Hackers target 'millions of PornHub users' worldwide with booby-trapped advertising
PornHub was not to blame - instead hackers used an ad network to launch attacks.

Millions of internet users in the US, Canada, UK and Australia were recently targeted by a hacking group called KovCoreG which took advantage of PornHub, one of the world's most visited adult websites, to spread booby-trapped downloads posing as browser updates.
Experts from cybersecurity firm Proofpoint said on Friday (6 October) that infections first appeared on PornHub webpages via a legitimate advertising network called Traffic Junky.
The payload would be different depending on the user's web browser of choice – be it Google Chrome, Mozilla Firefox or Apple Safari. In 2016, there were 23 billion total visits to PornHub meaning that, if infiltrated, the potential scope of infections could be huge.
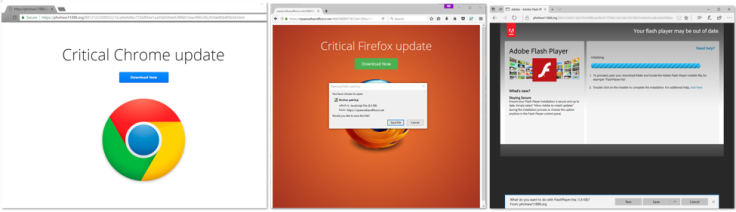
The hackers' campaign used social engineering tactics to trick users into installing malicious updates that would appear via pop-up ads when they visited some PornHub webpages. Potential targets would believe they were updating their computer's legitimate software.
In once instance, it posed as an Adobe Flash upgrade.
If victims clicked on the fake update file the malware would infect their computer system and stealthily click on advertisements in order to make illicit revenue.
In this case the attack was limited to click fraud, but Proofpoint experts said it could easily be adapted to deliver ransomware or information stealing Trojans.
The security firm said the malicious ads have now been removed and commended both the ad network and the website for working quickly to solve the problem.
PornHub did not immediately respond to request for comment from IBTimes UK. In most cases like this, the adult website is a victim of the wider attack - with ad networks the real target.
"Millions of web surfers [...] were potentially exposed to ad fraud malware due to the latest series of large-scale KovCoreG group malvertising campaigns," said Kevin Epstein, the vice president of threat operations at Proofpoint, in a statement.
He continued: "We are pleased that following our notification, the site and advertising network abused in this particular attack worked swiftly to remove the infected content.
"Very few groups have the capability to abuse the advertising chains of some of the world's most visited websites; however, the KovCoreG group is one of them.
"This discovery underscores that threat actors follow the money and continue to perfect combinations of social engineering, targeting, and pre-filtering to infect new victims."
This is far from the first time that adult websites – or the ad networks that live there – have been targeted by cybercriminals to spread adware. It won't be the last.
Back in 2015, researchers from Malwarebytes discovered a widespread operation had hit a slew of popular websites including xHamster, RedTube and PornHub. Yet despite the attempted hacks, experts often note that porn websites are known to have above average security.
If malware does slip through the cracks, they are among the quickest to resolve the issues.
"What we've noticed – and it may come as a surprise – is top adult domains [websites] are actually putting in a lot of resources towards fighting malware," Malwarebytes chief executive officer (CEO) Marcin Kleczynski told IBTimes UK in January after a separate outbreak.
"In fact," he continued, "the turnaround response time we get when reporting an incident to such sites is actually a lot faster than that of mainstream sites."
© Copyright IBTimes 2025. All rights reserved.






















