Cyber-criminals Target UK Banks with Sophisticated Malware
Customers of a UK bank are being targeted by sophisticated cyber-criminals who go to great lengths to avoid detection.

Awareness levels regarding potential threats online are growing among the public, but according to security firm Trusteer, this is only spurring cyber-criminals to be more innovative in creating sophisticated malware which targets online banking services.
The company has uncovered a new malware targeting one UK bank in particular which presents its victims with false input fields, security warnings and customised text during the login process, account navigation and transactions.
This is done using a method called HTML injection and is so sophisticated that it will present customised and localised pages in various languages depending on where the victim is accessing the website from.
"This type of attention to detail takes a lot of time and effort on behalf of the malware authors, but it is a necessary evil if they want their fake pages to trick victims into believing they are legitimate," Trusteer said in a report.
The malware specifically targeting a UK bank is called Ramnit. It was first detected as a computer worm in January 2010, however in 2011 it was seen to have morphed into a piece of financial malware, or according to Trusteer, was at least being "used as a platform to commit financial fraud."
The malware stays idle until the user successfully logs into their account, at which time it presents them with one of the following messages:
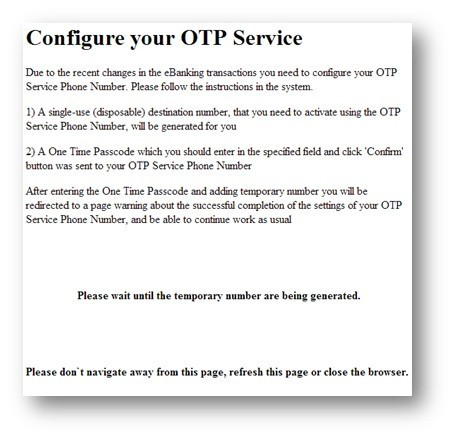
or
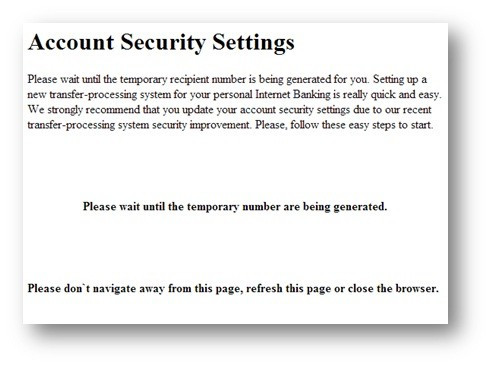
While the user is reading these messages, the malware connects to a remote server and obtains details of a designated "mule account." A transfer from the victim's account to the "mule account" is then initiated, all with out the
However in order for the transfer to proceed, the bank being targeted asks users for a One Time Password (OTP) which must be entered for the transaction to be completed.
To overcome this requirement Ramnit displays the following message:
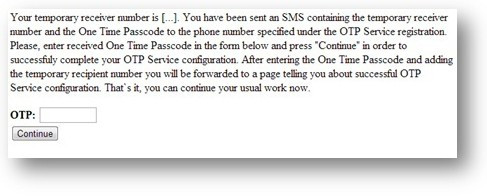
The "temporary receiver number" mentioned in the message is in fact the number of the "mule account." Having received a text message and thinking they must complete the "OTP service generation" the user enters their password and unknowingly enables the malware to complete the fraudulent transaction.
"This is yet another example of how well-designed social engineering techniques help streamline the fraud process," Trusteer said.
As we said at the beginning, greater user awareness around online security has forced cyber-criminals to be more innovative - and in this case they have been.
Should the request for the password raise questions among users, they may turn to the bank's FAQ page. However this is where the criminals have shown their attention to details. The authors of this malware took the extra step of altering the FAQ section to fit the new process.
They replaced the word 'transaction' with the word 'operation' to help reflect the use of the OTP in the fake "OTP service registration" process. While this was very clever, the simple find-and-replace process did lead to some grammatical errors as it failed to replce 'a' with 'an' in front of 'operation.'
© Copyright IBTimes 2025. All rights reserved.






















