IoT malware on the rise with hackers hijacking devices to launch DDoS attacks
IoT devices become prime targets for hackers due to lax security, say security researchers

Security surrounding IoT (Internet of Things) devices has long been a major cause of concern to experts, especially given the increasing use of IoT botnets by cybercriminals to leverage attacks. However, IoT malware botnets now appear to be on the rise, allowing hackers to launch DDoS attacks on unsuspecting owners of connected devices.
Symantec security researchers said that IoT malware was found to be primarily targeting "non-PC embedded devices", most of which are connected to the internet but do not come with any advanced security settings given the limited processing abilities of their OS (operating systems).
"2015 was a record year for IoT attacks, with eight new malware families emerging," said Symantec's researchers, adding that a deeper analysis of IoT malware samples found that "the highest number of IoT attacks originated in China, which accounted for 34% of attacks in 2016; 26% of attacks stemmed from the US, followed by Russia (9%), Germany (6%), the Netherlands (5%), and Ukraine (5%). Vietnam, the UK, France, and South Korea rounded out the top 10."
Nick Shaw, Vice President and General Manager EMEA at Norton by Symantec told IBTimes UK: "As we continue to adopt more internet-connected devices in our daily lives - from fitness trackers and routers to home security systems, smart TVs and baby cameras - cybercriminals are starting to pay attention. These new internet-accessible devices can bring great benefits, but they are also increasingly easy and lucrative targets for cybercriminals."
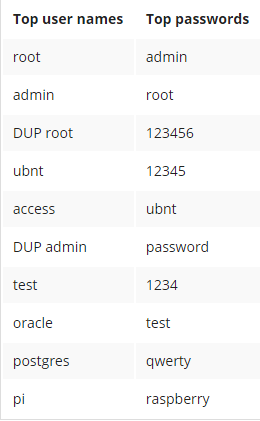
Top 10 passwords used by hackers to hijack devices
Symantec researchers were able to uncover the top most common passwords used by IoT malware and its operators, in efforts to log onto to connected devices. The combinations of "root" and "admin" were found to lead the charts, with "user name: ubnt and password: ubnt" coming a close second. Researchers say that the top password combinations indicate that users most likely do not change default passwords. Additionally, the appearance of "user name: pi and password: raspberry" in the commonly used password chart reveals an alarming trend of hackers increasingly targeting Raspberry Pi devices.
"Cybercriminals are interested in cheap bandwidth to enable bigger attacks. They obtain this by hijacking our devices and stitching together a large web of consumer devices that are easy to infect because they lack sophisticated security. All they need to do is pre-program their malware with commonly used and default passwords, allowing them to easily hijack devices' passwords," Shaw added.
How to stay safe
Given the lax security features on connected devices, it is imperative that users become aware of the potential security issues that come with not being attentive about password strength and security updates for devices. In order to avoid devices from being hijacked for future DDoS attacks, users should opt for strong passwords, changing the default credentials with a much stronger alternative. Moreover, users should be vigilant about new security updates provided by manufacturers to protect themselves against potential attacks.
"DDoS attacks remain the main purpose of IoT malware. With the rapid growth of IoT, increased processing power in devices may prompt a change of tactics in future, with attackers branching out into cryptocurrency mining, information stealing, and network reconnaissance," Symantec researchers warned.
© Copyright IBTimes 2025. All rights reserved.






















