RedTube porn website hacked to spread malware to visitors
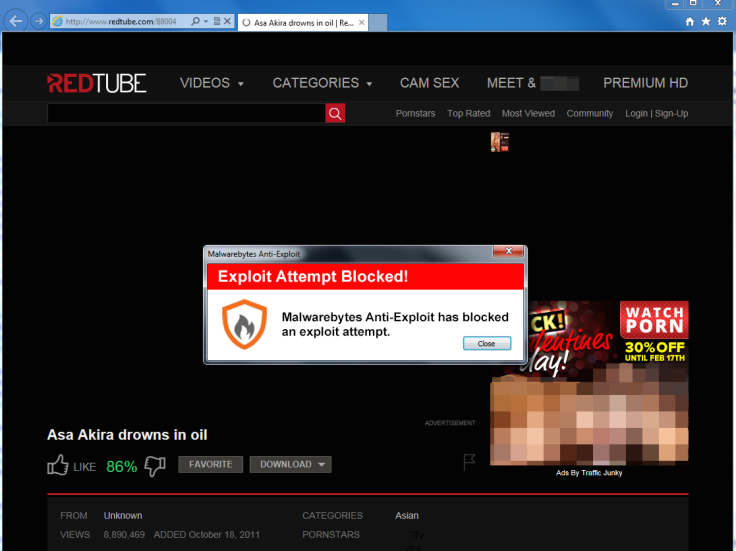
RedTube, the popular adult video website with 300 million monthly visitors, was hacked to redirect users to a malicious website which attempted to install malware on the victim's computer.
According to a blog post by security company Malwarebytes, which last month revealed that xHamster was subject to a malvertising campaign, visitors to RedTube.com were automatically redirected to a malicious website which hosted a piece of malware that was downloaded to victims' computers which could allow the attackers to steal their personal information.
RedTube is ranked as the 128th most popular website according to website monitoring service Alexa.
Source code
Unlike the malvertising attack on xHamster, the hackers who compromised RedTube.com were able to breach infrastructure which the website runs on letting them install an iFrame which was invisible to users:
Malwarebytes said:
The existence of the iFrame in the main page source code is evidence enough to say that RedTube servers were likely hacked by malicious actors who had access to the main page source code, adding the malicious code and then setting it loose on RedTube users.
The malicious website you are redirected to will use the increasingly popular Angler Exploit Kit to drop a piece of malware onto your system taking advantage of vulnerabilities in Adobe's Flash software.
The malware the exploit kit drops is part of what is known as the Kazy Trojan family, which the security company says is known "for stealing personal information from users as well as installing browser helper objects that spread pop-up ads, some redirecting to additional exploit pages and therefore more malware infections".
RedTube confirmed that its security was breached on Sunday, 15 February but the adult website has now addressed the issue to remove the malicious code.
IBTimes UK has contacted RedTube to find out how long the website was compromised, how many users were affected and how the attackers managed to gain access to the system, but at the time of publication we have not had a response.
© Copyright IBTimes 2025. All rights reserved.






















