Google Android: Xbot malware contains cocktail of data theft and ransomware

A fresh strain of Android malware called Xbot has been discovered by security researchers that boasts a vicious cocktail of banking Trojan, data theft capabilities and ransomware. Uncovered by the Unit42 security team at Palo Alto Networks, more than 20 Android applications have been found to be injected with the malware to date. While not yet "in the wild" research indicates the developer is rapidly enhancing its capabilities.
"The author appears to be putting considerable time and effort into making this Trojan more complex and harder to detect, it's likely that its ability to infect users and remain hidden will only grow, and that the attacker will expand its target base to other regions around the world," the Palo Alto researchers said in a blog post.
Xbot uses a method of attack called "activity hijacking" to mirror legitimate applications like Google Play and popular banking websites in an attempt to fool users into inserting sensitive credit card data. In its current form the malware developer has targeted seven popular Australian banking applications, however security experts claim the scope of the operation is likely to expand.
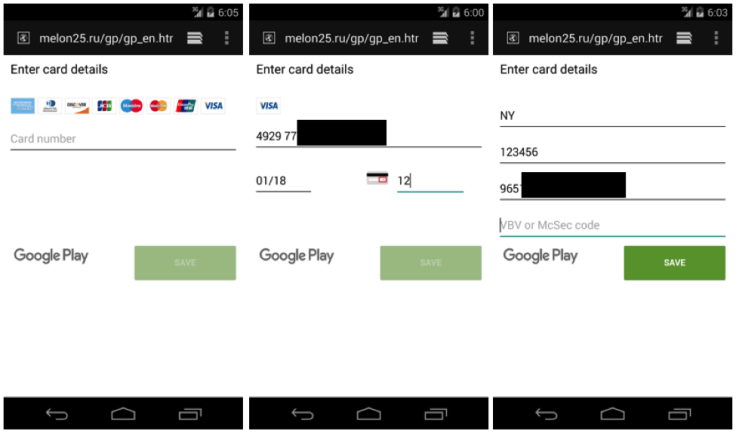
"Of the seven bank apps it is seen to imitate, six of them belong to some of the most popular banks in Australia. However, Xbot was implemented in a flexible architecture that could be easily extended to target more Android apps. Given we also observed the author making regular updates and improvements, this malware could soon threaten Android users around the world," said the research team.
The fake interfaces are downloaded from a server and displayed using WebView, an Android developer tool, however Palo Alto stressed that the legitimate applications are not actually tampered with. While Android users running version 5.0 or later will be protected from a large proportion of Xbot's malicious features, the research team warned that 'all users' are vulnerable to at least some of its capabilities.
Using stealthy tactics, the Xbot malware is also able to encrypt files on the Android device's external storage, such as SD cards, with a form of ransomware called CryptoLocker. Once the files have been locked, the malware operator typically demands payment of $100 to be paid through a PayPal cash card within five days. Furthermore, the Xbot malware can scan the phone for personal data, including text messages and phone numbers, to send straight to the attackers' command-and-control (C&C) server.
© Copyright IBTimes 2025. All rights reserved.






















