Flame Virus is Most Complex Threat Ever Discovered [VIDEO]
A highly sophisticated and malicious computer virus whose complexity exceeds all other known cyber menaces to date, has been discovered and is actively being used as a cyber weapon attacking entities in several countries.
The malware, now known as Flame, was discovered by Kaspersky Lab's experts during an investigation prompted by the International Telecommunication Union (ITU), which is the UN agency for information and communication technologies.
The primary purpose of Flame appears to be cyber espionage, by stealing information from infected machines. Such information is then sent to a network of command-and-control servers located in many different parts of the world.
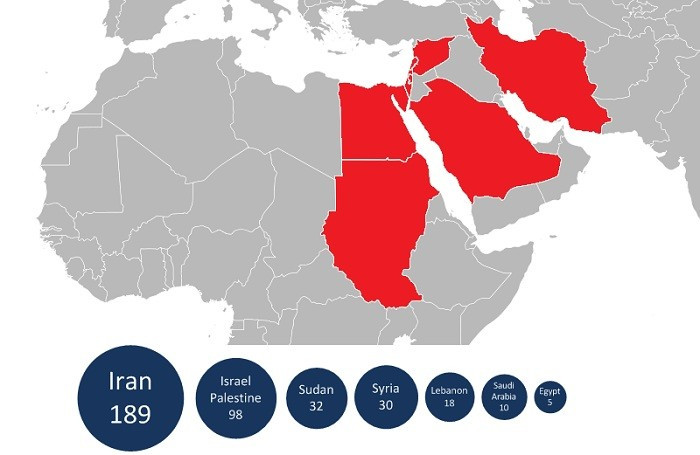
The Flame malware is currently affecting countries in the Middle East such as Iran, Israel, Sudan, Lebanon, Saudi Arabia and Egypt.
According to the experts at Kaspersky Labs, Flame can "steal valuable information, including but not limited to computer display contents, information about targeted systems, stored files, contact data and even audio conversations."
The Flame malware is not new however, and it is estimated that it has been in operation since March 2010, but such is the complexity of the malicious software plus the targeted nature of the attacks, that no security software detected it.
Flame will be the third major cyber weapon uncover following the discovery of the Stuxnet virus in 2010, which attacked Iran's nuclear program, and its data-stealing cousin Duqu, which was named after a villain in Star Wars.
Vitaly Kamluk, Kaspersky's chief malware expert, told the BBC that more than 600 specific targets were hit, ranging from individuals, businesses, academic institutions and government systems.
Kamluk said the size and sophistication of Flame suggested it was not the work of independent cybercriminals, and more likely to be government-backed. "Currently there are three known classes of players who develop malware and spyware: hacktivists, cybercriminals and nation states."
"The geography of the targets and also the complexity of the threat leaves no doubt about it being a nation-state that sponsored the research that went into it," Kamluk added.
"Flame is not designed to steal money from bank accounts. It is also different from rather simple hack tools and malware used by the hacktivists. So by excluding cybercriminals and hacktivists, we come to conclusion that it most likely belongs to the third group."
The fact the virus has gone undetected for so long has also promted some to speculate that there could be a lot more similar viruses out there. Roel Schouwenberg, Kaspersky Lab senior security researcher, told Reuters: "If Flame went on undiscovered for five years, the only logical conclusion is that there are other operations ongoing that we don't know about."
Alexander Gostev, Chief Security Expert at Kaspersky Lab, commented: "The preliminary findings of the research, conducted upon an urgent request from ITU, confirm the highly targeted nature of this malicious program. One of the most alarming facts is that the Flame cyber-attack campaign is currently in its active phase, and its operator is consistently surveilling infected systems, collecting information and targeting new systems to accomplish its unknown goals."
Kaspersky Labs were initially seeking information on a program which was deleting sensitive information across the Middle East. While searching for that code - nicknamed Wiper - the security team discovered a new malware codenamed Worm.Win32.Flame.
Eugene Kaspersky, who IBTimes UK spoke to recently about cyber security, tweeted that it took his company six months to analyse the Stuxnet worm but the Flame virus is 20 times more complicated.
Kaspersky added: "The Flame malware looks to be another phase in this war, and it's important to understand that such cyber weapons can easily be used against any country. Unlike with conventional warfare, the more developed countries are actually the most vulnerable in this case."

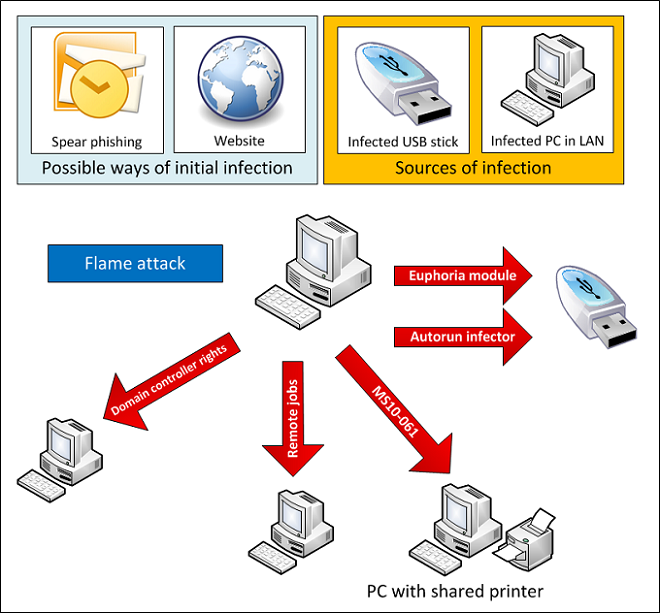
The initial point of entry to any system is unknown so far, but once a system is infected, Flame begins a complex set of operations, including monitoring the network traffic, taking screenshots, recording audio conversations, intercepting the keyboard, and so on. All this data is available to the operators through the link to Flame's command-and-control servers.
Prof Alan Woodward, from the Department of Computing at the University of Surrey, told the BBC, the attack is very significant: "This is basically an industrial vacuum cleaner for sensitive information," he told the BBC.
Prof Woodward agreed with Eugene Kaspersky when describing the complexity of Flame in comparison to Stuxnet: "Whereas Stuxnet just had one purpose in life, Flame is a toolkit, so they can go after just about everything they can get their hands on."
Kaspersky Labs has written an FAQ about the Flame malware giving a lot more detail of how it works and where it originated.
© Copyright IBTimes 2025. All rights reserved.






















