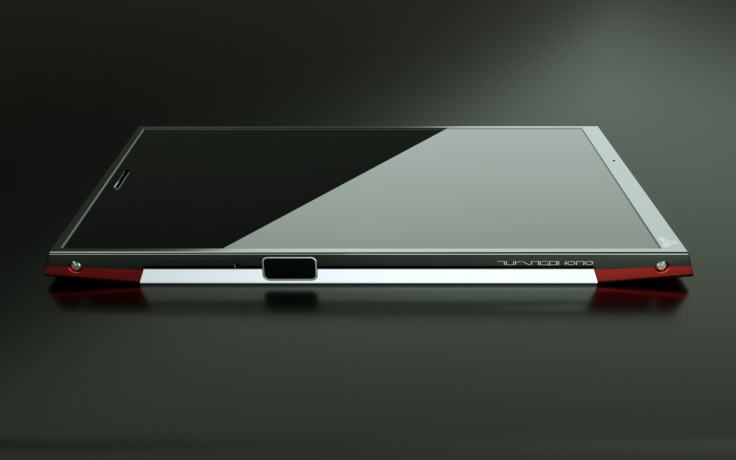
So instead he decided to build the phone himself, and teamed up with Professor Lugee Li, who developed a new super strong type of "liquid metal" called Liquidmorphium (an alloy of zirconium, copper, aluminium, nickel and silver) that is much stronger than titanium or steel.
The Turing Phone is targeted at consumers and enterprises, and TRI is currently in talks with mobile operators around the world to offer the phone on contract. The end-to-end encryption also only works when information or calls are transferred from one Turing Phone to another.
Making a mobile phone virtually impossible to hack

Apart from the secure TIK hardware chip, the phone will run a modified version of the Android 5.0 Lollipop mobile operating system known as the Turing UI, and feature a Qualcomm Snapdragon 801 processor, 13 megapixel camera, RFID, NFC, biometric fingerprint scanner, as well as gyro, motion, humidity, light and e-compass sensors.
There will be three versions of the phone – 16GB, 64GB and 128GB, and the 64GB version is expected to retail around $740 (£493) while the 128GB version will retail for $870 (£580) when it goes on sale in August.
In addition, Chao and his colleagues' work on the TIK has been certified by the International Telecommunication Union (ITU) to become a new global security standard – the ISO 29181-5.
"It's literally impossible to hack the phone as the keys reside inside the hardware chip. Whenever you have a hardware key it locks down the system, and the TIK can issue 10 (48) pairs of master public keys and master private keys, which is infinite," said Chao.
"Improving security is essential for Internet of Things (IOT) products. Hardware chips are difficult to replicate and this is why hardware security s always better than software security.
"Elephants can dance but they move slow. Not even the recent Blackberry CHACE initiative to secure mobile devices is being understood by the mainstream smartphone manufacturers. Based on my experience, it will be too late before they realise what they've missed."
© Copyright IBTimes 2024. All rights reserved.







