BankBot malware: More apps carrying the banking Trojan sneak into Google Play Store, UAE banks targeted
One BankBot-infected app was downloaded between 5,000 and 10,000 times.

Security researchers have discovered that more apps carrying the malicious BankBot Android banking malware have made their way into Google's Play Store. The malware, which surfaced back in January, targets legitimate banking apps and uses fake overlay screens to trick unsuspecting users into providing their credentials.
The malware is even able to hijack and intercept SMS messages, allowing it to bypass the SMS-based two-factor authentication security feature.
According to a blog post by Trend Micro on Wednesday (13 September), the latest variant of the mobile malware has been targeting legitimate apps from banks based in 27 countries, including 10 from financial institutions in the United Arab Emirates. So far, BankBot has targeted 160 apps, researchers said.
"Recently we found five new Bankbot apps, four of which made their way into the Google Play Store disguised as utility apps," Trend Micro said. "Two of these were removed immediately, while the other two were made available long enough to be downloaded by a few users."
One particular app infected with the malware was downloaded between 5,000 and 10,000 times.
Researchers found that the new variant of BankBot only works if the running environment is a real device, an app of a targeted bank is already installed on the device and the device's location is not in the Commonwealth of Independent States (CIS) countries.
"When BankBot is installed and running, it will check the package information of apps installed on the infected device," the security firm said. "If one of the target bank apps is available, BankBot will connect to its C&C server and upload the target's package name and label.
"The C&C server will send a URL to BankBot so it can download the library that contains files used for the overlay webpage. This overlay page is displayed on top of the legitimate banking app and used to steal the user's credentials."
Trend Micro found that BankBot exhibits slightly different behaviour when targeting UAE banking apps. Rather than directly displaying the fake overlay page, BankBot requests the user to enter their phone number.
The C&C server then sends a pin code to the targeted victim in a FireBase Message. Once the person enters the given pin, they are then prompted to plug in their bank details. Even if the users have provided the correct details, an "error screen" will pop up and ask them for the details again.
"Apparently, the author of BankBot wants to verify the banking details of their victims," Trend Micro explains. "They ask for the details twice, just in case users input it incorrectly at first. BankBot will send the stolen data to the C&C server only after account information is entered twice."
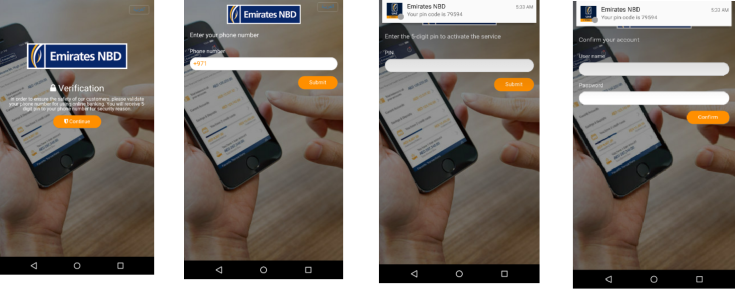
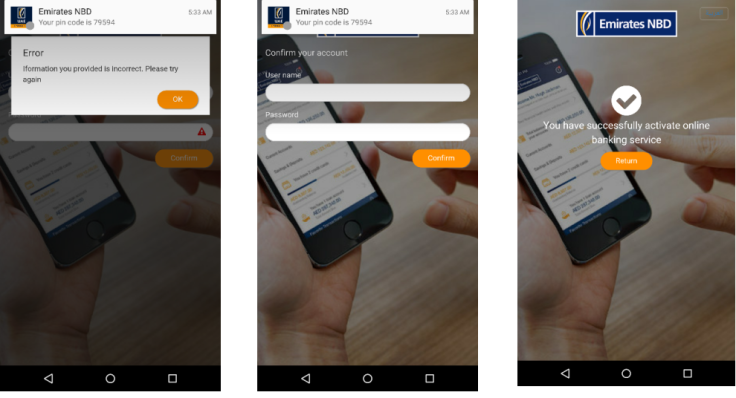
"BankBot seems to be widening its reach and experimenting with new techniques — which is a mounting concern because banking apps are growing more ubiquitous," Trend Micro researchers continued. They noted that mobile banking users in the Middle East and Africa is expected to cross a whopping 80 million by the end of the year.
"As more people adopt this technology, the apps become attractive targets for cybercriminals," they said.
© Copyright IBTimes 2025. All rights reserved.





















