Hackers can now earn $500,000 if they keep critical security flaws a secret from Apple
Exodus Intelligence will pay up to $300,000 more than Apple for your undiscovered iOS exploits.

Forget about Apple's bug bounty programme – a US-based private firm is willing to offer security researchers and white hat hackers up to $300,000 (£231,000) more if they report undisclosed software vulnerabilities concerning Apple products to it instead of the technology giant.
Texas-based firm Exodus Intelligence is offering to pay hackers and researchers up to $500,000 if they can provide undiscovered security vulnerabilities, also known as "zero-day vulnerabilities", specifically affecting iOS 9.3 and up, which is $300,000 more than Apple itself will pay.
Even more interesting, if the zero-day exploit continues to stay alive and isn't patched or discovered by the vendor, the hacker will receive an additional bonus payment every quarter that the software vulnerability continues to exist, and the firm also wants to know about vulnerabilities that have been patched, which are called "N-days".
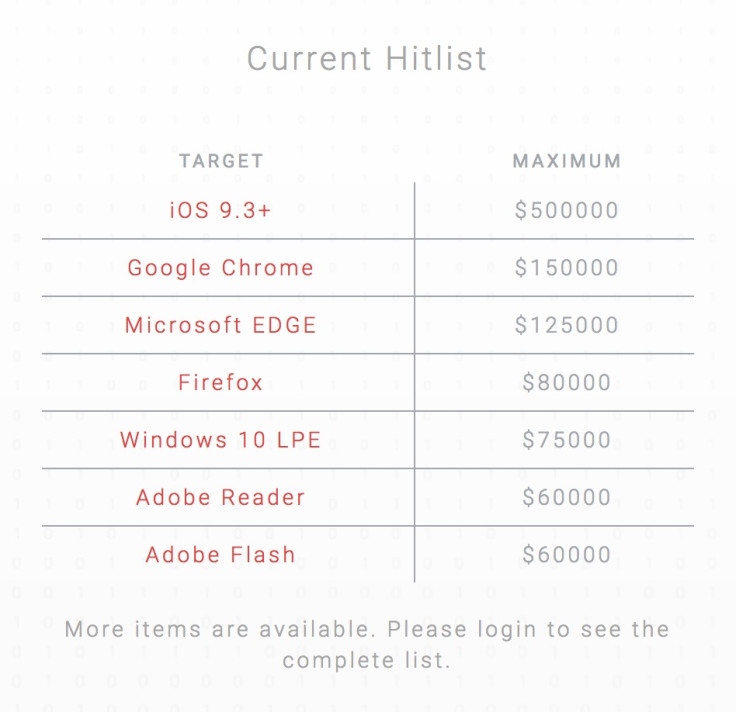
Exodus has published a list of prices for attacks on its website, and after iOS flaws, the next most in demand are attacks for the Google Chrome web browser ($150,000), followed by Microsoft Edge ($125,000), Firefox ($80,000), vulnerabilities specifically relating to the Local Privilege Escalation (LPE) in Windows 10, and vulnerabilities affecting Adobe Flash and Adobe Reader ($60,000 each).
Unlike Apple's invite-only programme, any hacker that would like to take part simply needs to register an account on Exodus' RSP platform and they will be paid by cheque, wire transfer or bitcoin if the vulnerability is accepted.
Why is this a big deal?
It's long been known that there's a huge underground black market on the Dark Web for software bugs that affect crucial operating systems such as Windows, Linux (used for servers), iOS, Mac OS X and Android, as well as certain messaging apps and web services including WhatsApp, Telegram, Facebook, Twitter, Yahoo Mail and Gmail, but no one knows exactly how many there are or how much they are typically sold for – until now.
The idea is that cybercriminals will pay anyone who is willing to tell them about the vulnerability and prevent the operating system or software's vendors from patching the flaw, because it's much better for the criminals if they have a consistent backdoor they can use to hack into a government or enterprise network.
The cybercriminals are also often employed by nefarious clients who hire them to hack into an organisation's servers for profit or spying purposes, or the clients are willing to pay even more money to keep certain security flaws secret, so for example, if there was a flaw that would make it easy for an attacker to spy on all messages sent from any iPhone, certain parties would do anything to keep that from Apple.
And it's not just the bad guys who do it – in December 2015, the FBI admitted that it too uses zero-day exploits in order to spy on potential terrorists and criminals, and it does so without informing the affected vendors either.
Exodus offers a subscription-only database of software bugs that costs its customers $200,000 per annum, targeting antivirus vendors that want to keep their users safe, but the problem is, the service is also open to clients that might seek to capitalise on undisclosed vulnerabilities for whatever nefarious purpose – from hacking for profit to spying on citizens.
© Copyright IBTimes 2025. All rights reserved.






















