Regin Malware: UK, US or Israel Likely Creators of the New Stuxnet

More information has been published about the sophisticated Regin malware, as western powers are fingered as the most obvious creators.
The first details about the Regin malware were published by Symantec detailing a highly targeted attack which was capable of taking control of systems to spy on government organisations, businesses and private individuals. The security company failed to identify where Regin originated from, saying only that it looked like the work of a nation-state.
As more details about the complex computer code begin to emerge, some prominent security experts have said the most likely suspects are the UK, US or Israel.
Speaking to the Guardian, Mikko Hypponen from F-Secure ruled out China and Russia as the creators of Regin: "We believe Regin is not coming from the usual suspects. We don't think Regin was made by Russia or China."
As reporter Tom Brewster-Fox points out, this only really leaves the US, UK or Israel as the countries with the technical know-how to create a piece of malware as sophisticated as Regin.
Another F-Secure expert, Sean Sullivan, responded to this assumption saying: "That is a very astute observation on your part...there are no other countries I can think of."
Hopscotch, Legspin, Starbucks and S**t
Symantec reported that the majority of infections were found in Russia and Saudi Arabia, with Ireland and Mexico next on the list, though the attacks are highly targeted, with Kaspersky's research suggesting there are only 100 victims found so far, since the malware first surfaced in 2008.
According to new details published by Kaspersky Lab, which has been tracking Regin since 2012, there is further evidence to back up claims this malware was written by English-speaking authors.
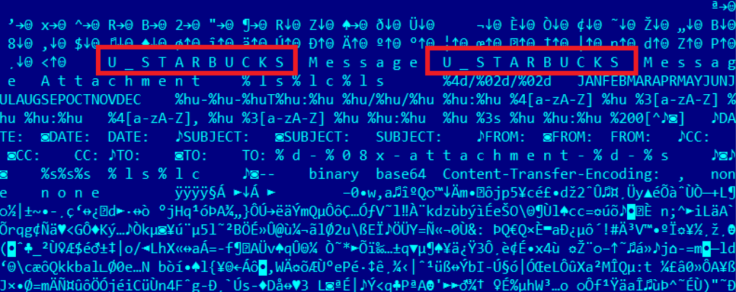
Within the virtual file system of Regin, Kaspersky Lab researchers found the words "legspin", "hopscotch", "Starbucks" and "s**t" which could suggest a collaboration between the US and the UK given the origin of these words.
The research from Kaspersky Lab revealed an additional feature of Regin, showing that the sophisticated piece of malware is capable of manipulating GSM networks allowing them take control of the phone on the network.
"In today's world, we have become too dependent on mobile phone networks which rely on ancient communication protocols with little or no security available for the end user," said Costin Raiu, Director of Global Research and Analysis Team at Kaspersky Lab.
"Although all GSM networks have mechanisms embedded which allow entities such as law enforcement to track suspects, other parties can hijack this ability and abuse it to launch different attacks against mobile users."
Kaspersky Lab revealed that the people behind Regin were able to infect one major operator in the Middle East, giving them "access to information about which calls are processed by a particular cell, redirect these calls to other cells, activate neighbour cells and perform other offensive activities," Kaspersky Lab researchers wrote. "At the present time, the attackers behind Regin are the only ones known to have been capable of doing such operations."
© Copyright IBTimes 2025. All rights reserved.






















