Amnesty International exposes mysterious espionage scheme against journalists and activists
Meet 'Safeena Malik', the fake persona at the heart of a cyber campaign targeting activists.

Over the past 12 months a sophisticated, persistent, cyber-espionage campaign has been targeting journalists, trade unionists and activists working around the subject of labour rights – and alleged abuses – in the countries of Qatar and Nepal.
In a new report, Amnesty International, the global human rights organisation, detailed how a suspected state-sponsored actor used online services, including Facebook and LinkedIn, to conduct a lengthy "phishing" style campaign designed to pilfer personal credentials.
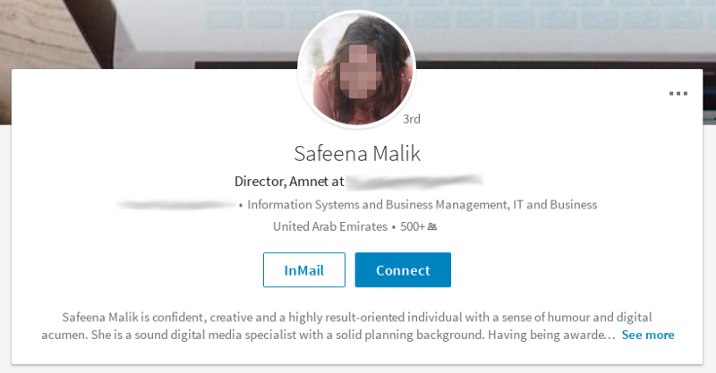
It only came to light after victims reported being contacted by an account using the name "Safeena Malik", claiming to be an activist based locations including London, UK. But this was no ordinary account, instead the persona was part of a well-oiled cybercrime scheme.
Claudio Guarnieri, a technologist at Amnesty, explained in a blog post how the attackers behind "Safeena Malik" went to the trouble of generating a full online and social media presence. The associated LinkedIn profile, for example, had over 500 connections.
Other active profiles, including on Facebook and Twitter, appeared to follow a clear pattern: friends and followers were mainly Middle East-based journalists, staff for human rights organisations and campaigners for migrant/labour rights in the state of Qatar.
The Amnesty probe exposed how the attackers behind the Malik account regularly engaged with victims in order to trick them into inserting their Gmail credentials to a specifically designed website designed to look identical to the real Google version.
The campaign was persistent, often lasting several months. In one example "Safeena" tried to lure a target by asking for help on a research project. "I am doing research about human trafficking. Can you help in this? I want to share my research with you," the account wrote.
The attackers would send what appeared to be invitations to access a Google Drive-hosted documents. Again, the page mimicked the official version in great detail.

Interestingly, Amnesty said the campaign took great steps to keep suspicions to a minimum. To this end, after a victim entered their account details they would indeed see a legitimate document.
But despite the smoke and mirrors, their account details were already compromised by this point.
In another example, the attackers approached victims directed on Facebook and used the messaging function to chat. The account of "Safeena Malik" was able to infiltrate several groups "dealing with migrant workers and forced labour," Guarnieri reported.
The persona has been used to launch cyber-espionage and phishing attacks on roughly 30 different people, Amnesty said. While many remained unnamed, one target, the International Trade Union Confederation (ITUC) admitted being involved but said it did not believe it was hacked.
In the past, the Brussels-based ITUC has held campaigns around migrant labour rights. Amnesty said a "significant number" of targets were from Nepal, which it noted is one of the largest nationalities amongst migrant workers in Qatar.
Who is behind the operation?
Like all attribution in the world of cybercrime, it remains unclear who is responsible. "The fact that the campaign specifically targets individuals active on human rights issues in Qatar, makes us believe that it might be a state-sponsored or affiliated actor," said Guarnieri.
While the identity of the individual – or team – behind the operation remains elusive, the attackers did log into some email accounts from an IP address linked to a web service provider called Ooredoo, a firm which has its headquarters in Doha, Qatar.
Amnesty contacted the government of Qatar to ask if it had any involvement with the operation or phishing campaign – a challenge it denied. "We consider such practices to be unethical and would regard them as a clear violation of our government's principles," it said in a statement.
© Copyright IBTimes 2025. All rights reserved.






















