Open-source code from Mars rover used in espionage campaign targeting Indian government

Two open-source code libraries used in the development of the historic Mars rover have been exploited by cybercriminals and moulded into an effective espionage tool that is being used to target high-level officials in the Indian government.
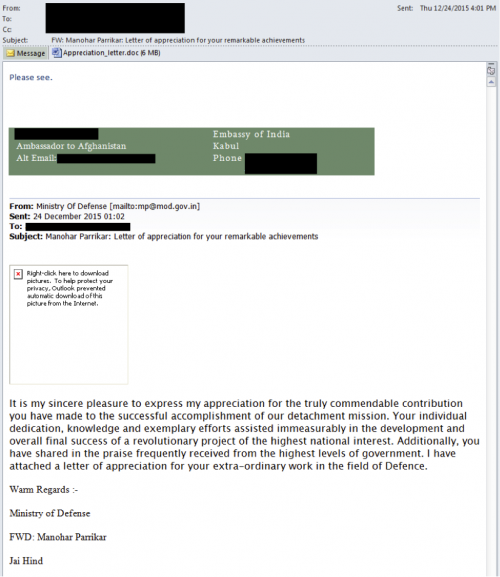
First exposed by security researchers at Palo Alto Networks, the malware, now dubbed Rover, was found in a malicious phishing email received by India's ambassador to Afghanistan that was made to look like it was sent from India's defence minister which, if opened, would have installed a slew of vicious exploits on the computer system.
Upon analysis, the experts found the malware, which contained code that attacked a flaw in Office XP, boasted a range of spying features including the ability to hijack computer files, launch a keylogger, take screenshots and even record audio and video in real-time. All of the data compromised would be sent straight to the malware creator's command and control (C&C) server.
It is the audio and video components, using libraries OpenCV and OpenAL, that give the cybercriminals operating the malware the recording functions. OpenCV, for instance, is frequently used by technology firms and government departments in the creation of computer vision applications, unmanned vehicles, object tracking and even AI systems. Inspiring the name, it was also used by the Mars rover to capture images and send the data back to Nasa. Meanwhile, OpenAL is an audio API that renders "three-dimensional positional audio" for a multitude of computer platforms.
Despite being branded as an unsophisticated piece of malware as it lacks a lot of the modern snooping features of recent exploits, Palo Alto said this actually helps it to remain undetected by many anti-virus tools being used today. At the time of discovery, two out of three Rover malware samples were not detected by any protection product.
"It is interesting to see the very code used in such significant projects also being used to track and spy on individuals being targeted and which can remain undetected by traditional security systems," said Palo Alto researchers in a blog post.
"Though Rover is an unsophisticated malware lacking modern malware features, it seems to be successful in bypassing traditional security systems and fulfilling the objectives of the threat actor behind the campaign in exfiltrating information from the targeted victim. It is important to understand the techniques and tools being used by such threat actors to better defend and protect organisations from such threats."
While the creators of the malware remain elusive, it is likely the close relationship between India and Afghanistan in funding economic development and key infrastructure over the past few years has piqued the interest of numerous groups or nations that would be interested in spying on key high-profile Indian government officials.
© Copyright IBTimes 2025. All rights reserved.






















