Internet Explorer the 'Most Vulnerable' Web Browser of 2014, States Study: Time to Switch to Chrome and Firefox?
Users of Microsoft's Internet Explorer (IE) are most vulnerable to being targeted by hackers and cyber criminals, according to the findings of a latest study. The study, conducted by Bromium Labs, reported that IE was one of the most exploited web browsers during the first half of 2014.
Bromium Labs' latest study also mentions Adobe Flash as being the primary target of cyber-criminals, during the first half of 2014.
The popular plugin was exploited by hackers via 'Zero Day' attacks.
By launching 'Zero Day' attacks, cyber criminals exploit previously known vulnerabilities that developers fail to address in an application.
"The notable aspect for this year thus far in 2014 is that Internet Explorer was the most patched and also one of the most exploited products, surpassing Oracle Java, Adobe Flash and others in the fray. Bromium Labs believes that the browser will likely continue to be the sweet spot for attackers," states Bromium Labs, in its research report.
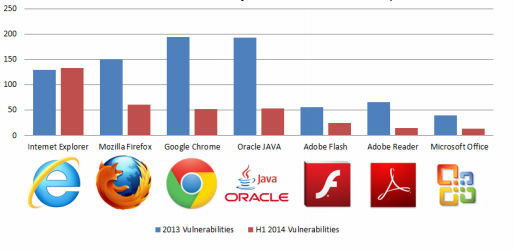
Exploitations on Internet Explorer
Microsoft's IE was targeted more often by cyber criminals, when compared to other web browsers like Firefox and Chrome. The Redmond-based company recently acknowledged and released fixes for as many as 24 vulnerabilities within IE.
According to Bromium Labs, hackers used an emerging 'Zero Day' attack trend called "Action Script Spray" to target Internet Explorer. Action Script Spray techniques are used to launch attacks on Adobe's Flash application, which in turn makes IE vulnerable to threat.
Cyber-criminals also use 'Action Script Spray' to bypass various built-in OS security mechanisms such as Address Space Layout Randomisation (ASLR), which offers protection from buffer overflow attacks.
An 'Action Script Spray' exploit also leads to hackers/cyber-criminals bypassing ASLR, and thereby gaining control over an application, and gradually the entire host system.
Along with 'Action Script Spray', hackers also resorted to 'Internet Explorer memory corruption', by using Return Oriented Programming (ROP) techniques, to bypass the default ASLR mechanism.
ROP is a security exploitation mechanism, using which attackers resort to running customised executable codes, even when security mechanisms such as "code signing" and "Executable Space Protection" are enabled.
Exploitations on Adobe Flash
Engineers at Bromium Labs say that hackers and cyber-criminals exploited ActionScript, an object-oriented programming language using which new features for Adobe Flash are developed, via new features that Adobe released in 2013.
Cyber criminals exploited Action Script Virtual Machine (ASVM) flaws using 'Action Script Spray'.
Also, built-in OS security mechanisms were bypassed by criminals by exploiting to the hilt non-ASLR libraries.
"This is further evidence that the world of Web browser plugins presents a weak link that is just waiting for exploitation in the future," says Bromium Labs.
"In addition to that, the prevalence of IE+Flash is much higher than IE+Java Jave Runtime Environment (JRE), so this provides the attackers with a bigger opportunity," the engineers added.
Microsoft reportedly is aware of the latest vulnerabilities that plague its web browser.
"We're aware of the reported issues, one of which has been addressed in newer versions of Internet Explorer," said a Microsoft spokesperson to The Guardian.
"Each version of Internet Explorer is more secure than the last and contains new and improved security features that help protect customers," the spokesperson added.
Bromium Labs' latest findings are a concern considering the fact that Microsoft Windows still runs dominant on majority of the world's computers.
The latest reports could also serve as a shot-in-the-arm for both Google and Mozilla, both of which have a significant share in the web browser arena.
© Copyright IBTimes 2025. All rights reserved.





















