'Industroyer' malware could be 'biggest threat' to major power grids around the world
ESET and Dragos experts warn the malware could be adapted to hit gas and water.

Last December, government officials in Ukraine launched a probe into a suspected cyberattack on the country's power grid that caused a blackout in the northern part of the capital city of Kiev. It was the second major incident directed at its critical infrastructure within 12 months.
While that case remains under investigation, security researchers from Eset, a Slovakia-based cybersecurity firm, this week said a malware strain known as 'Industroyer' was "highly likely" to have been involved. In a white paper, experts called it an "advanced and sophisticated" threat.
"Industroyer is capable of controlling electricity substation switches and circuit breakers directly," wrote researcher Anton Cherepanov in a blog post (12 June).
The team has warned the malware could potentially be adapted to exploit protocols used in further critical systems including power, water and gas.
Eset said critical infrastructure "switches" can be tampered with to perform various functions – from turning off power to causing damage to the equipment itself. In the 2015 attack, an alleged cyberattack resulted in the lights going off for more than 220,000 people.
"Industroyer's dangerousness lies in the fact that it uses protocols in the way they were designed," Cherepanov wrote. "The problem is that these protocols were designed decades ago, and back then industrial systems were meant to be isolated from the outside world.
"Thus, their communication protocols were not designed with security in mind. That means that the attackers didn't need to be looking for protocol vulnerabilities; all they needed was to teach the malware to 'speak' those protocols." Unfortunately, evidence suggests the malware is fluent.
Upon analysis, Eset researchers found Industroyer has multiple components. At its core is a system backdoor used to manage an attack via a remote command and control (C&C) server, but it can also map networks and issue commands to identify specific industrial devices.
The security firm said its design shows a "deep knowledge and understanding" of control systems, often the beating heart of a country. In addition to its attack function, it can reportedly remain under the radar, ensure persistence and even "wipe all traces of itself after it has done its job."
Cherepanov wrote: "The 2016 attack on the Ukrainian power grid attracted much less attention than the attack that occurred a year earlier. However, the tool most likely used, Win32/Industroyer, is an advanced piece of malware in the hands of a sophisticated and determined attacker.
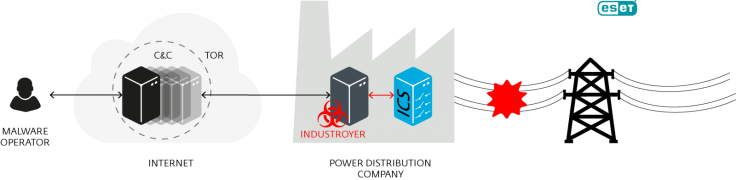
Loose attribution has previously blamed Russian forces of orchestrating the power grid attack. "The analysis of the impact of symptoms on the initial data of these systems indicates a premeditated and multi-level invasion," power supplier Ukrenergo told Reuters at the time.
Ukraine's security chief, Oleksandr Tkachuk has claimed the attacks were linked to a gang using a malware strain commonly known as BlackEnergy. "Russian hackers [have] become an important tool of the aggression against our country," he said in mid-February this year.
In a paper this week (12 June), Eset said it found no links between BlackEnergy and Industroyer.
"The commonly-used industrial control protocols used in this malware were designed [...] without taking security into consideration," the firm warned. "Therefore, any intrusion into an industrial network with systems using these protocols should be considered as 'game over'.

The security experts said, upon analysis, Industroyer could be the "biggest threat to industrial control systems since Stuxnet", a reference to the nation-state cyber-sabotage effort allegedly developed by the US and Israel to help disrupt a nuclear plant based in Iran.
It remains unknown if the Ukrainian power grid attacks were intended as a full-scale digital assault or simply as a test–run, as some experts have suggested in the past.
"Thanks to its ability to persist in the system and provide valuable information for tuning-up the highly configurable payloads, attackers could adapt the malware to any environment, which makes it extremely dangerous," Cherepanov noted.
"Regardless of whether or not the recent attack on the Ukrainian power grid was a test, it should serve as a wake-up call for those responsible for security of critical systems around the world."
Dragos Inc, a separate cybersecurity firm which also analysed the malware, said in a release it has "high confidence" the group behind the December 2016 attack shows links to the Sandworm Team – a hacking unit many experts believe works to further the interests of Moscow.
In its own report into the malware, which it has dubbed "Crash Override", Dragos Inc stated: "The functionality in the Crash Override framework serves no espionage purpose and the only real feature of the malware is for attacks which would lead to electric outages.
"Crash Override could be extended to other industries with additional protocol modules, but the adversaries have not demonstrated the knowledge of other physical industrial processes to be able to make that assessment anything other than a hypothetical at this point."
The firm stressed major electric grids remain extremely reliable. "[The malware] represents alarming tradecraft and the ability to disrupt operations, but the public must understand that the outages could be in hours or days not in weeks or months," it said.
© Copyright IBTimes 2025. All rights reserved.






















