Home
> hackers
hackers
Lazarus: North Korean hackers linked to Sony hack were behind cryptocurrency attacks in South Korea
North Korean hackers have increasingly targeted cryptocurrency firms and users to generate funds for a country squeezed by sanctions and trade restrictions.
Triton malware: Next-gen cyberweapon that can shut down power plants accidentally leaked online
The malware is believed to have been created by a nation-state and has reportedly been publicly available online for nearly a month.
Hospital pays $55,000 in bitcoin to hackers after 'SamSam' ransomware locks systems
A US hospital has paid hackers $55,000 (£39,900) to restore control of its computer systems after they were infected with a strain of ransomware known as "SamSam".
Smoke Loader: Fake Meltdown and Spectre patches found infecting PCs with malicious new malware
Researchers say hackers are constantly looking to exploit anxious users, particularly during widely publicised events such as the recently disclosed Meltdown and Spectre flaws.
What is RubyMiner? New malware found targeting Windows and Linux servers to mine cryptocurrency
The latest attacks come as hackers increasingly target cryptocurrency using various nefarious methods amid the growing popularity and value of virtual currency.
BitTorrent critical flaw allows hackers to remotely control users' computers
The critical vulnerability in the popular Transmission BitTorrent app was exposed by Google Project Zero researchers.
BlackWallet hacked: Over $400,000 in cryptocurrency stolen after hackers hijack DNS server
This isn't the first time hackers have targeted crypto-related businesses and exchanges in recent months.
Hackers hijack Twitter account of India's top diplomat to post photos of Pakistan's flag
"We will show you the power of the Turk!" the hackers tweeted from the compromised accounts.
What is Teligram? Fake Telegram app found serving up malware and ads on Google Play Store
"The only differences, at least at first glance, are the misspelling of Telegram," security researchers warned.
What is OSX MaMi? New undetectable Mac malware can hijack DNS settings, steal users' personal data
OSX MaMi is a DNS hijacker but also features a slew of other malicious capabilities, security researchers said.
New Zealand Football website hacked with fake news of CEO Andy Martin's resignation
The fake article appeared on the All Whites' official website claiming his resignation was effective immediately.
First Android malware written in Kotlin found posing as Swift Cleaner app and stealing user data
The data-stealing malware is also capable of performing click ad frauds, remote command execution, sending SMS and more.
WhatsApp security flaws could let uninvited guests slip into your private group chats
Researchers presented their findings at the Real World Cryptosecurity conference in Zurich.
What is FakeBank? New banking malware can intercept SMS messages to steal sensitive data and funds
The malicious banking malware has been spotted targeting users in Russia and other Russian-speaking countries.
MacOS High Sierra security bug lets you unlock App Store System Preferences with any random password
"We greatly regret this error and we apologise to all Mac users," Apple said in a statement.
Watch out for this Netflix phishing scam that will steal your credit card details
Netflix users are being warned to avoid clicking on suspicious email links after a phishing scam was uncovered that security experts say is designed to steal credit card details.
Fancy Bear: Alleged Russian hackers leak 'emails and documents' from Olympic body
A Twitter profile linked to suspected Russian hackers, which last year pushed out stolen health documents of Olympic athletes, resurfaced on Wednesday - leaking files.
Russia-linked Turla hackers using Adobe Flash update to drop malware, steal data from embassies
The group has been using this attack technique in campaigns since at least July 2016, ESET researchers said.
Hackers exploit critical Oracle WebLogic flaw to secretly mine cryptocurrency worldwide
The attacks are thought to have begun after a security researcher published a proof-of-concept exploit in December.
Microsoft suspends Meltdown and Spectre patches for AMD after PCs suffer 'blue screen of death'
The Meltdown and Spectre flaws affect nearly every modern processor and impact a range of devices such as computers, smartphones, tablets and servers.
Twitter promotes 'get verified' phishing scam that actually steals your account, credit card details
Although Twitter is no stranger to phishing scams, the latest incident does highlight serious flaws in Twitter's ad approval system.
What is CoffeeMiner? New attack lets hackers hijack public WiFi networks to mine cryptocurrency
Researcher Arnau Code said he has already successfully tested the CoffeeMiner attack in real-life scenarios including in cafes.
Malware found mining cryptocurrency and secretly sending coins to a North Korean university
"It's not clear if we're looking at an early test of an attack, or part of a 'legitimate' mining operation," researchers said.
Florida hack exposes 30,000 Medicaid patients' confidential records, medical conditions and diagnoses
Florida's AHCA said one of its employees fell victim to a "malicious phishing email" late last year.
Hackers target Ukrainian software company to spread the notorious Zeus banking trojan
Since the source code for version 2.0.8.9 of the ZeuS trojan was leaked in 2011, other threat actors have taken inspiration from the malicious code.
Watch out for this new Android malware that poses as Uber to steal passwords
Android users should be on alert for a new malware variant posing as ride hailing app Uber in an attempt to steal passwords, security researchers warn.
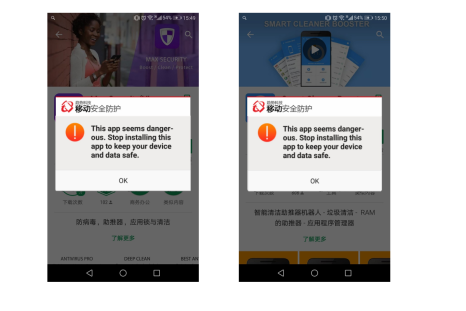
36 fake security apps harvesting user data and tracking their location found in Google Play Store
Users are even asked to sign and agree to an end-user licence agreement (EULA) that describes the information to be gathered and used by the app.
Trackmageddon: Flaws in hundreds of GPS services risk exposing millions of devices' data to hackers
The vulnerable GPS services are exposing location data, phone numbers, device model, IMEI numbers, photos and more.
Hackers have posted the malware code behind Satori botnet for free on Pastebin
"When an IoT exploit becomes freely available, it hardly takes much time for threat actors to up their arsenal," NewSky Security warned.
MacOS zero-day: 15-year-old Apple root access bug was publicly released on the last day of 2017
The zero-day vulnerability is a local privilege escalation (LPE) flaw and can only be exploited when the attacker has local access to the targeted device.