Chinese Hacking Ring Targets Videogame Developers
Cybercrime group has attacked online games since 2009
A hacking group based in China has been attacking videogame developers since 2009 and is still active, targeting online multiplayer games in order to steal in-game currency.
The attackers were uncovered by security researchers at Russia's Kaspersky Lab in 2011 and the group, known as Winnti, has attacked at least 35 game companies over the past four years, with the ultimatle goal of obtain in-game currency which can then be exchanged for real money.
The type of games being targeted are those known as Massively Multiplayer Online Role-Playing Games (MMORPG) with US games company Trion - developers of Rift and Defiance - one of the most high profile targets.
According to Kaspersky the Winnti stole digital certificates from legitimate software vendors so that users would download malware to their computers more readily. Digital certificates are electronic authentication keys which are attached to software sent over the internet which systems trust comes from a legitimate source.
Kaspersky said that Winnti's initial goal was industrial espionage, obtaining the source software code of the games, allowing the group to manipulate these online titles so that in-game currency would accumulate faster but without drawing suspicion from the games' moderators.
"Members of the Winnti team are patient and cautious. Cybercriminals have affected the processes of the online games from the infected companies and stolen money from them for years, but they have found ways of doing this without attracting attention to themselves," Kaspersky said in its report.
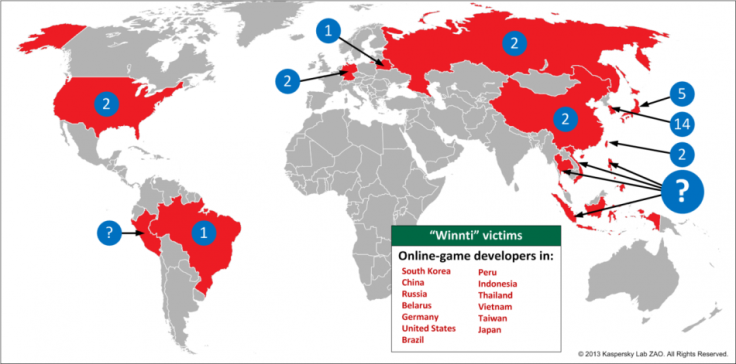
Winnti's attacks are focused mainly on game companies in south east Asia, in countries including South Korea, Japan and China. However the group has also targeted game companies in Germany, Brazil, Russia, Belarus and the US. South Korean game firms Sesisoft, Mgame Corp. and Neowiz are listed as confirmed victims of the Winnti group.
"[Kasperky's] team of experts has been diligently working with the IT security community, online gaming industry and certificate authorities to identify additional infected servers while assisting with the revocation of stolen digital certificates. Currently the Winnti group is still active and Kaspersky Lab's investigation is on-going," the security company said.
Kaspersky first identified Winnti in 2011 when malicious Trojan software was discovered on a large number of computers all used to play the same unspecified online Following an investigation the source of the malicious software was a official update from the game's publisher itself.
The initial reaction was to believe that the publishers themselves were spying on their own players, but further investigation revealed the hacking group was targeting the game companies' servers directly.
© Copyright IBTimes 2024. All rights reserved.























