The Evolution of the Botnet
Seen as one of the most powerful and effective tools used by cyber-criminals for over ten years, botnets are downsizing, becoming more numerous and more complex.

Infected computers in a botnet network are a little like Justin Bieber fans. They're everywhere, they don't even know they are infected, and they are at the bidding of some evil entity sitting in a darkened room cackling as he directs his army of zombie followers.
Willing to do just about anything their master asks of them, millions of infected PCs (Bieber fans) can be a powerful weapon which can earn their creators millions of pound every year.
For those of you who don't know, a botnet is a group of PCs infected with malicious software and controlled as a group without the owners' knowledge. They are controlled by cyber criminals who use these armies of PCs to do whatever they tell them to do.
They have been around for almost 15 years now and it is very likely that at some stage during that time one or more of your PCs has been part of a botnet. It's even possible that the computer you are reading this on is infected, as part of the power of botnets is that they remain under the radar of users and security vendors for as long as possible.
Botnets have been in the news recently for a couple of reasons. First was the good news of Microsoft and Symantec taking down the Batimal botnet which comprised up to eight million infected PCs.
Good news I hear you say. Indeed, but on a less positive note, earlier this week security companies reported they were once again monitoring Kelihos, a botnet which had already been disabled twice in recent years.
These two incidents only serve to highlight the evolution of botnets and how difficult it is for law enforcement agencies and security companies to identify and disable these powerful cyber weapons, which have evolved from very basic beginnings.
Some background
Botnets have been around for a long time. Since 1999 in fact, according to Rik Ferguson, VP of Security Research at Trend Micro, who charted the rise of the botnet back in 2010.
While early botnets were concerned with building on the functionality of what had gone before, it wasn't until 2003 that the criminal element decided to get involved, spotting the possibilities afford by a huge network of zombie PCs which would remotely bend to your will at the stroke of a key.
Early botnets focused on using the infected networks of PCs to send out billions of spam emails but as the complexity and sophistication of the malware infecting PCs grew, so did the scope of botnets.
Botnets are now used for crimes ranging from information theft to distributed denial of service (DDoS) attacks and much more. Up until March last year, Shadow Server Foundation was tracking around 6,000 unique command and control servers, which even then didn't represent all the botnets that were in operation at the time.
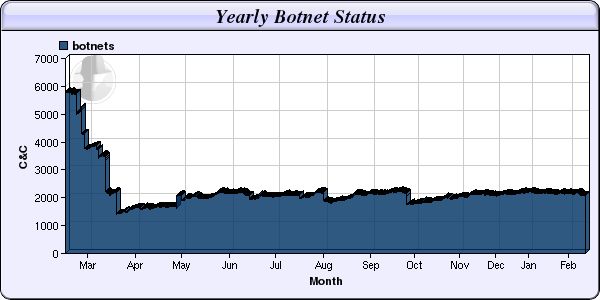
As you can see in the chart above, that figure plummeted at an extraordinary rate in March of 2012, which is the same time as Microsoft launched an attack on the Zeus family of botnets.
However as you can also see, since that takedown, the number of botnets in operation has slowly but steadily grown with currently over 2,000 command and control servers being tracked by the Foundation.
Current state of play
According to F-Secure's latest Threat Report, botnets resurfaced in 2012 with new packaging and different methods. "New business models like 'rent-a-botnet' schemes are flourishing, where cybercriminals rent a whole network of infected computers and use it to perform their attacks," the report adds.
According to the Finnish security company ZeroAccess was the fastest growing botnet last year, infecting millions of computers globally. Despite Microsoft's efforts Zeus, which is also a banking trojan, continues to reign, with the United States, Italy and Germany the most affected countries.
"Unfortunately, despite these commendable efforts, the botnets have been regularly resurrecting, often with new strategies or mechanisms for garnering profit. In addition, the operators running these botnets have been aggressively marketing their 'products' to other hackers and malware distributors," F-Secure said.
Microsoft continues its efforts to dismantle botnets around the globe with the Batimal takedown its sixth botnet disruption operation in three years
However Rik Ferguson believes that while efforts of private companies like Microsoft and security vendors are to be applauded, it simply isn't enough to stop cyber-criminals who look to be one step ahead at all times.
"Law enforcement and the security industry, working hand-in-hand with service providers makes life increasingly uncomfortable for criminals. That being said, by far the most effective means of disrupting criminal activity is to go after the people, rather than the infrastructure, meaning arrests, extraditions and jail time."
The problem with this plan however is that it is much more complex and can be a huge drain on man-power and other resources. However as the takedown of the Reveton ransomware gang proved this week, the approach is effective.
The future
While botnets like to remain under the radar, their sheer size means that security companies will eventually find them, and will result in them becoming targets for law enforcement agencies and security vendors. This is not what criminals want says Ferguson:
"In response to law enforcement and takedown activity in recent years, we don't expect to see the rise of very many truly huge botnets (think Storm, Conficker etc) in the future. From a criminal perspective, these are unnecessarily conspicuous and will attract unwanted attention in the form of takedowns."
So does that mean the demise of botnets? Not by a long way according to Ferguson, who says that botnets will evolve, become more dangerous and be even harder to detect:
"We are beginning to see more widespread implementations of peer-to-peer technology in modern botnets, or Domain Generation Algorithms to make the Command & Control infrastructure much more opaque. So in brief, more, smaller and more complex botnets seem to be the future."
What this means for you and me is that we are still under the same threat of being infected but by ten different smaller botnets rather than one big one.
The next untapped area for botnet creators is of course mobile, as smartphone sales boom and we increasingly carry around with us every single piece of personal digital information we own, from address books and contact numbers to pictures, emails and private documents.
However we are not going to see a wholesale shift from desktop botnets to mobile botnets any time soon, as criminals are too clever for that says Ferguson:
"[Mobile and desktop botnets] will co-exist for as long as the traditional computing environment and the mobile one continue to coexist. Online criminals can be extremely innovative in terms of technologies and methodologies, but they will always stay close to the target and close to the money."
The solution
Tackling a problem on such a huge scale is a daunting one. Not only do you face new botnets cropping up every week, but old one like Kelihos re-emerge and are given a new lease of life by cyber-criminals.
The solution, according to Ferguson lies in the combination of law enforcement agencies working closely with security experts.
"The most effective weapon remains law enforcement, supplied with intelligence from the security community. Greater harmonisation of international law, closer cooperation of law enforcement teams, more wide reaching international agreements and treaties and a significant up-skilling of police officers globally."
He also believes that vital information is being lost on a daily basis when people fail to report or ignore criminal activity:
"Too many crimes go unreported or ignored, any one of those could be offering a vital piece of intelligence that was not followed up."
Botnets, it seems, are here to stay, and are likely to be infecting PCs long after Justin Bieber and his army of fans are but a distant memory of a crazier time.
© Copyright IBTimes 2025. All rights reserved.






















