Android users beware: Notorious 'BankBot' Trojan hits Google app store to drain accounts
The banking malware can empty accounts by mimicking legitimate applications.

Android users have been warned to avoid two applications discovered on the Google Play Store, the official mobile marketplace, after they were found to be laced with malicious software that could exploit legitimate 'accessibility services' and empty bank accounts.
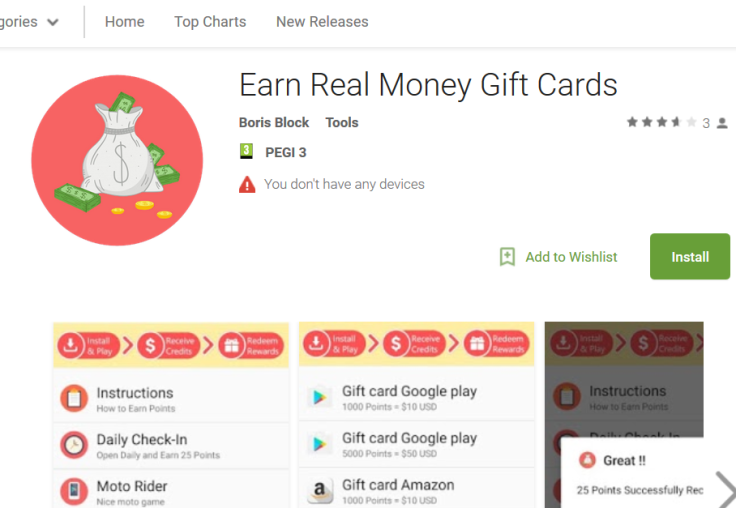
This week, two cybersecurity firms – Zscaler and SfyLabs – released detailed analysis of the applications, which were called 'Earn Real Money Gift cards' and 'Bubble Shooter Wild Life'. One, the companies found, had been spreading the notorious "BankBot" Trojan.
BankBot, which targets Android smartphones, had its source code leaked online back in January and has since transformed into a major cybercrime threat.
It has the ability to pose as legitimate banking applications to trick users into entering their credentials – in turn providing full access to accounts.
As reported, previous versions of the malware could also send texts, steal call logs, obtain contact list phone numbers and track device geolocations via GPS.
On 21 August, Zscaler found it had been smuggled onto Google Play within Earn Real Money Gift Cards.
The second app, Bubble Shooter Wild Life by the same author using the name "Boris Block", was identified as a downloader Trojan which could abuse Google's Play Accessibility Services – typically designed to help disabled users navigate and interact with the software.
It could install additional applications without a user's permission, Zscaler's experts wrote in a blog post a day after becoming aware of the malware.
The Google Android security team has been notified but, at the time of writing, both remain online.
Bubble Shooter Wild Life could stay hidden because it didn't trigger any malicious activity until 20 minutes after installation, effectively evading security checks. Like many other games, it asked for permissions to work – but these granted it far more access than it needs.
"When users try to enable the service, they see the list of services required," Zscaler said. "Considering the techniques used by the malware author, the user is most likely going to accept these permissions and press OK, giving the accessibility permission to the malware."
The app shows a fake Terms and Conditions page that mimics a version from Google, again adding to the illusion of legitimacy. All it takes is a single click to take hold.
The malware attempts to dupe the victim into letting it enable an Android option that permits installation from "unknown sources". Zscaler claimed that the abuse of accessibility service to install more malware was "unique".
Both applications – the BankBot Trojan and the downloader – were recently uploaded to the marketplace and, as such, have been accessed fewer than 5,000 times. Even so, some commenters on the store have been suspicious. "Malware detected," one said in late July.
"It looks like the developer is still working on improving his dropper app," conduced SfyLabs in a blog post, referencing the Bubble Shooter Wild Life software.
"Any new update to the app can add an embedded APK which will be installed after the app is started," the analysis continued. "With a simple campaign on social media the app can be spread rapidly, especially since the app appears to be a normal and fun game to the average user.
"As we have long expected droppers will probably become more common."
To help stay safe from banking Trojans and other malicious software, Android users are advised to only download apps from legitimate sources, remain vigilant when any application asks for permissions and never enter personal passwords into suspicious services.
See the hack in action via ESET's Lukas Stefanko:
© Copyright IBTimes 2025. All rights reserved.






















