Russian hackers hijacking satellite internet links to hide Turla cyber espionage data siphoning

Security researchers have discovered that a Russian cyber espionage group has been hijacking satellite-based internet links to hide their activities, which include stealing information from diplomats and government agencies around the world.
According to security firm Kaspersky Lab, a sophisticated group of hackers from Russia called 'Turla' has been quietly using satellite-based internet links to conduct their business, as it is much easier to avoid detection.
Cyber espionage groups
When it comes to hackers, there are several types. Some are in it for the money like notorious spam king Sanford Wallace, some are in it for political activism like Anonymous, and then there are the state-sponsored hackers who attack other countries for government agencies like the NSA.
One such example of state hacking is Turla, a Russian-speaking group that has been in operation for almost a decade, running advanced persistent threat (APT) attacks that covertly target specific organisations, nations and businesses using command-and-control systems to monitor and slowly extract data from the target.
Often, this is achieved by infecting computers with malware that can perform a myriad of functions, including exploiting undisclosed zero-day security flaws to find a backdoor into a network, cracking administrator passwords, or spear phishing, where emails masquerading as a reputable bank or online service trick users into putting in their account passwords and credit card details.
Of course, internet service providers (ISPs), security agencies and law enforcement are on high alert for hacking activity, and are constantly seizing and shutting down the servers and domains needed for command-and-control systems, so cyber-criminals need to find another way to stay afloat.
Satellite internet is cheap and not encrypted
Although satellite-based internet is slow, it is easy to hack into and abuse since these connections are not encrypted, and maintaining hijacked downstream internet access links costs only $1,000 (£650) a year, as opposed to paying for it legitimately at the cost of up to $7,000 a week, according to Kaspersky.
At the moment, Turla is primarily targeting satellites and IP addresses belonging to satellite internet providers in Middle Eastern and African countries such as Lebanon, Libya, UAE, Somalia, Nigeria, Congo and Niger.
Kaspersky tracked the IP addresses back to command-and-control servers owned by Turla, and they noted that the hijacked satellite IP addresses belonged to the following companies: Telesat, Teleskies, Skylinks Satellite Communications Limited, Lunasat, Emperion, SkyVision Global Networks, Orioncom, Intrasky, IABG mbH and Sky Power International.
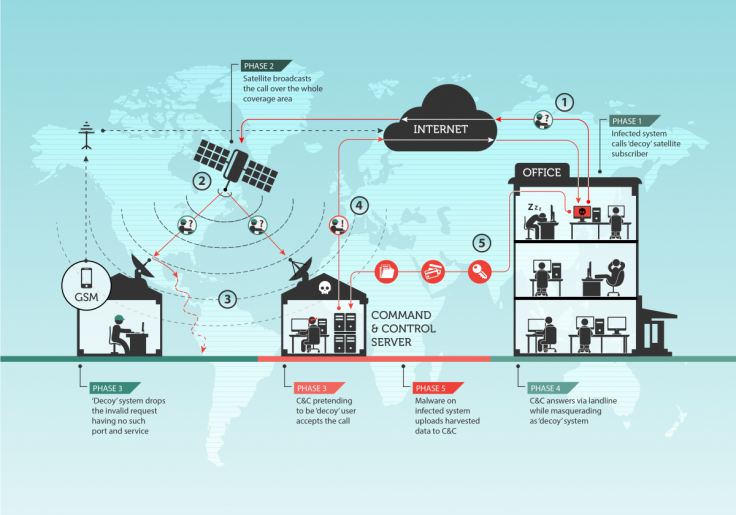
"The regular usage of satellite-based Internet links by the Turla group represents an interesting aspect of their operation. The links are generally up for several months, but never for too long. It is unknown if this is due to operational security limitations self-imposed by the group or because of shutdown by other parties due to malicious behaviour," Stefan Tanase, a senior security researcher with Kaspersky Lab, wrote in the blog post.
"Considering how easy and cheap this method is, it is surprising that we have not seen more APT groups using it. It should be noted that Turla is not the only APT group that has used satellite-based internet links. HackingTeam C&Cs were seen on satellite IPs before, as well as C&Cs from the Xumuxu group and, more recently the Rocket Kitten APT group.
"If this method becomes widespread between APT groups or worse, cyber-criminal groups, this will pose a serious problem for the IT security and counter-intelligence communities."
© Copyright IBTimes 2025. All rights reserved.





















