Pharmaceutical and manufacturing firms hit by 'Operation Ghoul' hack attack
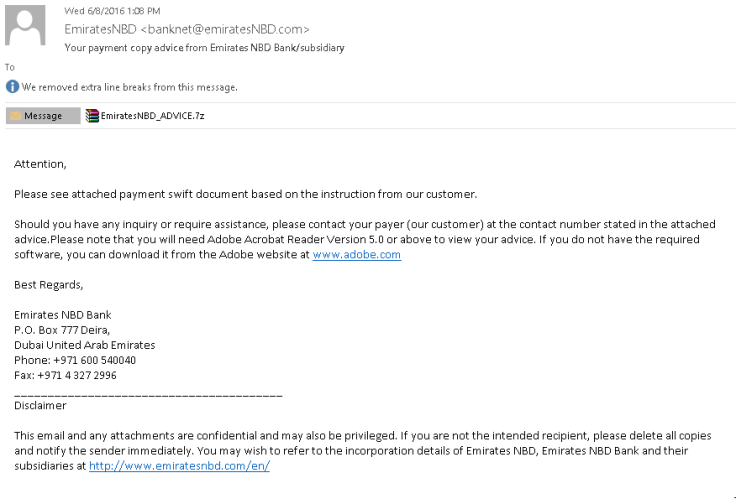
Hackers use fake emails made to look like payment documents.

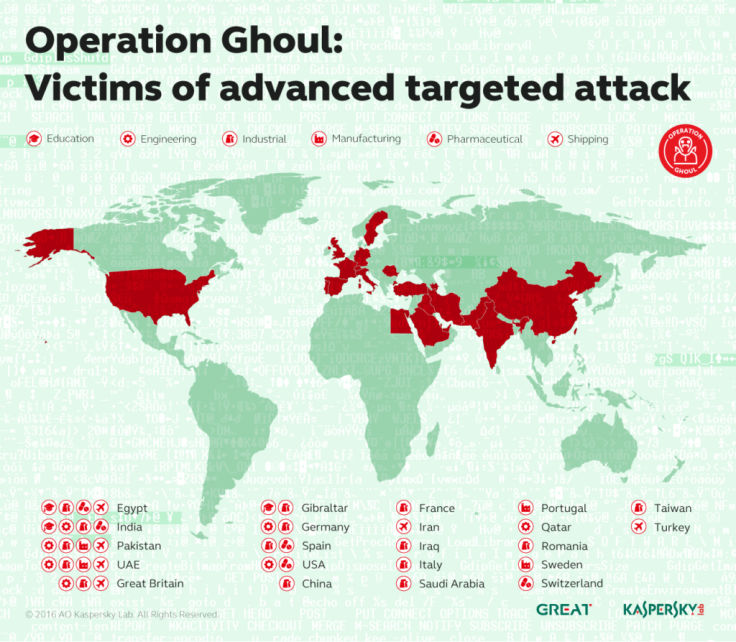
A sophisticated cybercrime operation targeting industrial and engineering firms in over 30 countries across the world with the aim of stealing financial data has been exposed by security researchers at Kaspersky Lab.
The cybercriminals behind the campaign, dubbed Operation Ghoul, have reportedly attacked over 130 businesses so far using email phishing tactics to spoof letters from banks in an attempt to get unsuspecting recipients to hand over sensitive corporate information.
The fake emails are most frequently made to look like payment documents, and often include Zip files loaded with malware, Kaspersky said. Additionally, the hackers have been known to use phishing links – which are still shockingly effective to the untrained eye.
Once inside a network, the Operation Ghoul group uses malware that is able to steal passwords, take screenshots of computer screens and even send real-time keystrokes to the hackers' own servers.
While the hackers largely focus on countries in the Middle East, the attacks are not confined to any one region. According to a report released on 17 August, targeted countries also include Spain, Pakistan, the United Arab Emirates (UAE), India and Egypt.
The operation recently swelled in mid-June, Kaspersky noted, yet it has been in existence since at least March 2015.
The malware used has been analysed by the cybersecurity researchers, who found it was derived from a piece of commercial spyware called Hawkeye. This alone is able to collect everything from browser data to information on email clients and records relating to poplar messaging applications.
"Since the beginning of their activities, the attackers' motivations are apparently financial, whether through the victims' banking accounts or through selling their intellectual property to interested parties" said Mohamad Amin Hasbini, senior security researcher at Kaspersky.
"Most infiltrated victim organisations are considered SMBs [and] the utilisation of commercial off-the-shelf malware makes the attribution of the attacks more difficult."
Hasbini, speaking to Kaspersky's ThreatPost, elaborated: "Unlike state-sponsored actors, which choose targets carefully, this group and similar groups might attack any company.
"Even though they use rather simple malicious tools, they are very effective in their attacks. Thus companies that are not prepared to spot the attacks, will sadly suffer."
To combat its attacks, Kaspersky said people with access to sensitive files need to be extra vigilant about suspicious links or emails. "Privileged users need to be well-trained and ready to deal with cyber threats; failure in this is, in most cases, the cause behind private or corporate data leakage, reputation and financial loss," Hasbini added.
© Copyright IBTimes 2025. All rights reserved.






















