iOS: Over 1,000 apps that use JSPatch technology put users at risk

More than 1,000 iOS apps in the App Store that use a framework could allow attackers to carry out powerful actions on a compromised device without the user's consent. The framework, known as JSPatch, is an open source project that allows developers to apply hot fix on apps for several bugs, while bypassing Apple's review process for updated apps.
The app review process for a bug fix takes at least seven days before the updated code is approved. While developers seek methods to bypass the waiting period, it puts users at risk.
The security flaw in the framework could allow attackers to access photos, microphone, clipboard and other features. According to cybersecurity firm FireEye, as many as 1,220 apps in the App Store utilise JSPatch. Although it failed to name the apps, it claims that it has already notified the app provider. While JSPatch is a useful technology for iOS development, if exploited, it could pose a big risk to users.
JSPatch framework
Originating from China, JSPatch has tasted success in the Chinese market since its release in 2015. Scores of popular and high-profile Chinese apps have adopted the technology. FireEye has found that developers outside China have also adopted the framework.
It allows attackers to effectively circumvent the protection given by the App Store review process and perform arbitrary and powerful actions on the compromised device, notes the firm. The code for the framework makes it quite difficult to catch any malicious action.
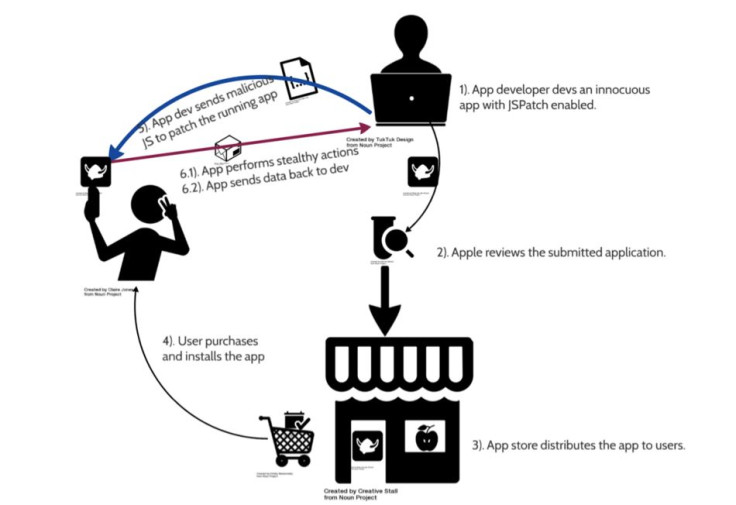
"JSPatch is a boon to iOS developers. In the right hands, it can be used to quickly and effectively deploy patches and code updates. But in a non-utopian world like ours, we need to assume that bad actors will leverage this technology for unintended purposes. Specifically, if an attacker is able to tamper with the content of JavaScript file that is eventually loaded by the app, a range of attacks can be successfully performed against an App Store application," states a blog post on FireEye.
According to the cybersecurity firm, JSPatch is one of several offerings that provide a low-cost patching process for iOS developers. Other similar offerings are also seen as vulnerable to exploitation.
How to avoid the vulnerability
Speaking to the Telegraph, Josh Goldfarb, who heads emerging technologies at FireEye, said: "A sly attacker could write a legitimate, non-malicious app using this framework and — once it gets through the Apple process — use it to send non-legitimate, malicious instructions to the device."
He also offered some security advice to iOS users. "The recommendations are pretty standard: only download applications that you need, that you know, and that you trust. Beware of apps that ask for an extensive amount of permissions - and only give it those that are necessary," Goldfarb added.
This is not the first time iOS users are facing vulnerability. In October 2015, SourceDNA found that hundreds of iOS apps were collecting the user's private data while violating Apple's security and privacy guidelines. The discovery came just a month after the XcodeGhost malware attack on the App Store.
While explaining the vulnerability of mobile phones, Goldfarb said: "Mobile devices are an attractive target for attackers, because they're relatively poorly protected compared to laptops and desktops. We're going to start seeing a lot more activity in this environment. Attackers go where the money is — so we're going to see a lot more targeting of mobile."
© Copyright IBTimes 2025. All rights reserved.





















