Google can remotely unlock 74% Android devices to comply with orders
The internet search giant plans to use default full-disk encryption on Android Lollipop or above

Google can remotely reset the passcode of Android devices running older versions of the operating system pursuant to a search warrant to assist law enforcement authorities. But the same is not the case with those running the higher version.
A report issued by the office of Manhattan district attorney Cyrus Vance, urging law enforcement authorities to require that tech companies provide backdoors to encrypted devices, says "Forensic examiners are able to bypass passcodes on some of those devices using a variety of forensic techniques. For some other types of Android devices, Google can reset the passcodes when served with a search warrant and an order instructing them to assist law enforcement to extract data from the device. This process can be done by Google remotely and allows forensic examiners to view the contents of a device."
But for devices running operating systems like Android Lollipop or above, Google wants to use a default full-disk encryption that will make it impossible for Google to extract the data of the device. Apple is already using the full-disk encryption technology. Certain Nexus brand devices have this encryption implemented already, although not in the Android 5.0 devices.
However, if you want to, you can enable the encryption on your Android devices, regardless of them running on Android Lollipop or not. But performing so will result in performance issues.
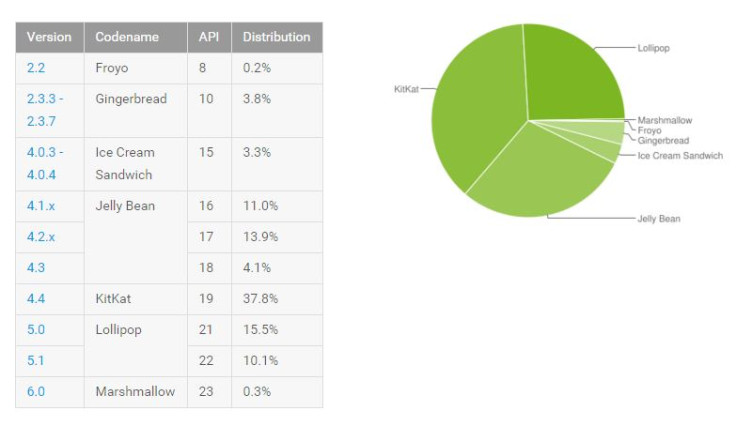
As the Android developer dashboards spotted by TNW suggests, a total of 74.1% devices are running versions lower than Lollipop, which can be accessed by Google.
Unlocking Apple devices
As for Apple, the DA's office report notes the older iPhone 4 models can be unlocked via brute-force. However, using brute-force might make it impossible to access the content on iPhone 4s or later iPhone iterations running version iOS 7. In such cases, the law enforcement authorities need Apple's assistance to obtain data from the device. But with iOS 8, Apple can no longer get access to the content of the devices running iOS 8.
"iOS 8 prevents Apple from accessing data on the device unless Apple has the user's passcode. But, Apple does not keep users' passcodes. Thus, it is no longer possible for Apple to extract data as it did for devices running prior operating systems. According to Apple, as of October 19, 2015, approximately 61% of all Apple devices currently in use run iOS 9, and approximately 30% use iOS 8. Only nine percent use an earlier iOS version," adds the DA's office.
© Copyright IBTimes 2025. All rights reserved.



















