Smartphone Malware Secretly Creates 3D Models of Your Surroundings
A university experiment has proven that mobile malware can be used by your smartphone to remotely map the interior of your house or office.

Until now, the idea that your smartphone's camera could be used to secretly build a 3D model of your home or office, upload the data to a remote server, and allow them to virtually snoop around your home, was the preserve of works of science fiction and fantasy.
However researchers at the School of Informatics and Computing at Indiana University have shown that this is, in fact, a reality, and have created a simple camera app for the Android platform which criminals could use to remotely burgle your home or office.
In a paper titled PlaceRaider: Virtual Theft in Physical Spaces with Smartphones, the researchers outline how a simple app called PlaceRaider can take dozens of photos every minute on your smartphone, analyse these along with data from the phone's other sensors and upload them to a remote server.
These images, along with location and orientation data from the phone's accelerometer and gyroscope are then used to construct a 3D model of the victims' environment, allowing virtual theft of sensitive, personal data such as bank account details, passwords and other personally identifiable information - without ever stepping inside your home.
So-called "sensor malware" has been gaining popularity on the Android platform over the past year and researchers recently demonstrated how malware can be used to "listen" for spoken credit card numbers using the microphone.
The researchers tested the app using 20 students who were unaware the malicious app was running on their smartphones. There were capturing data from an office environment and following analysis of the data, it was shown that "faithful 3D models of a space can often be generated from opportunistically captured images."
Main functions
The App has three main functions: to monitor orientation sensor data, to capture images, and to select a subset of images likely to contain valuable information for constructing a 3D model.
In order to remain below the radar of the user, the app requires a number of permissions when being downloaded. These include permission to access the camera, to write to external storage, and to connect to the network. However these are all permissions a legitimate camera app would normally ask for, therefore few suspicions would be raised when downloading PlaceRaider.
One other permission is required by PlaceRaider - to change audio settings in order to capture photos without making an audible "shutter" sound. This too can be circumvented however, for example by advertising it as a feature allowing the user to continue to listen to music through an unrelated app without the interruption of the shutter sound.
Even if these permissions did arouse suspicion if read carefully, it has been shown that the majority of Android users disregard permissions when downloading an app anyway.
Reconnaissance

Once the PlaceRaider app has been downloaded to your phone, it begins its reconnaissance work silently in the background without alerting the user to what is going on. In the tests carried out at Indiana University, the researchers set the camera to capture an image every two seconds.
Capturing full-size images at this frequency on a smartphone with an 8 megapixel camera would quickly begin to arouse suspicion however, as the phone's memory would soon fill up.
In order to avoid this, the researchers set the camera to capture images of just 1 megapixel in size. To further reduce the number of images which have to be uploaded, the PlaceRaider app employs sophisticated algorithms based on a measure of an image's anisotropy, to select only a few of the captured images for uploading.
Because images are taken surreptitiously and opportunistically, a large majority of the images are likely to be either of very low quality (such as completely dark photos while the phone is resting on a desk, or very blurry images when the phone is moving rapidly) or to be redundant - many duplicated pictures of exactly the same static scene.
Algorithms
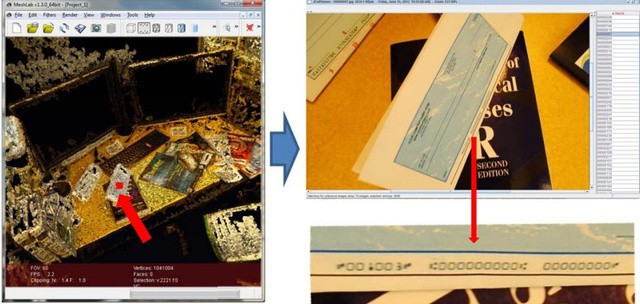
The algorithms employed allows for the majority of captured images to be deleted and only those with important information to be uploaded to the remote server.
Once the images and sensor data have been uploaded, the attackers can then create 3D models of the home or office environment, allowing them to virtually snoop around and identify any information of a sensitive nature.
While smartphones are currently not powerful enough to render these 3D images themselves, the researchers say this will be possible in the future.
Among the data which could be available are bank statements, cheque books, passwords, calendars telling the attackers when the victim will be out of the house, and a lot of other financial and personal information.
While this app was only created as a proof-of-concept, it highlights how the powerful features of today's smartphones could be leveraged by cyber criminals to steal your private data - even if it's not stored on your device.
Looking at ways of preventing this type of malware propagating, the researchers suggest a number of methods of limiting access to your phone's features.
Among the methods of securing the platform include enabling a persistent shutter sound to highlight when images are being taken; enabling permissions for sensors, something which is currently not enabled on Android or iOS; and finally suggesting that users should pay more attention to the permissions they are giving apps they download.
© Copyright IBTimes 2025. All rights reserved.






















