mSpy hacker says company knew of data leak two months ago

The hacker responsible for stealing sensitive customer data from mSpy claims the data was left completely unprotected and the company knew about the leak up to two months ago.
Speaking to IBTimes UK, the anonymous hacker says the details of tens of thousands of mSpy customers were left completely unprotected on a bank of six servers which didn't even have password protection.
Having initially denied all allegations that its customer data had been compromised, the US-based company finally admitted there had been a breach of its systems and customers data had been revealed.
Speaking to BBC News, mSpy spokeswoman Amelie Ross said: "Much to our regret, we must inform you that data leakage has actually taken place. However, the scope and format of the aforesaid information is way too exaggerated."
The leak was first reported by security expert Brian Krebs on 14 May after he was tipped off about the post on the dark web -- a part of the web only accessible using special tools such as the Tor browser.
However mSpy initially denied such claims, telling IBTimes UK in a statement that it was the "victim of a predatory attack, aimed to take advantage of our estimated commercial achievements".
They 'spit on safety, on me and on the clients'
The hacker, who provided evidence to IBTimes UK that he is the person responsible for dumping the data online, says that it was mSpy's failure to communicate with him that led to all the information being posted on the dark web for anyone to access.
The hacker says that he contacted mSpy up to two months ago but was completely ignored by the company. The hackers says the security gaps he discovered were subsequently fixed, but without ever talking to him.
He describes the actions of mSpy as "to spit on safety, on me and on the clients".
mSpy has claimed that it was the victim of blackmail threats and the hacker admits he was looking for some compensation for discovering such a gaping hole in the company's security systems.
The hacker says that he was able to easily access six servers which contained the customers databases and didn't use any authorisation -- not even a password.
The hacker would not provide any personal information due to the possibility of legal action against him, though he did include a quote in Spanish -- "Más vale prevenir que curar" meaning "Better safe than sorry".
400,000 customers' data
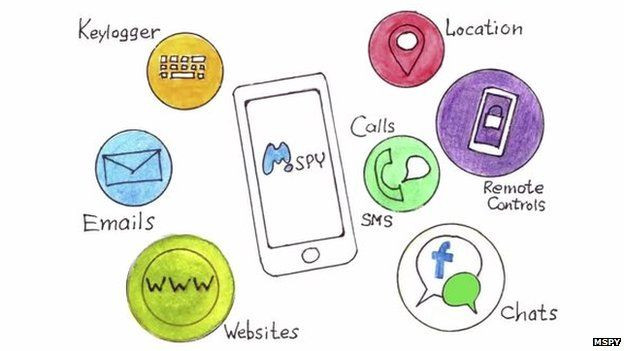
mSpy sells spying software for smartphones and PCs which is aimed at allowing parents to monitor their children and employers monitor their workers. The apps allow those using the service to monitor someone's location, what apps they use, see what photos they take and record every word they type or speak.
While it now admits that there was a breach, it denies that it is of the level being reported. Krebs initial report suggests there are details of 400,000 of mSpy's customers buried in the data dump but the company claims this figure is closer to 80,000.
It is, however, hard to believe anything that mSpy is currently saying, considering its continued denial of this leak over the past week, and especially if, as the hacker claims, it knew about the breach of its security up to two months ago yet didn't inform customers.
IBTimes UK asked mSpy to comment on the hacker's claims but at the time of publication has yet to receive a response.
Disturbing
In a new post, Krebs says he spoke to "multiple customers whose payment and personal data — and that of their kids, employees and significant others — were included in the huge cache. All confirmed they are or were recently paying customers of mSpy".
One customer said she was completely unaware of the data leak confirming she and her husband paid mSpy to monitor the mobile device of their 14-year-old daughter.
Addressing the fact that mSpy could be trying to cover up the leak, she said: "This is disturbing, because who knows what someone could do with all that data from her phone," adding that she and her husband had both discussed the monitoring software with their daughter.
"As parents, it's hard to keep up and teach kids all the time what they can and can't do. I'm sure there are lots more people like us that are in this situation now," she said.
According to the BBC, the UK's Information Commission is now getting involved, saying it is "aware of the breach and is trying to find out where the company is based".
A company representative speaking to IBTimes UK said the company's headquarters is based in Mountain View in California but it also had customer support centres in the UK and Germany.
Dark web explained
The dark web is a section of the internet that is not indexed by search engines such as Google, and not easily navigated to using a standard web browser. Accessing the dark web requires specialised knowledge and software tools. An example of this is content only accessible by using the Tor software and anonymity network, which while protecting privacy, is often associated with illicit activities.
© Copyright IBTimes 2025. All rights reserved.





















