19 Fake Mobile Base Stations Found Across US – Are They For Spying or Crime?

The US manufacturer of a super secure mobile phone recently discovered 19 fake mobile base stations set up across the US that are quietly intercepting calls, SMS text messages and data from users' phones.
According to Popular Science, Les Goldsmith, the CEO of ESD America, a leading provider of defence and law enforcement technology, used its new CryptoPhone 500 to detect the fake mobile base stations.
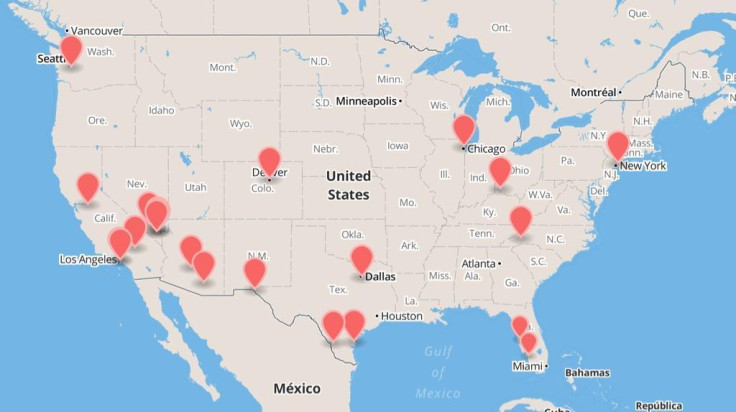
The CryptoPhone 500, which costs $3,500 (£2,127), is specially customised Android smartphone that pretends to be a Samsung Galaxy SIII. It was able to detect 17 fake mobile base stations in various states in the month of July, including big cities like New York, Chicago, Denver, Dallas, Seattle and Miami.
By August, the number of fake base stations had increased to 19, and in some cities, such as Los Angeles, Houston and Miami, there are more than one fake mobile base station in existence.
What are fake mobile base stations?
There is an underground market for illegal telecoms equipment, much of which comes from China. The equipment can be used to pretend to be a mobile base station, tricking all users' phones to connect to it as they pass close to areas where the fake base station is located.
In addition to transmitting a mobile phone user's location and identifying information, data from text messages can easily be intercepted using an SMS server, without the user's mobile operator or the user themselves being any the wiser.
In March, Chinese authorities arrested a total of 1,530 suspects in a crackdown on spam text messages, and found that there were 3,540 cases of suspected crimes, with some of the scams run by gangs in various cities.
Users can also be tricked into subscribing to premium text messages by a malicious mobile app, whereby every time they receive the spam text message, they could be charged £1, for example, which adds up but is less noticeable as a single entry on a mobile phone bill.
China's Ministry of Public Security said that it had identified 3,540 cases of suspected crimes, including one case where a Liaoning Province gang is suspected of sending out over 200 million spam messages.
Who is using the fake base stations in the US?
In July, we reported that US police departments in various parts of the US, such as Florida, had been using a fake mobile base station product called StingRay to spy on US citizens without warrants since 2009, and that the US government had specifically requested that this knowledge be kept secret.

Some in the industry are pretty sure that these new fake base stations are not being run by a government intelligence agency like the NSA.
Cloud security firm SilverSky CTO/SVP Andrew Jaquith told VentureBeat: "The NSA doesn't need a fake tower [to tap your phone]. They can just go to the [mobile] carrier."
If Chinese gangs have been so successful in creating a business model where they spammed users' phones in order to obtain online banking details or to trick users into spending money on premium SMS text messages – perhaps criminals in the US are getting a clue?
Although the base stations could be being used by nefarious spies intent on intercepting calls and data from US citizens, it could just all be crime.
In any case, ComputerWorld pointed out a good way to know when you might be near a fake mobile base station – devices like StingRay only work on 2G networks, so in order to spy on users, the performance of your phone will instantly drop from 4G or 3G down to 2G as the device jams your phone signal.
So if you notice a sudden dramatic decrease in your mobile phone performance, maybe best to wait till you leave the particular geographic area you are in, before making a sensitive phone call.
© Copyright IBTimes 2024. All rights reserved.























