6.5 Million LinkedIn Passwords 'Leaked' Online
A report on a Norwegian website suggests that 6.5 million hashed and encrypted passwords from LinkedIn accounts have been leaked online.

Under the headline Change Passwords on LinkedIn, Now! the Dagensit website suggests that a package of 6.5m encrypted passwords were posted on a Russian hacker website up to two days ago. Those who posted the passwords on the site were looking for help to crack the codes, which is a fairly common occurrence in the world of cybercrime.
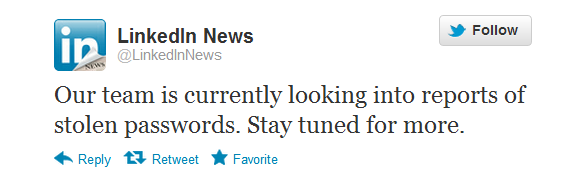
In response to these reports, LinkedIn has said on Twitter that it is "currently looking into reports of stolen passwords. Stay tuned for more."
Two hours later the social network added in another tweet: "Our team continues to investigate, but at this time, we're still unable to confirm that any security breach has occurred. Stay tuned here."
While no user details have been posted online, it is believed those behind the attack will have had access to this data. Finnish security firm CERT-FI, said in a post: "All users password seals have not been published, but it is likely that a burglar is in possession of the rest of the seals." [via Google Translate].
Only 5 percent of the passwords stolen have so far been cracked according to reports, but many more are likely to be uncovered as long as the hashed passwords remain online.
LinkedIn is a professional social networking website founded in December 2002 and launched in May 2003, it is mainly used for professional networking and as of 9 February 2012, LinkedIn reports more than 150 million registered users in more than 200 countries. This means only a small percentage of the total user base is vulnerable, however it is the negative press which this leak will bring with it that will cause the real damage.
A security expert with Finnish company F-Secure, Mikko Hypponen, gave some advice to those worried about the breach: "First change your LinkedIn password. Then prepare for scam emails about Linkedin password changes, linking to phishing sites. Will happen."
Hypponen also posted some of the allegedly leaked LinkedIn passwords, which shows that many people were not very creative when creating their passwords: nathanlinkedin, linkedintrouble, hondalinkedin, eaglelinkedin, springlinkedi.
Earlier today it had been reported that LinkedIn's iOS app collects full meeting notes and details from you device's calendar and sends them back to the company in plain text. This is able to take place without the express permission of the user, thanks to a feature of the app which lets you access your calendar from within the app.
LinkedIn has responded to this in a detailed blog post, saying: "We deeply care about our members trust so I want to provide clarity around what we do, don't do, and outline ways we are going to make a great feature even better."
The company says it does ask permission before accessing your calendar, and that this will continue to be an opt-in feature, adding that it doesn't store any calendar information on its servers.
In a bid to appease angry users, LinkedIn says it will no longer send data from the meeting notes section of your calendar event and there will be a new "learn more" link to provide more information about how your calendar data is being used.
© Copyright IBTimes 2025. All rights reserved.





















