Stash of Two Million Facebook and Twitter Passwords Discovered Online
A trove of two million stolen passwords for Facebook, Twitter, email and other online services has been discovered by cyber security researchers.

Unearthed by Trustwave and detailed on its blog, the collection of stolen data contains 1.5 million website login credentials for sites like Facebook, 320,000 email account credentials, and 3,000 remote desktop login details, among others.
Researchers gained access to a server controlling an instance of the malicious Pony botnet, a piece of malware which infects users' computers then records the victim's usernames and passwords, which are returned to the cyber criminal and either used or sold on to others.
Most of the compromised login details belong to Facebook, Google, Yahoo, Twitter and LinkedIn accounts, and - as is becoming increasingly common during such data thefts - the most commonly used passwords are the easiest to guess.
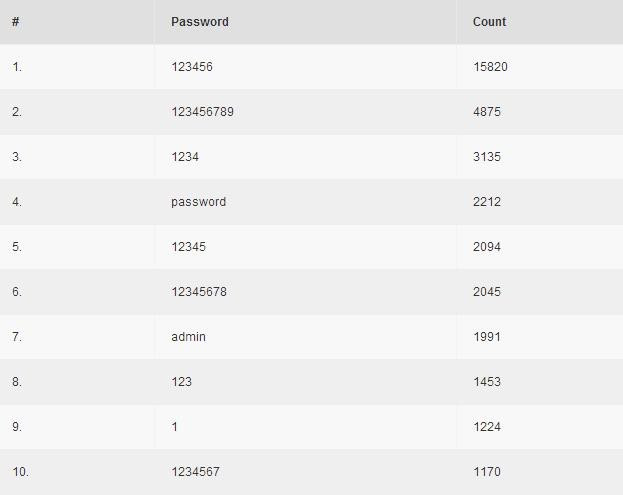
The most common password of the two million stolen was '123456', while '123456789' was second and '1234' was the third most popular password; other examples to feature in the top ten include 'password', 'admin' and '1'.
Worringly predictable
Security expert Graham Cluley blogged to say the stash of stolen passwords revealed a "worryingly predictable story of the extremely poor choices made by users."
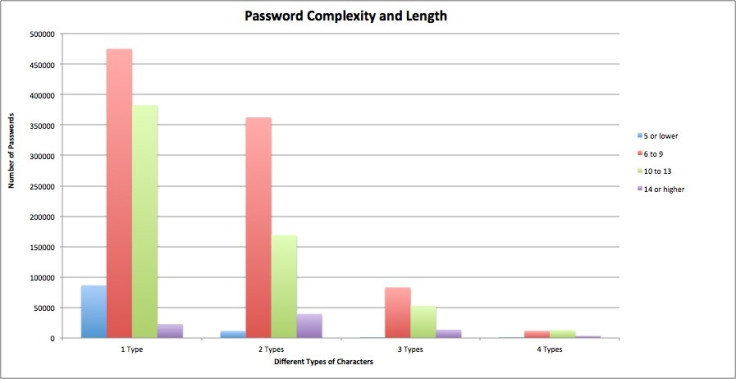
Further analysis by Trustwave found the most popular type of password was between six and nine characters long, but contained just one type of character - in other words, all lower-case letters or all numbers. Only a tiny fraction of the two million passwords contained three or four types of character, and very few were more than 14 characters long.
Along with social network and email login details, the ninth most popular service for which passwords were stolen by the Pony botnet was ADP, a payroll service provider.
Trustwave's Daniel Chechik and Anat Davidi commented: "Facebook accounts are a nice catch for cyber criminals, but payroll services accounts could actually have direct financial repercussions.
In a statement sent to IBTimes UK, Brian Spector, CEO of security firm CertiVox, said: "It is high time that organisations everywhere took a second look at the security methods that they employ - what is proven time and again is that username and password security systems are inherently weak, offering a wide range of attack vectors to criminals, along with a valuable harvest of private customer information."
Inherent problems
Spector also highlighted the dangers of using the same password for multiple accounts. "This," he adds, "coupled with the inherent problems with storing such complete information on one server really adds to the argument that it is time for companies to move beyond username and passwords and find a more secure method."
One such method is two-step authentication.
Used by Facebook, Twitter and others, the system requires the account holder to verify any login attempt made by a computer or mobile device not previously used by them.
Typically, a text message with a verification code will be sent to the account holder's mobile phone, and only once this has been entered, along with the username and password, will access be granted. Although numerous online services use this system, it is not yet compulsory.
© Copyright IBTimes 2025. All rights reserved.






















