iOS 5.1.1 Fixes Serious Security Issues
The rise of mobile malware is one of the hot topics among security experts these days, and this has been shown to be the case once again with the release of iOS 5.1.1, which patches at least three serious security flaws.
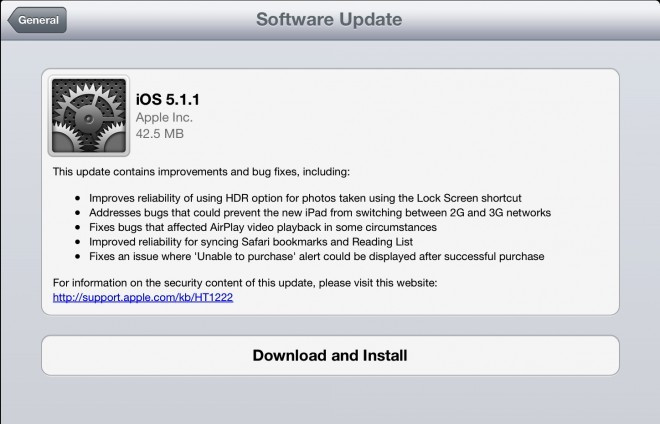
iOS 5.1.1 began rolling out on Monday for iPhone, iPad and iPod touch users, and while Apple was playing up its improved HDR photography features and the improved reliability for syncing Safari bookmarks with Reading List, there were much more important updates included with iOS 5.1.1.
While the landing page of the update doesn't go into the security content of the page, you will be able to get the details, with a little digging, on a page called HT5278.
The three main security problems fixed with the update have been detailed on the Naked Security Blog by Paul Ducklin, head of technology for security firm Sophos.
The first issue, called address bar spoofing, allows website X to direct you to website Y, while appearing as if you have been sent to website Z. This flaw allows for scammers, phishing schemes and peddlers of malware to appear to be legitimate websites in order to fool iDevice users.
The second flaw which has been fixed with the update is something called cross-site scripting, or XSS for short. When you visit a website, in theory only code from that site should be allowed to be executed, while content from a second site should only have access to your cookies or browsing history.
But with XSS a crook in control of one website may be able to recover session authentication data (password, username etc.) from another site, and use this to impersonate you online.
The final serious security flaw fixed by iOS 5.1.1 is remote code execution, which means that a maliciously crafted website might crash your browser in such a way that it ends up running program code secretly embedded in the page.
The normal procedure when some executable machine code is served up by an untrusted website is to see several dialogue boxes popping up to ask if you really want to run this code. This means such malicious code should never get near your device's CPU.
However, until now, there have been some exploitable remote code execution vulnerabilities in iOS, letting people sneak malware onto your phone or tablet without you knowing about it. This is very similar to the way the recent Flaskback Trojan managed to infect hundreds of thousands of Macs.
iOS and Apple are seen by most people as a lot safer from malware attacks than other operating systems' manufacturer ecosystems.
In a recent survey to establish which mobile phone operating systems are the most vulnerable, iOs was found to be more secure than Android and Windows Phone 7, but was significantly behind RIM's BlackBerry in terms of security.
In a recent interview with IBTimes UK, security analyst Rik Ferguson said: "There is no [criminal] malware whatsoever that would affect a non-jailbroken iPhone. The fact is, when you jailbreak a device, you disable some very key security mechanisms."
Security researcher Charlie Miller did manage to bypass Apple security and get an app into the official App Store which exploited a security flaw, but Apple fixed this vulnerability in a previous software update, showing that threats continue to crop up on Apple's platform.
The iOS 5.1.1 update is now available to download and works with the iPhone 3GS, iPhone 4, iPhone 4S, iPad 2, iPad, iPod touch, (third and fourth generations).
Apple lists the improvements and bug fixes as follows:
- Improves the reliability of the HDR photography option when shooting photos using the Lock Screen shortcut.
- Addresses bugs that could prevent the new iPad from switching between 2G and 3G networks.
- Fixes bugs affecting AirPlay video playback.
- Provides improved reliability for syncing Safari bookmarks and Reading List.
- Fixes an issue where an "Unable to purchase" alert is displayed after successful purchase.
© Copyright IBTimes 2025. All rights reserved.






















