Apple iOS not as secure as you think – App Store tricked into allowing users to install pirate apps

Chinese developers have managed to sneak past Apple's strict code reviewers to upload an app to the App Store that is actually a third-party App Store client, enabling users to download and install pirated and modified iOS apps for free onto non-jailbroken devices. This could spell trouble for the future of iOS security.
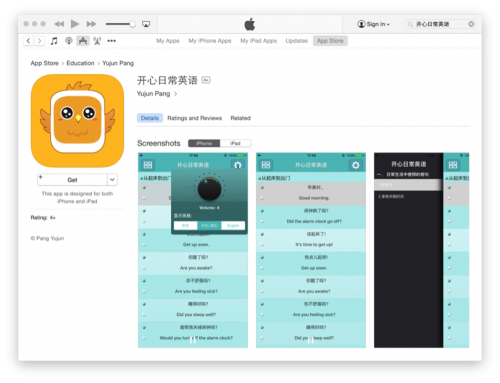
The app, called 开心日常英语 ("Happy Daily English" in Mandarin), was available for purchase on the App Store between 30 October 2015 until 20 February 2016, when security researchers from Palo Alto Networks contacted Apple.
According to the researchers' blog, the app pretends to be an educational app for learning English if it is looked at by reviewers and users on IP addresses outside China. However, if you look at the app while on an IP address within mainland China, then the app turns into a third-party App Store client instructing users how to set up a provisioning profile that lets users download modified versions of popular iOS apps for free.
Apple's iOS security fortress might be crumbling
Today, it is still relatively rare to find malware on iOS devices, as Apple keeps a very tight control over what apps can do when they are loaded on the iOS operating system, to ensure that an app cannot access other parts of an iPhone to carry out malicious behaviour.
Only if the app meets the security criteria is it allowed to be published to the official App Store, so if users don't want to pay for apps and seek to download them from a third-party App Store, they have to jailbreak their phones, which only lasts until you update to the next version of the iOS operating system.
This attitude to security also prevents users from customising their phones as much as they would like, which has led some iPhone users to switch over to Android. However, the open-source Android operating system, which allows for a wide level of customisation, has its shortfalls in that it is much easier for hackers to develop mobile malware that works on Android devices.
But now it seems that criminals are steadily finding more and more ways to get around Apple's security measures too, with recent examples like the YiSpector malware – which abused private APIs in iOS to infect non-jailbroken devices – or XcodeGhost, which hid in iOS apps and stole user data.
Using iOS developer feature to bypass Apple reviewers
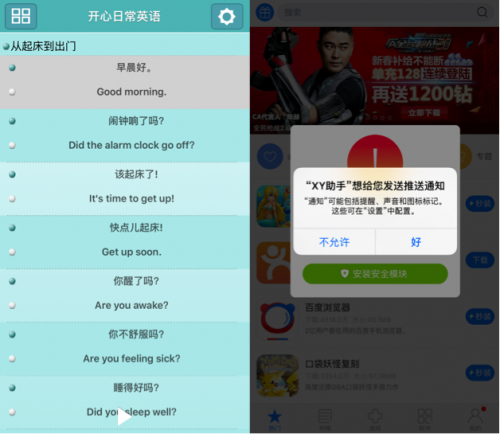
The developers behind this app managed to completely bypass Apple's strict sandboxing security rules by using a new feature of the Apple Developer Enterprise Program called Xcode7. Xcode7 lets developers obtain free personal development code-signing certificates so that they can build, sign, test and distribute apps on a limited scale, such as in-house apps that are meant to help an enterprise run its business.
Since in-house apps contain proprietary information and are only designed to be used by employees in a company, they would understandably not be published to the App Store, and this method of testing apps is also much cheaper than enrolling in Apple's Developer Program, which costs $99 (£70) for a year's subscription.
It seems that the criminals figured out how to get Xcode to automatically generate the personal development code-signing certificates without having to go through Apple's server for approval, and the researchers call this technique "ZergHelper".
Researchers found over 50 ZergHelper apps being distributed by channels other than the App Store. These apps have been signed by different enterprise certificates, and could just as easily be installed on a non-jailbroken iOS device by tricking Apple in the same way as the Happy Daily English app.
And although the researchers did not find any sign of malware in the app, they feel the ZergHelper technique could be used by others for malicious attacks in future.
© Copyright IBTimes 2025. All rights reserved.






















