Flame Virus Update: UK Servers Used to Control Malware
Flame, the most complex piece of malware ever discovered, and which has been used to carry out cyber-espionage primarily in the Middle East, was controlled using servers in countries like the UK, Hong Kong and Switzerland over the last four years.
Following an investigation prompted by the International Telecommunications Union (ITU), Kaspersky Lab and CrySyS Lab in Hungary discovered the Flame virus, whose complexity exceeds all other known cyber menaces to date.
The primary purpose of Flame appears to be cyber espionage, by stealing information from infected machines. Such information is then sent to a network of command-and-control servers located in many different parts of the world.
A new update on the Flame virus from Kaspersky Lab, entitled The Roof is on Fire: Tackling Flame's C&C Servers reveals that several hours after the discovery was made public on 28 May, the Flame command-and-control (C&C) infrastructure, which had been operating for years, "went dark."
The C&C servers are used by the person/people in charge of a piece of malware like Flame to remotely instruct the computers infected with the virus. Flame can be used to steal valuable information, including, but not limited to, computer display contents, information about targeted systems, stored files, contact data and even audio conversations."
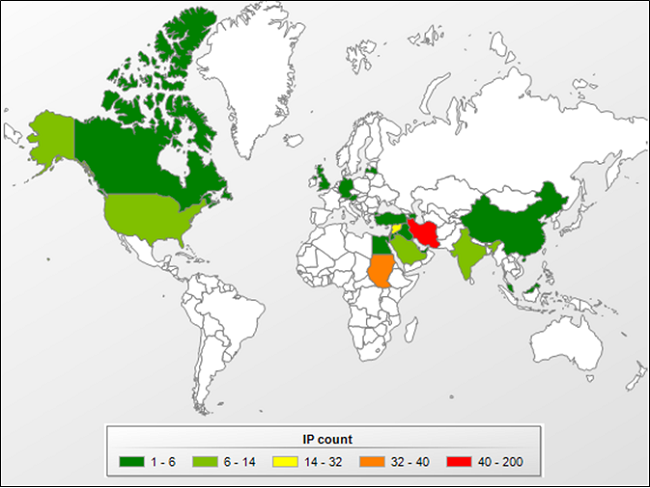
While C&C servers were located around the world, it appears as if systems infected by Flame were mostly located in the Middle East, though there were some infected systems around the globe, as you can see in the map below.
One of the most interesting findings of the Kaspersky Lab research so far is that Flame attacks on computer systems have shown a high level of interest in PDFs, Office documents and AutoCad drawings, which would indicate that the primary goal of the Flame malware was not to steal financial information.
Once those documents have been stolen they are uploaded to the remote C&C servers using relatively simple algorithms.
Kaspersky Lab has also found that the 64-bit version of Windows 7 is not affected by Flame and is therefore an effective method of protecting yourself from infection.
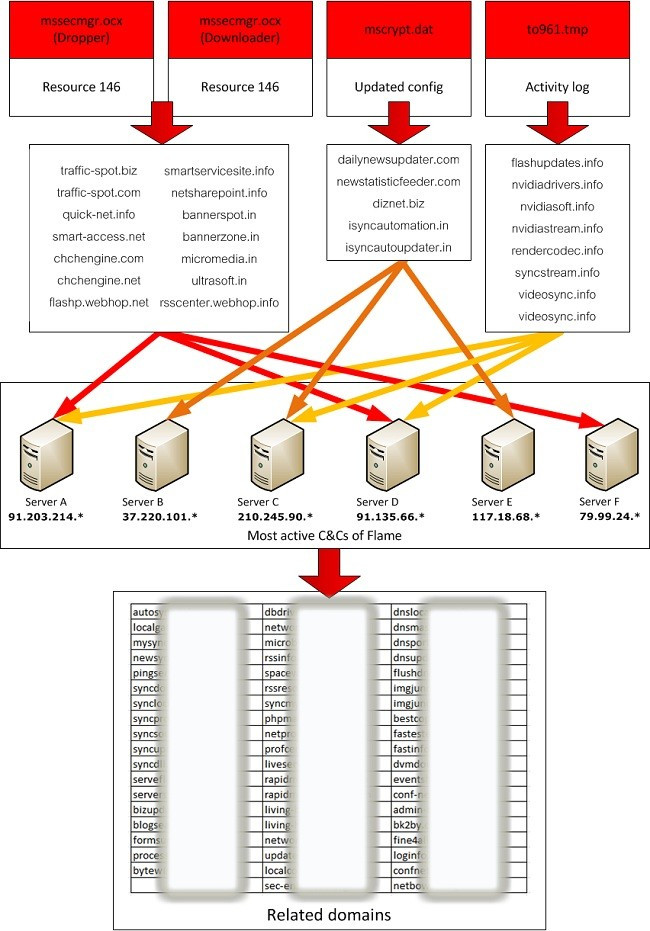
Currently there are more than 80 known domains used by Flame for C&C servers and its related domains, which have been registered between 2008 and 2012.
During the past four years, servers hosting the Flame C&C infrastructure moved between multiple locations, including Hong Kong, Turkey, Germany, Poland, Malaysia, Latvia, the United Kingdom and Switzerland.
According to Kaspersky Lab, "The Flame C&C domains were registered with an impressive list of fake identities and with a variety of registrars, going back as far as 2008."
Some of the fake identities used to register domains include names such as: Adrien Leroy, Arthur Vangen, George Wirtz, Gerard Caraty, Ivan Blix, Jerard Ree, Karel Schmid, Maria Weber, Mark Ploder, Mike Bassett, Paolo Calzaretta, Robert Fabous, Robert Wagmann, Romel Bottem, Ronald Dinter, Soma Mukhopadhyay, Stephane Borrail, Traian Lucescu, Werner Goetz or Will Ripmann.
Many of those forged identities had fake addresses in Germany and Austria, notably Vienna, however Kaspersky Lab is unsure why Vienna was an attractive choice for the attackers.
The large amount of forged identities and associated fake addresses confirms that Flame is one of the most complex cyber-warfare operations ever carried out. "The amount of domains and servers which were used in the Flame operation matches our previous opinion about the complexity of this malware."
One of the ways in which Flame spreads is by using a fake Windows Update program, signed by a fake Microsoft certificate. It uses the "Gadget" module within Flame to carry out this attack, but it should be noted that this way of spreading the malware can only take place within a network where one computer has been infected already.
Microsoft has issued a statement saying it is aware of the issue, and an update is available which blocks three known fake Flame digital certificates.
Vitaly Kamluk, Kaspersky's chief malware expert said following the discovery of the malware last week: "The geography of the targets and also the complexity of the threat leaves no doubt about it being a nation-state that sponsored the research that went into it."
This comes in the same week as it was revealed by New York Times journalist, David Sanger, that computer virus Stuxnet was part of a US and Israeli intelligence operation codenamed "Olympic Games", started under President George W. Bush and expanded under President Barack Obama, and aimed at spying on Iran's nuclear program.
The FBI has now launched an investigation looking into who might be behind the leaks, according to the Wall Street Journal.
Must Read:
© Copyright IBTimes 2025. All rights reserved.






















