MarsJoke ransomware targets US government organisations, gives victims 96 hours to pay up before deleting files
The ransomware was detected as being distributed via the Kelihos botnet and is demanding $320 as ransom.

A new active ransomware campaign has been detected targeting US government and educational institutions. The ransomware was dubbed MarsJoke after researchers uncovered a "string contained within the code: 'HelloWorldItsJokeFromMars'". The ransomware gives victims 96 hours to pay up the ransom, after which it begins deleting files.
Proofpoint researchers ascertained MarsJoke to be part of a "large-scale" email campaign, being distributed via the Kelihos botnet. The ransomware developers are demanding victims pay up $320 (0.7 bitcoins). The primary targets appear to be US state and local governments as well as K-12 educational institutions. The campaign also targeted healthcare, telecommunications, insurance and other organisations, however in "smaller numbers".
Proofpoint researchers said: "On September 22, Proofpoint detected a large MarsJoke ransomware email campaign. Emails contained URLs linking to an executable file named "file_6.exe" hosted on various sites with recently registered domains, apparently for the purpose of supporting this campaign. This is a departure from the much more frequent attached document campaigns we have observed recently with a range of malware, including the widely distributed Locky ransomware. "
Victims lured with 'convincing' content
In efforts to lure in victims, the ransomware's email campaign was found to be using "convincing" content, with a wide variety of subject lines "referencing a major national air carrier, adding an air of legitimacy to the lures with stolen branding". Some of the subject headings used in the emails included, "checking tracking number", "check your package" and "tracking information".
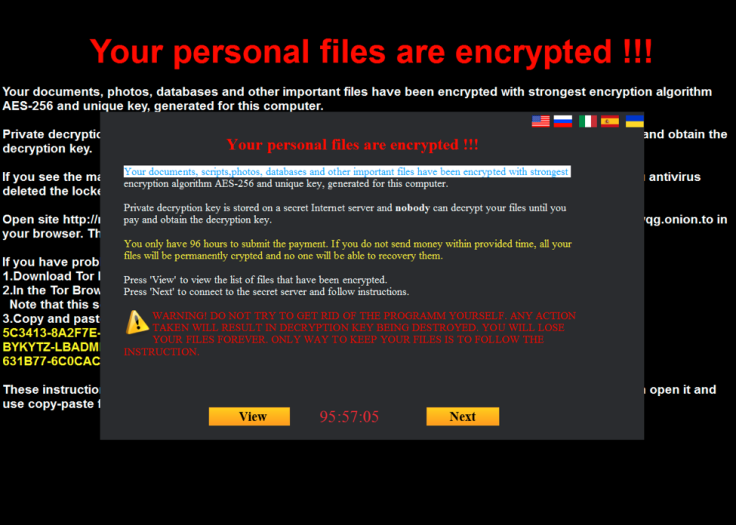
MarsJoke changes victim's desktop background
Proofpoint researchers discovered that MarsJoke made changes to the victim's desktop background and introduced pop-up ransom messages, which came in various languages. "The victim's desktop background is changed and a dialog pops up presenting the ransom message. This dialog is available in several languages, including English (the default during testing), Russian, Italian, Spanish, and Ukrainian," the researchers said.
The message also came with a warning to users that read: "Warning! Do not try to get rid of the program yourself. Any action taken will result in decryption key being destroyed. You will lose you files forever. Only way to keep you files is to follow the instructions."
Users are also provided the option of interacting with the ransomware developers via an "onion-hosted web panel", which provides detailed instructions on how to pay the ransom.
Proofpoint researchers concluded: "Ransomware has become a billion dollar a year industry for cybercriminals. In the case of the MarsJoke campaign described here, K12 educational institutions and state and local governments are often seen as easy targets because they lack the infrastructure and funding to ensure robust backups and strong defensive resources are in place to prevent and mitigate infections. MarsJoke does not appear to be 'just another ransomware', though. The message volume and targeting associated with this campaign bear further monitoring as attackers look to monetize new variants and old strains saturate potential victims."
The identity and location of MarsJoke's developers remain unclear. It is also uncertain, especially given the primary targets were US government sites, whether the campaign may be part of an elaborate cyberespionage campaign. IBTimes UK has reached out to Proofpoint for further information and will update this article upon receiving a response.
© Copyright IBTimes 2025. All rights reserved.






















