Ashley Madison hack as it happened: Who is named in cheating site's big data leak?

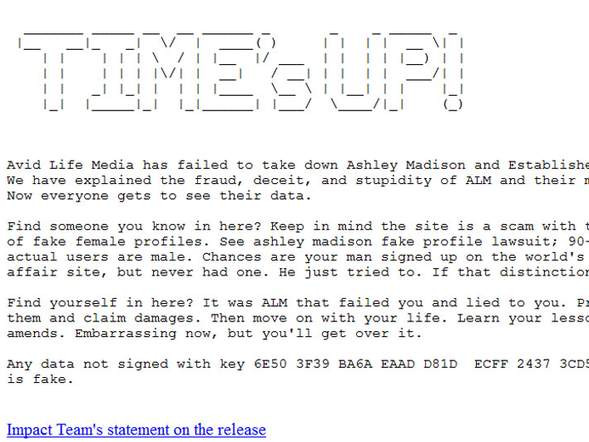
Hackers have leaked the account details and logins for nearly 32 million users of cheating website Ashley Madison. The data dump on the dark web by the hacking group Impact Team comprises names, street addresses, email addresses and amounts paid to Ashley Madison.
The group threatened one month ago that it would release the information if Avid Life Media, Ashley Madison's parent company, did not take down the site and its sister Established Men.
In a message accompanying the dump, the hackers said: "We have explained the fraud, deceit and stupidity of ALM and their members. Now everyone gets to see their data."
- Names of members of the British government were reportedly found to be on a list of over 30 million email addresses, along with those from the US Department of Defense.
- Some 15,000 with .mil or .gov addresses were found in the released data.
- Ashley Madison's parent company Avid Life Media has said in a statement that it is aware of the dump.
If you want to find out if your email address ... or someone you know is on the Ashley Madison list, check this website: ashley.cynic.al
The developer, known only as 'Rufo' created the website to search the huge database of emails published by the hackers. Rufo acknowledges that users may not know if the website checker is legitimate but says: "I'm the same person who made the Adobe leaked password checker if that lends me any credibility."
A warning though: It will only show if an email has been used to sign up for a profile with Ashley Madison but it will not say if the user has been actively using the site, names, credit card details or sexual preferences.
Rufo says: "It is possible someone accidentally or deliberately registered the wrong email address. Determining the likelihood of this is left to you. You'd be amazed how many people apparently don't know their own email addresses, so be skeptical about the results, especially if the person's name is common."
Political Scrapbook says that after crunching the public sector numbers from the Ashley Madison website, the number of gov.uk email addresses is slightly slower than first suggested, due to duplicate entries in the database.
It noted that as with students on the university accounts, a significant number of the Ministry of Defence emails appear to be those with lower ranks using the armymail system rather than "randy generals and Whitehall officials".
The spread of public sector domains are: universities, colleges and research establishmentsL ac.uk (1,716); Government: gov.uk (124); MoD: mod.uk (92), local education authorities and schools: sch.uk (65); National Health Service: nhs.uk (56); police force: police.uk (less than 50).
Graham Cluley, an independent computer security analyst warns that the list should NOT be taken at face value because Ashley Madison requires no email verification when creating a profile.
"You might have joined the site years before when you were single and be shocked that they still have your details in their database, or you might have joined the site out of curiosity or for a laugh... never seriously planning to take things any further."
"But more importantly than all of that, if your email address is in the Ashley Madison database it means nothing. The owner of that email address may never have even visited the Ashley Madison site."
According to Gawker, Duggar purchased a $250 "affair guarantee" that promised him money back if he didn't "have an affair within three months."
There is currently no evidence that Duggar was involved in any extramarital affairs via the hook-up site. But unsurprisingly, Twitter showed no mercy following the latest revelation to surface about the disgraced TV star.
Duggar's profile included an extensive list of encounters that he was seeking including: "Conventional Sex," "Experimenting with Sex Toys," "One-Night Stands," "Open to Experimentation," "Extended Foreplay/Teasing," "Bubble Bath for 2," "Likes to Give Oral Sex," "Likes to Receive Oral Sex," "Someone I Can Teach," "Someone Who Can Teach Me," "Sharing Fantasies," "Sex Talk."
More details have reportedly emerged relating to Josh Duggar's alleged paid subscriptions to Ashley Madison.
A credit card in Duggar's name and connected to his grandmother's address was used to pay "a total of $986.76 for two different monthly Ashley Madison subscriptions from February of 2013 until May of 2015," reports Gawker.
Disgraced reality TV star Josh Duggar of TLC's 19 Kids and Counting fame was allegedly a user of Ashley Madison, it has been reported.
Duggar was previously named the executive director of the Family Research Council, a conservative lobbying group in D.C. which seeks "to champion marriage and family as the foundation of civilization, the seedbed of virtue, and the wellspring of society."
Duggar was forced to resign after In Touch Weekly reported that he had molested five young girls. It has now emerged that during that time, he also maintained a paid account on Ashley Madison.

Biderman, who has been happily married for twelve years, told http://www.stuff.co.nz recently: "People have affairs for a multitude of reasons. I don't think there's a one-size-fits-all approach to infidelity ... I believe monogamy is worth pursuing and that it's a worthwhile endeavour."
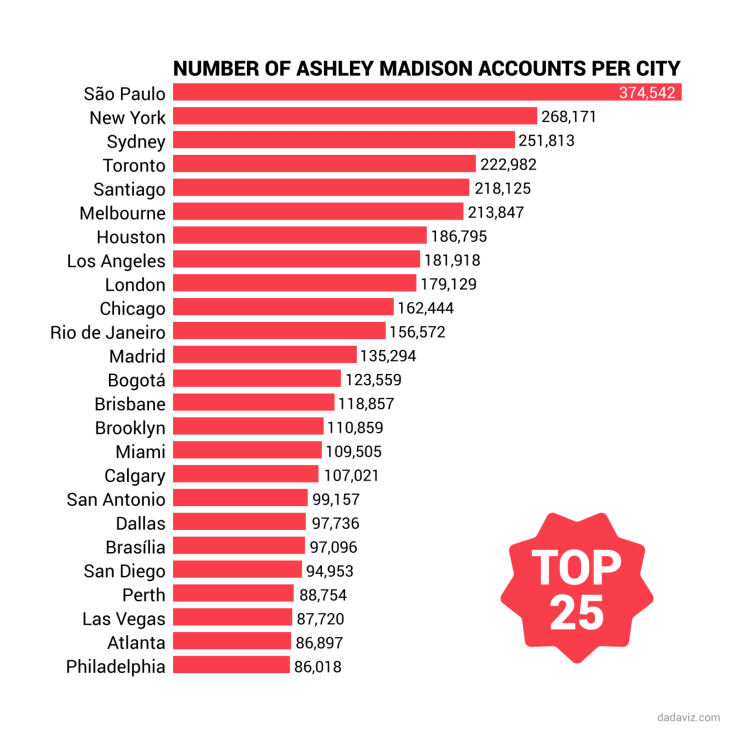
As the cheaters database is scrutinised online, it has been reported that it includes email addresses linked to the White House and NASA, as well as the Vatican and the United Nations. Senior professors at top universities are also included in the list.
The inevitable revelations to come, of celebrities who have used the site, means the fallout from the latest hacking scandal is going to be felt for many weeks and months to come.
With families, relationships and reputations at risk after the release of customer data from infidelity website Ashley Madison, Rik Turner, senior analyst of infrastructure solutions at consultancy firm Ovum said the outcome for users of the site is inevitable.
"If your name's been published, you're going to live in fear. There's nothing you can do once it's been published."
Representatives for Ashley Madison have confirmed the compromise to their database and are condemning the attack that is being investigated.
"This event is not an act of hacktivism, it is an act of criminality. It is an illegal action against the individual members of AshleyMadison.com, as well as any freethinking people who choose to engage in fully lawful online activities."
Among personalities who have come out as Ashley Madison account holders is British journalist and novelist Celia Walden, who speaking to ITV's Lorraine morning show quipped she is "going to be in trouble" as a few years ago she signed up for the website as part of her research to prepare an interview with its founder. Walden is married to journalist and television personality Piers Morgan.

Ashley Madison's parent company Avid Life Media has denied users' credit card details were stolen, saying it has never stored full card numbers.
Avid Life Media said in a statement: "No current or past members' full credit card numbers were stolen from Avid Life Media. Any statements to the contrary are false. Avid Life Media has never stored members' full credit card numbers."
In a separate email to Reuters the company however confirmed that some legitimate data has indeed been stolen.
"There has been a substantial amount of postings since the initial posting, the vast majority of which have contained data unrelated to AshleyMadison.com but there has also been some data released that is legitimate," Avid Life spokesman Paul Keable told the news agency.
In his blogpost on the data dump, Errata Security Chief Executive Rob Graham also gave his take on the hackers' motives. He wrote:
They appear to be motivated by the immorality of adultery, but in all probability, their motivation is that #1 it's fun and #2 because they can. They probably used phishing, SQL injection, or re-used account credentials in order to break in.
British MP Michelle Thomson, a married mother of two, said her email address is among those released as part of the data dump.
The newly-elected SNP MP for Edinburgh West said her email was used to set up an Ashley Madison account without her knowledge, suggesting it might have been the work of someone aiming to smear her name.
She said:
Along with potentially millions of others, an out-of-use email address seems to have been harvested by hackers. I am not aware of or in contact with either Avid Life or Ashley Madison and look forward to finding out more about what has actually happened.
However, having a personal email address linked to an account doesn't mean that person is really a user of Ashley Madison. Users are able to sign up to the site without responding to an email verification, meaning anyone's email address could have been used to create an account.

Ashley Madison does not verify the email addresses of its users, meaning that many of them may be false.
While Ashley Madison's owners Avid Life Media are coming in for a lot of criticism over the security measures it had in place, the company at least did one thing right.
The leaked database contains encrypted passwords which use the bcrypt function to secure the details, which is widely seen to be more secure that the common MD5 standard that most sites use - if they use any encryption at all. Of course this will be of little comfort to the people whose information has been suddenly splashed all over the internet.
As well as security researchers trawling the data dump to assess the impact of the leak, in the more seedy corners of the internet such as 4Chan and 8Chan, users with access to the data are fulfilling requests from others to check very specific email addresses - some of which are from official bodies while others are clearly seeking to identify co-workers or even friends.

A relatively comprehensive list of email addresses associated with employees at companies such as Amazon, Boeing and Sony; governments agencies in the UK, Canada and France; defence contractors such as Raytheon and BAE Systems and banks including JP Morgan, Bank of America and Citigroup has been collated here.
As researchers begin to crunch the numbers of the Ashley Madison database, some interesting stats are beginning to emerge. The first is that among the 33 million or so user accounts included in the leak, the vast majority is men, with security researcher Robert Graham counting just five million accounts marked female to 28 million market men - with two million undetermined.
Ashley Madison has previously been accused of creating fake female accounts to lure male customers to use the site, with some reports suggesting the customer base is up to 95% male.
Two more sites have been set up to allow Ashley Madison customers to check whether their data has been hacked - ashleymadisonleakeddata.com and ashleymadisonleaked.com. The latter has crashed.
Millions of PayPal and bank details are believed to have been leaked with the data raising fears of fraud. Michael Sutton, chief security information officer at Internet security company Zscaler, has commented that:
"There are no bulletproof countermeasures for consumers when it comes to protecting financial data or Personally Identifiable Information (PII). Consumers should assume that breaches will occur and take steps to limit exposure. This can be best achieved by restricting purchases to reputable vendors, sharing only necessary information, avoiding insecure networks and regularly checking banking records and credit histories to identify potentially fraudulent transactions."

Calls to both Ashley Madison's customer service centres in the US and the UK are going unanswered at the moment. It is not clear whether this is the case because call centres are overwhelmed or because the company has stopped offering customer service in the wake of the data leak.
Those calling reach a pre-recorded message by woman with a North American accent asking customers to pose their query in an email.
Cyber security company Blue Coat, which has been doing its own research into the data leak, has said the aftermath will last a month and in the coming weeks three prongs of attack by those wishing to gain from the information can be expected:
1. Reselling personal data to other cyber attackers: Now that more than nine gigabytes of data has been released, they may begin to look at the financial value of a target to see if they will profit from the time spent building malware for the attack. This data is most likely to be among some of the most valuable data set compromised so far. If it is worth $100 to "go away" and there are 37 million users, this could be one of the largest cyber heists in history.
2. Financial or non-financial blackmail of Ashley Madison and its customers: Not all of the personal data of Ashley Madison users has been released, therefore cyber attackers may go directly to the management, or to the individual users of Ashley Madison and ask for a payment for the release/deletion of personal data. Blackmail can also happen through non-financial means by coercing victims into working with the attackers as an insider.
3. Social engineering to take down bigger business targets: Attackers can identify high-value targets who are members of Ashley Madison and collect widely available social media data to impersonate the victim over a long period. If successful, attackers can gain unrestricted access to corporate networks and sensitive work information.
Paddy Power is now offering odds on who will be caught out by the Ashley Madison data leak.
The bookmakers is offering 1/10 for a Premier League footballer to be named, 1/4 for an MP, 2/1 for a Roman Catholic cardinal and 5/6 for a member of the royal family.
Paddy Power is also offering odds of 7/1 that a TOWIE cast member found out by the cheating site and more generally it is giving odds of 6/1 for a record number of divorces in the UK in 2015 and 5/2 that Ashley Madison will hold its IPO in London this year.
The 30 million email addresses in the data dump have been uploaded by haveibeenpwned.com
The list is not searchable but after users verify their email addresses they will be notified if their data has been breached.
Marriagehelper.com has given step-by-step advice to cheating spouses on how to break their infidelity to their spouses in the wake of the Ashley Madison hacking.
"There are several things you need to consider before telling your spouse. If you walk in and confess without having done introspection, you probably are going to create an even bigger problem. Think before you act. Think carefully," the website advises.

BuzzFeed has reported that executives at Ashley Madison knew they were vulnerable to attacks before the hack.
On an internal questionnaire CEO Noel Biderman wrote: "We should put any and all efforts forward to defend against any security issues that can put our brand and 15 years of hard work at risk," according to the news website.
Trevor Stokes, the CTO, wrote: "I would hate to see our systems hacked and/or the leak of personal information."
Initial surveys of the data has shown that as many as 150 UK government addresses have been found within the data. However, because Ashley Madison does not verify the email addresses of its users, many of them may be false.
Also, even if the addresses are correct the users may have signed up to the website for reasons other that seeking affairs.
Media in Canada, where Ashley Madison is based, has reported that the hacking team responsible for the leak is seeking fame and notoriety. Claims have also been made that the hackers must have been linked to Ashley Madison in the past.
"These guys want as much notoriety as possible. This isn't cyber terrorism. It's cyber vigilantism," Ajay K Sood, general manager for Canada of cyber security firm FireEye Inc, told CBC news.
Troy Hunt, a Microsoft security expert, has told the Canadian broadcaster that more than one million unique email addresses were attached to payment records.
Online security expert Gary Newe, Technical Director at F5 Networks, has said beyond the moral argument over the service provided by Ashley Madison that the data dump is nevertheless still a breach in privacy.
"Regardless of your views on Ashley Madison's customers and the service, this is an unacceptable breach of online privacy. If we start separating hacks into those that are acceptable and those that are not, where does it stop? If we want to keep businesses and consumer data safe from hackers, we need to be on the same side of the fence, rather than deciding whether a hack is moral or not," he said.
An Ashley Madison user in Saudi Arabia has written on Reddit that he may be stoned to death in his home country after using the site to have discreet homosexual relationships.
"I was single, but used it because I am gay; gay sex is punishable by death in my home country so I wanted to keep my hookups extremely discreet. I only used AM to hook up with single guys," he wrote.
The anonymous user has asked people to share his story (which can be found here) in the hope the data will be removed.
His story highlights the fact that a number of Ashley Madison users were not using the site for affairs.
Ashley Madison has appealed to the public for information about the hackers.
"We know that there are people out there who know one or more of these individuals, and we invite them to come forward. While we are confident that the authorities will identify and prosecute each of them to the fullest extent of the law," the company has said.
© Copyright IBTimes 2025. All rights reserved.