‘Red October’ Cyber Attack Discovered Targeting Governments
A piece of espionage malware known as Rocra or Red October, which secretly gathers highly-classified and sensitive information from governments has been discovered, five years after it began operating.
Compared to Flame in terms of its complexity, Red October is a piece of cyber-espionage malware which targets diplomats, government employees and scientific research organisations, mostly based in eastern Europe.
Red October was first uncovered by Kaspersky Labs back in October 2012, following a tip off from an anonymous source. Since then the Russian-based security firm has been investigating this complex malware, and through analysis of registration data used to purchase the command and control (C&C) servers, it has estimated the malware could date back as far as 2007.
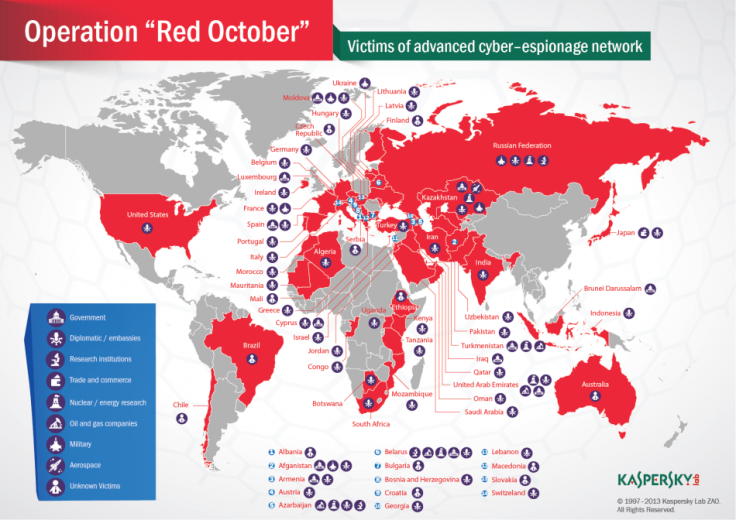
Red October has infected hundreds of users around the world in eight main categories: government, diplomatic, research institutes, trade and commerce, nuclear research, oil and gas companies, aerospace and military.
The amount of highly sensitive data stolen is estimated to be huge, with Kaspersky saying that over the past five years it would amount to around five terabytes of information.
While most of the infected computers identified since October come from eastern Europe, with the Russian Federation leading the infection list, there have also been infections found in countries like India, the US, Italy and Switzerland. In total there are victims in 39 different countries.
Addressing the question of who is behind the attack, Kaspersky Labs said no specific location has been identified by the data collected so far. However it does point out that the exploits appear to have been created by Chinese hackers and the Rocra malware modules have been created by Russian-speaking operatives.
Unlike Flame, which was immediately identified as a state-sponsored attack, there is currently no evidence linking Red October to any nation-state. However, Kaspersky Labs do note: "The information stolen by the attackers is obviously of the highest level and includes geopolitical data which can be used by nation states. Such information could be traded in the underground and sold to the highest bidder, which can be of course, anywhere."
Targets
The malware not only targets workstations but also mobile devices like smartphones and tablets, as well as networking gear to give them better access to organisations. Once established within a network, the attackers stole everything from files on desktops, smartphones and FTP servers, to email databases using exploits developed in China and Russian malware, Kaspersky researchers said.
Information harvested in earlier attacks has been reused in later attacks, for example stolen credentials were compiled in a list and used when the attackers needed to guess passwords and network credentials in other locations.
The scale of the Red October malware is enormous, with more than 60 domain names and several server hosting locations in different countries (mainly Germany and Russia). The Command & Control server infrastructure is actually a chain of servers working as proxies in order to hide the location of the main "mothership" server.
The first stage of the attack sees a spear-phishing email campaign targeting specific people within the organisation. These emails contain a file using known exploits in Microsoft Word and Excel. The documents are tailored for specific victims and the malware modules have specific victim ID numbers, Kaspersky said.
Once the file is downloaded and opened, the Trojan is dropped on the machine, which in turn scans the network for other machines vulnerable to a security flaw in Windows - a vulnerability which was also used by the infamous Conficker worm.
"During the past five years, the attackers collected information from hundreds of high profile victims although it's unknown how the information was used. It is possible that the information was sold on the black market, or used directly," Kaspersky said in its report.
While it compared Rocra to Flame in terms of complexity, Kaspersky said it could not find any link between the two pieces of malware.
© Copyright IBTimes 2025. All rights reserved.






















