'Clinton caught on video giving money to Isis' malware email scam exposed
Campaign was exposed by researchers at cybersecurity firm Symantec.

If you received an email that promised to show a video of Democratic Party candidate Hillary Clinton meeting with a member of the Islamic State terror group in a money exchange deal, would you click the link? A new email spam campaign being used to spread malware is hoping the answer is in the affirmative.
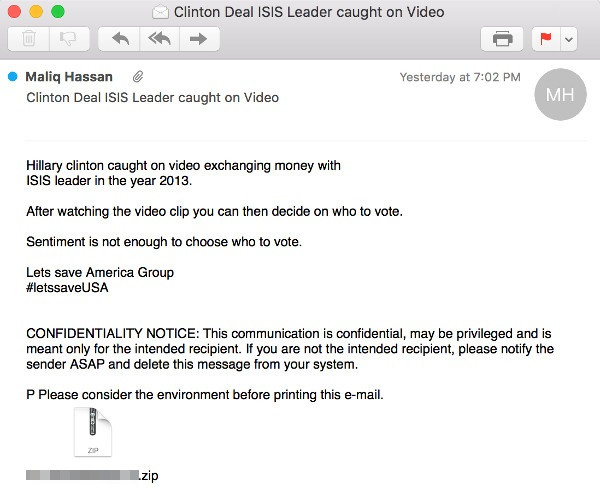
As detailed by cybersecurity firm Symantec, the email's subject announces: 'Clinton Deal ISIS Leader caught on Video', however there is no video contained in the email, just malicious software that could allow hackers to compromise your computer.
The email states: "Hillary Clinton caught on video exchanging money with Isis leader in the year 2013. After watching the video clip you can then decide on who to vote. Sentiment is not enough to choose how to vote. Let's save America Group. #letssaveUSA"
Attached to the email is a file in .Zip format that, upon analysis, was found to contain a malware-ridden Java file. If the recipient opens the file in an attempt to view the video they will be swiftly infected with a Remote Access Trojan (RAT) called Adwind.
Symantec said it also observed two Visual Basic Script (VBS) dropped by the malware that can be used by hackers to uncover vital information about what type of firewall and anti-virus is running on the infected computer.
Up to 85% of the recipients of the clickbait-enhanced spam campaign were located in the United States, perhaps unsurprising given the subject of the email. However, the same content was also spammed to users in the United Kingdom, Canada, and Mexico.
"World news and events are a preferential topic for general spam and in some phishing scams," Satnam Narang, security expert at Symantec, told IBTimes UK. "This was the first time this election season that we observed a malicious spam campaign including one of the U.S. presidential candidates.
"We advise everyone to keep an eye out for suspicious emails that may use either presidential candidate, Hillary Clinton or Donald Trump, as bait," he added. "When seeking news related to the US elections only visit trusted news websites and avoid opening unsolicited emails."
The Adwind Trojan can infect Windows, Mac, Android and Linux operating systems and can be used to create a 'backdoor' into computer systems to help a cybercriminal steal sensitive files or documents.
The RAT has been on the scene since at least 2012, but has been known under a number of aliases over the years – including AlienSpy, Frutas, Unrecom, Sockrat, JSocket, and jRat. Most recently, according to Softpedia, it re-branded to the name JBifrost.
Despite email clients like Gmail and Hotmail coming with highly effective spam-blockers in recent years, there are a number of ways to quickly spot malicious spam emails that may still sneak through the cracks.
Often, the first indication that something is amiss will be obvious spelling or grammatical errors – two things this campaign clearly has based on the image provided by Symantec. Other warning signs include suspicious attachments, dodgy email addresses or unsolicited advancements, offers and coupons. Using a common sense approach, the advice from cybersecurity experts is always the same, if suspicions are aroused – do not click the link.
© Copyright IBTimes 2025. All rights reserved.






















