'CopyCat' malware infected 14 million Android devices and generated $1.5m for hackers
CopyCat malware was able to give hackers 'full control' over roughly 8 million devices.

In a lucrative cybercrime scheme, hackers were able to use a strain of mobile malware to infect 14 million Android devices and generate roughly $1.5m (£1.2m) in illicit advertising revenue over a period of two months last year by "stealing credit" for app referrals, experts have revealed.
In a 13-page analysis this week (6 July), researchers from cybersecurity firm Check Point said the malware – dubbed CopyCat – was able to successfully give hackers "full control" over roughly 8 million devices in an "unprecedented" campaign between April and May last year.
The majority of infected users were in Southeast Asia, but the analysts found it also spread to more than 280,000 Android devices in the US. It had the ability to gain root permissions, maintain persistence and control "any activity" on compromised devices.
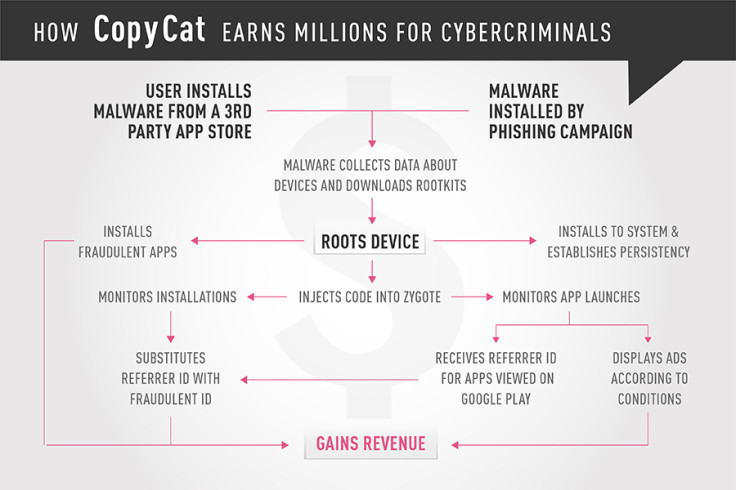
The hackers' campaign peaked last year, with the researchers revealing that it spread via popular apps that had been "repackaged" with malicious components and uploaded to third-party stores. There was no evidence it spread via the Google Play Store.
Ultimately, it used "state of the art" capabilities to conduct advertising fraud. Upon infection, it would attempt root the device before injecting malicious code into Zygote, a core Android function that controls the launching of all apps.
In short, the malware used two tactics to steal ad revenue: displaying fraudulent ads for clicks and stealing referrer IDs of apps installed from Google Play – the official Android marketplace.
Typically, legitimate advertisers are paid for displaying ads that lead to the installation of certain apps but in this case the malware was designed to let the hackers generate funds by allegedly scamming a leading analytics service called Tune, Check Point said.
The researchers were able to gain insights by retrieving data from the malware's command and control (C&C) servers. The firm claimed malicious ads were displayed on 3.8m infected devices while 4.4m infected devices were used to "steal credit" for Google Play referrals.
This is believed to be the first example of adware using this technique. "We called it [CopyCat] because it takes credit for installations it didn't initiate, which is the big technological innovation it presents," Daniel Padon, Check Point threat researcher, told eWEEK.
Old exploits, new tricks
"CopyCat successfully rooted over 54% of the devices it infected, which is very unusual even with sophisticated malware," the researchers wrote, adding that all exploits used were "both widely used and very old" – with some being issued patches way back in 2013.
The exploits remained effective because "users patch their devices infrequently, or not at all".
The cybersecurity firm, which recently exposed a massive malware campaign dubbed 'Fireball', informed Google of the campaign in March 2017. The tech giant was then able to reduce the spread of the malware, but has warned that some infections may still exist.
It remains unknown who was behind the CopyCat malware attacks, however Check Point found links to an advertising network located in China called MobiSummer.
Researchers found "some of the remote services used by the malware" were created by the firm.
Interestingly, the malware doesn't target Chinese devices, which indicates the hackers are attempting to evade local investigations from law enforcement. In its blog, Check Point admitted it's possible the hackers "used MobiSummer's infrastructure" without the firm's knowledge.
To stay protected from Android malware of this nature, experts advise users only download apps from official marketplaces and ensure all devices have the latest security updates installed.
© Copyright IBTimes 2025. All rights reserved.






















