Game of Thrones spoilers used by Chinese hackers to lure and infect victims with malicious malware
Proofpoint researchers said the Trojan has previously been used by Chinese state-sponsored hackers Deputy Dog.

Security researchers have discovered a new targeted email campaign that uses fake Game of Thrones Season 7 spoilers and video clips to lure curious fans and spread malicious malware. Security firm Proofpoint first came across an email on 10 August with a subject line that reads: "Wanna see the Game of Thrones in advance?"
The email features some details of upcoming episodes along with a malware-laced Microsoft Word attachment titled "game of thrones preview.docx" that purportedly lists potential GoT spoilers. Once downloaded and run, the "preview" executes a malicious PowerShell script that installs a diskless "9002" remote access Trojan (RAT) that has previously been used by state-sponsored Chinese hacker group Deputy Dog.
According to Proofpoint researchers, the 9002 RAT has previously been used in attacks attributed to Deputy Dog, also known as APT 17.
"Once installed, the 9002 RAT provides attackers with extensive data exfiltration capabilities," the researchers said in a blog post published on Friday (25 August). "Based on several shared identifiers, it is possible that the recent campaigns were conducted by the same actor that conducted the campaigns in early- to mid-2014.
"The 2014 campaign resembles activity previously attributed to the Deputy Dog (aka APT17) actor. Additionally, the Deputy Dog actor has been observed utilizing a similar 9002 RAT with an earlier iteration of the 4-byte XOR encoding algorithm in diskless mode."
Proofpoint suspects that the attack was likely carried out by Deputy Dog "based on similarities in code, payload, file names, images, and themes". Although they noted that they do not currently have "any definitive evidence linking this activity to Deputy Dog", the researchers said they have identified "enough similarities to support a possible connection".
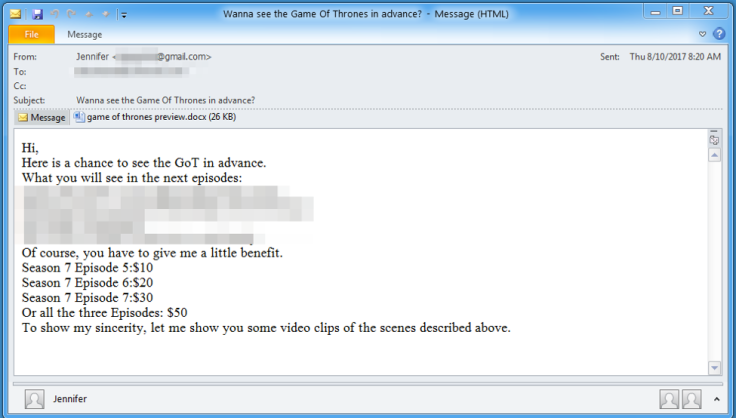
Proofpoint said the Game of Thrones lure is "especially relevant" now since the massively popular HBO show premiered in July and its finale aired on Sunday, 27 August.
"It is worth noting that episodes 4 and 6 were already leaked; it is unlikely that responding to the lure would actually net a recipient new, unreleased episodes, particularly considering that the final episode airs this weekend," Proofpoint said. "The use of a Game of Thrones lure during the penultimate season of the series follows a common threat actor technique of developing lures that are timely and relevant, and play on the human factor - the natural curiosity and desire to click that leads to so many malware infections."
Over the past month, a hacker using the online pseudonym "Mr Smith" claimed to have stolen 1.5 terabytes of programming material from HBO's computer networks and leaked some of its content including scripts for unaired Game of Thrones episodes as well as full-length episodes. The hackers also demanded a ransom from the network while threatening to release more stolen files.
Hacker group OurMine also hijacked a number of HBO's social media accounts including those dedicated to Game of Thrones and Last Week Tonight with John Oliver.
"While Proofpoint systems blocked this attack, the use of such lures, combined with sophisticated delivery mechanisms and powerful tools like the latest version of the 9002 RAT can open wide doors into corporate data and systems for the actors behind these attacks."
© Copyright IBTimes 2025. All rights reserved.





















