Google Chrome 'missing font' hack is the latest malware scam you need to avoid
This Chrome 'hack' can be used to trick unwitting web users into downloading malware.

Cybercriminals are skilled at coming up with new and innovative ways to trick web users into falling into carefully placed traps to then infect them with malware. One bullish tactic, now reportedly targeting Google Chrome, spreads via a sneaky "missing font" prompt.
The "drive-by infection" hack was spotted on a compromised WordPress website by a security researcher called Mahmoud Al-Qudsi, who found it to be using JavaScript to change how text was displayed on the website and urging users to download a "fix".
How does the Chrome hack work?
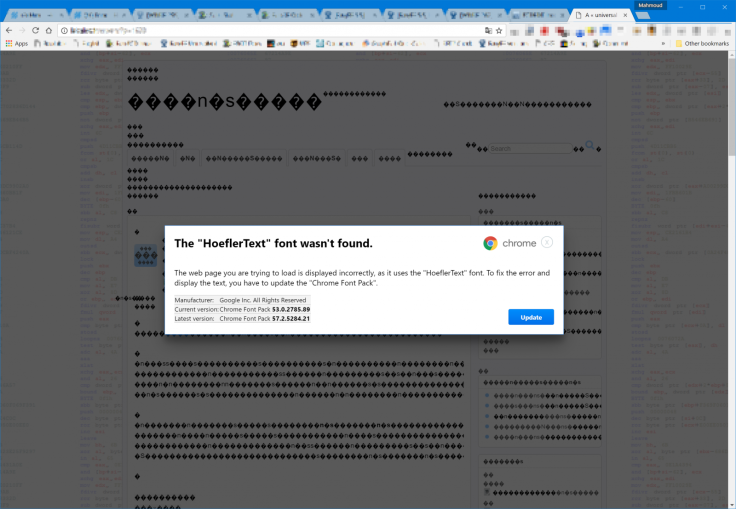
The malicious script caused text on the website to be replaced with "symbols and rubbish" in place of the content, Al-Qudsi wrote in a blog post. Screenshots show the hacker designed a warning box that appears legitimate, using Chrome's branding and colour scheme.
A message displays: The web page you are trying to load is displayed incorrectly as it uses the "HoeflerText" font. To fix the error and display the text, you have to update the "Chrome Font Pack." It has a blue button that appears real at a glance, labelled "Update."
Al-Qudsi said: "This attack gets a lot of things right that many others fail at. The premise is actually believable: the text doesn't render, and it says that is caused by a missing font (a real font, by the way), which it then prompts you to download and install.
"The usage of a clean, well-formatted dialog to present the message with the correct Chrome logo and the correct shade of blue for the update button. The shape of the update button seems correct, and the spelling and grammar are definitely good enough to get a pass."
Furthermore, the file that downloads if a user clicks update is not recognised by either Windows Defender or Chrome as being a virus. When uploaded to VirusTotal, a service which profiles malware, only nine out of 59 antivirus scanners identify it as dangerous.
What does 'missing font' malware do and how to identify it
If infected, VirusTotal revealed the malware will snoop on files and documents and can be used to inspect core Windows system files. Firms that identified the malware successfully included Fortinet, Malwarebytes, CrowdStrike and Symantec.
Luckily for potential victims, there are a number of key warning signs the "update" landing page is a scam. Also, while Chrome itself doesn't view the file as malware, it should still be blocked by a warning that "this file isn't downloaded very often", Al-Qudsi said.
Furthermore, the pop-up box that appears is slightly blurred, which for many internet users is a clear warning sign something is amiss. Additionally, the download file itself does not appear to have an official Google icon, only shattering the illusion further.
In any case, the attack clearly represents the abundance of techniques that cybercriminals can use to infect unwitting people online. Typically, such attacks can be designed – and tailored – for every major web browser or operating system, from Mozilla Firefox to Microsoft Edge.
In January earlier this year, a web developer uncovered that several internet browsers, including Google Chrome, could be manipulated to expose user's personal data by exploiting its built-in "autofill" capabilities.
In a separate attack, which hit Google Chrome last year, an Android banking Trojan dubbed Svpeng was found to be hitting the browser, reportedly infecting over 300,000 devices in a span of just two months.
IBTimes UK contacted Google for comment however had received no response at the time of publication.
© Copyright IBTimes 2025. All rights reserved.






















