Mysterious hackers attempting to bring down entire internet by DDoS-ing critical servers

Mysterious hackers are yet again trying to bring down the entire internet by bombarding crucial servers that support it with a gigantic, sustained distributed denial of service (DDoS) attack, which has caused webpages to load slowly in some locations.
There are 13 internet root name servers in the world that run the internet, and these servers are responsible for helping your web browser to locate top-level domains such as .com, .org, .net or any country-specific top level domains like .uk, .fr, .sg, .de, .ae and .cn. The servers function as a sort of internet address book and they make up what is known as the domain name system (DNS) system.
The 13 root name servers are run by independent organisations in the world, including ICANN, the US Army, the US Department of Defense, Nasa, Europe's internet registry RIPE NCC, the University of Southern California, Japan's Wide Project and Sweden's Netnod. Network infrastructure solutions firm Verisign also operates two of them, namely the "A" and "J" root servers (the 13 servers are named in sequence after the alphabet from A-M).
DDoS attack sent 5 million queries per second
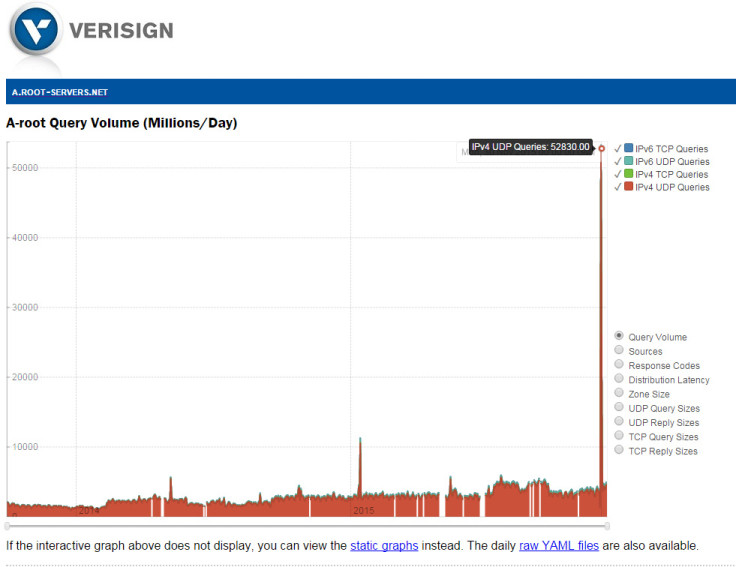
Between 30 November and 1 December, an entity carried out an enormous DDoS attack against these 13 root name servers, flooding them with a deluge of traffic from multiple IPv4 addresses, so that the servers received more than five million queries per second, and more than 50 billion queries in total during the two-day period. To give you context, over the past two years, the most queries Verisign's A root name server received per day on average has never topped more than 10 billion queries.
"While it's common for the root name servers to see anomalous traffic, including high query loads for varying periods of time, this event was large, noticeable via external monitoring systems, and fairly unique in nature," Root-servers.org, which is run by the operators of the root name servers, wrote in its incident report.
"The incident traffic saturated network connections near some DNS root name server instances. This resulted in timeouts for valid, normal queries to some DNS root name servers from some locations."
You might think that the servers would be knocked offline by that much traffic, but no, they were saved by the root server operators having enough additional servers on standby that were able to balance the load of traffic.
Although the sustained cyberattack resulted in some real queries from users surfing the web timing out in some locations, there were no complaints that end-users were having severe internet problems, so the root server operators believe that the attack would have been "barely perceptible" and all anyone would have seen was a slight delay in loading webpages in some web browsers.
The root name server operators also stated that since IP source addresses can be easily spoofed and the traffic flooded multiple anycast websites, it is impossible to trace the traffic back to its source, so we have no idea who was behind this.
Only a government could have this much clout
However, if you use logic, it would take a really powerful entity like a country's government to have the resources to sustain a coordinated cyberattack that lasted 48 hours and was able to keep flooding the root name servers consistently with a high level of traffic at five million queries a second.
This is not the first time this has happened either – on 21 October 2002 a DDoS attack campaign attacked the 13 root name servers for one hour, and on 6 February 2007 a DDoS attack was sustained for 24 hours.
In the first incident, the attackers didn't have enough traffic to fully flood the servers and take them offline, while the second incident saw two root servers suffer badly, while another two servers experienced heavy traffic.
So who could it be? Is it a foreign government, a terrorist group or cybercriminals? Who knows, but they seem to be getting better at it.
© Copyright IBTimes 2024. All rights reserved.























