Microsoft, FBI, Interpol and other law enforcement agencies disrupt Dorkbot botnet infecting one million PCs
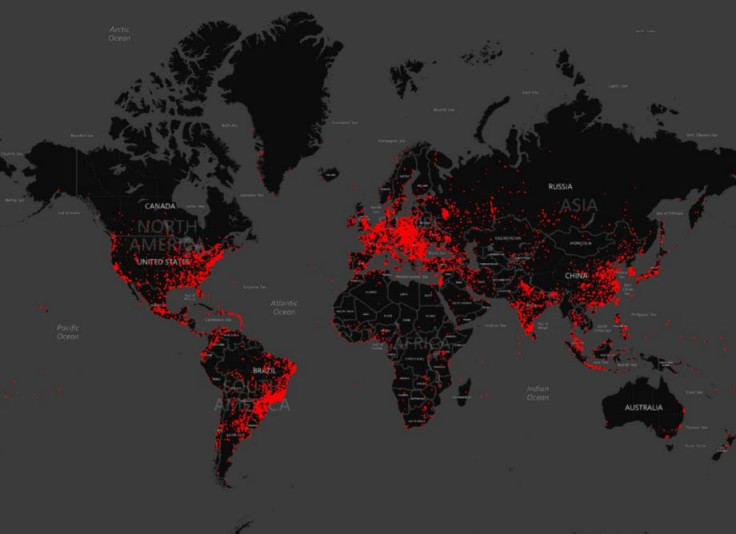
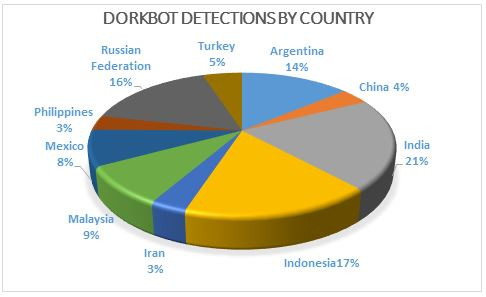
The most notorious malware family – Win32/Dorkbot – discovered in April 2011, has infected more than one million PCs in 190 countries across the globe. The top 10 countries infected by this malicious software such as Argentina, China, India, Indonesia, Iran, Malaysia, Mexico, Philippines, Russia and Turkey, represent 61% of the infection.
Dorkbot spreads through USB flash drive, instant messaging or social networks. It lets hackers steal user names, passwords and other personal information by disabling security protections. Dorkbot can even download other malware and prevent users from visiting security-related sites.
Microsoft, along with a number of law enforcement agencies, has managed to disrupt the malware that has infected on an average 100,000 machines each month for the past six months. The agencies are CERT Polska, ESET, the Canadian Radio-television and Telecommunications Commission (CRTC), the Department of Homeland Security's United States Computer Emergency Readiness Team (DHS/USCERT), Europol, the Federal Bureau of Investigation (FBI), Interpol, and the Royal Canadian Mounted Police (RCMP).
Dorkbot is an Internet Relay Chat (IRC) based botnet. The main objective of Dorkbot is to steal online account user names and passwords, and other personal identification information.
"It is commercialised by its creator as a "crime kit" called NgrBot, which hackers can buy though underground online forums. The kit includes the bot-builder kits as well as documentation on how to create a Dorkbot botnet. Figure 4 and 5 show one of the builder interfaces for Dorkbot - illustrating all available functionalities that the operator can set through the kit, including the IRC server settings and the command settings," Microsoft explains.
Targeted sites
Dorkbot monitors and intercepts browser communications with various websites by connecting network-related APIs. Then it steals the user name and password used to log into a particular site. Microsoft confirms that AOL, eBay, Facebook, Gmail, Godaddy, OfficeBanking, Mediafire, Netflix, PayPal, Steam, Twitter, Yahoo and YouTube are a few of the sites that were being targeted by Dorkbot for stealing user login and password.
How hackers spread Dorkbot
Dorkbot was distributed within a loader module, which carries its own code for updating and distributing other malware. The loader is also responsible for guiding Dorkbot's connection to command-and-control (C&C) server. The loader module contains a download URL in its binary. The binaries in these URLs are Dorkbot's downloader component, self-update and other malicious software.
Dorkbot can receive commands to download and install malware on the infected computers. It also downloads other malware families. Once a Dorkbot worm spreads malware into a computer, it connects to a C&C server. After connecting to the C&C server, the infected system gets instruction to download other malware or spread to other computers.
How to protect your PC from Dorkbot
While your system could be one of those infected ones, consider the following cautionary measures;
• Be wary when opening emails or social media messages send by users unknown to you.
• Always download software from the programme developers only.
• Run antimalware software on your PC.
If your machine is running Windows, use Windows Defender for Windows 10 that offers you the latest protection against Dorkbot threats. You can also use standalone tools such as Microsoft Safety Scanner and Malicious software removal tool (MSRT) to detect and remove Dorkbot.
© Copyright IBTimes 2025. All rights reserved.





















