Is This how the FBI was Hacked?
A cyber security blogger has detailed one way in which the data from an FBI laptop could have been stolen by Anonymous hackers.
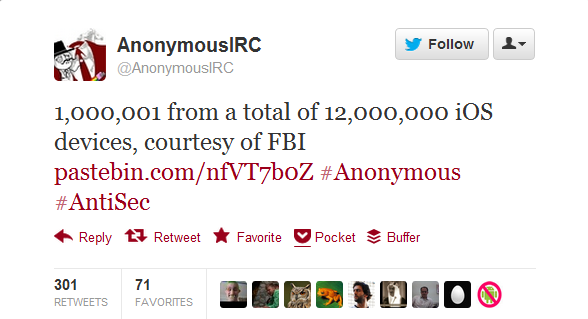
On Monday evening, Anonymous announced on Twitter that it had stolen a file from a laptop belonging to the FBI, which contained 12 million unique Apple device ID numbers - along with usernames, addresses and mobile phone numbers.
Anonymous also claims the FBI was using these Apple UDID numbers to track iPhone and iPad users.
The problem is that none of this is verifiable. There is no way of knowing where the data dumped online by Anonymous has come from.
AntiSec, the Anonymous off-shoot claiming responsibility for the breach, published 1,000,001 of the Apple IDs, but we don't know if it has any more. We also don't know if the file contained the additional information - like addresses or mobile phone numbers - as most of this information was redacted.
However, if (and it's a big IF) this information was taken from an FBI laptop, then one security blogger has detailed just how the AntiSec hackers could have got their hands on the information.
Robert David Graham, writing on the Errata Security blog, points to the fact that the hackers revealed they used a zero-day Java vulnerability to access the data. This was not the vulnerability which has been in the news in the past couple of weeks, but one which was being exploited in March 2012.
Hacked laptop
The hackers also said the data was stolen from a Dell Vostro laptop belonging to Supervisor Special Agent Christopher K. Stangl in the second week of March, which would seem to fit the timeline.
However to use this exploit, the hackers would have had to had the email address of this FBI agent, and probably a number of others. Luckily for them, this seems to have been the case.
Graham references to a law enforcement conference call which was intercepted by Anonymous hackers and released to the public on 3 February. This call was intercepted because the hackers had intercepted the email sent to 40 FBI agents from various part of the world telling them about the call.
This gave them not only the time and code for the conference call (letting them listen in and record what was being said), more importantly it gave them the names and email address of 40 law enforcement agents from around the globe who were tracking Anonymous, AntiSec and LulzSec.
Having a set of emails, the hackers would have set about a series of spear phishing attacks. These attacks see hackers, who know a specific email address for a known target, send emails which are tailored to reel in that target.
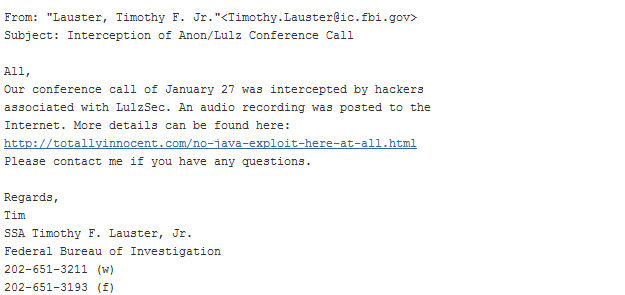
In this case, the email would have been related to the conference call and/or LulzSec and would have come from the same email address (something like the one above). The message would contain a link to a website hosting a Java app with the exploit which was being carried out at the time.
Once the hacker had infected the FBI agent's machine, then it would have been a matter of having a look around the PC to see what they could find.
Theory
Of course this is just one theory, and there are several others being postulated since the leaked Apple UDIDs were posted online. One theory being floated by a number of analysts and forum commentators is that the information contained in the AntiSec dump could have come from a hacked iOS developer account, which could have contained the same information.
Anonymous could then have added some specific-sounding details about the breach, such as the date, specific laptop and exploit name to make it all sound more convincing. The addition of the filename beginning with the acronym NCFTA, which refers to the National Cyber-Forensics Training Alliance adds a certain level of credence to the missive posted online.
Unless more information comes to light we won't know for sure where the hacking collective are telling the truth or not.
Anonymous has said it is not say anything more on the subject to journalists opn the matter - unless that is a strange caveat is fulfilled. That is, that a Gizmodo writer, normally critical of Anonymous, appears on his own website's homepage wearing a tutu.
As for the FBI, it is unsurprisingly remaining tight-lipped and is likely to do so until the whole thing blows over.
However, if there is any truth in the matter, then we suspect that Special Agent Stangl is in for a long holiday in Alaska.
© Copyright IBTimes 2025. All rights reserved.






















