Machine learning cybercrime experts tip Monero to join Bitcoin for darknet ransomware
Security experts Webroot predicts Bitcoin may be replaced by privacy-centric cryptocurrency Monero.

For a long time Bitcoin has been the de facto currency of the darknet, where its pseudonymity can be made more obscure by mixing transactions using specially designed tumbling services.
But the blockchain provides an immutable record so, as attempts by law enforcement to track transactions have evolved, and technology savvy analysis firms have emerged, users are looking for ways to improve their privacy.
Webroot, a security company which uses machine learning to identify cyberthreats, predicts Bitcoin may be replaced by privacy-centric cryptocurrency Monero, as the preferred currency of ransomware merchants on the darknet.
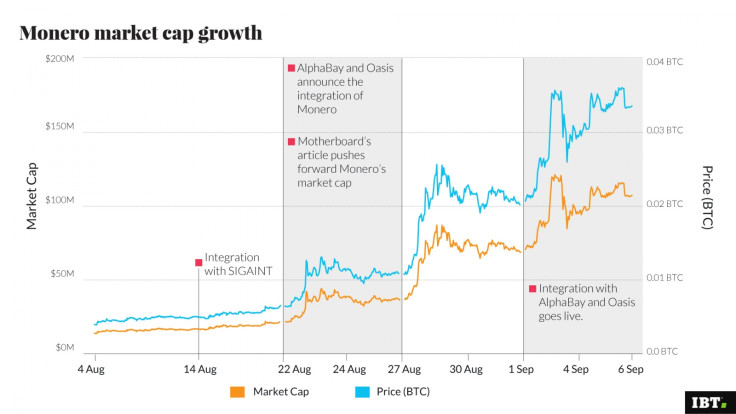
Monero uses ring signatures in clever ways to bulk together transaction inputs and outputs so that all possible spenders appear "equiprobable". A couple of weeks ago dark marketplace AlphaBay announced it would be integrating Monero and the price of the currency has since rocketed amid a flurry of interest.
Tyler Moffitt, senior threat research analyst and one of Webroot's cryptocurrency security specialists, said he is yet to see any ransomware take Monero as the source, but expects he will.
He told IBTimes UK: "It's just easier to accept the overwhelmingly more popular Bitcoin currency and then exchange. So it's just darknet services thus far, but I do expect this to increase as the buzz continues.
"This was to be expected with a cryptocurrency that is secure and untraceable. Cybercriminals are going to be exchanging all of their Bitcoins for Monero to evade detection from firms like Chainalysis."
Moffitt talked through the history of malware on the dark net. Pre-Bitcoin, the money mules used in this context were the likes of Ukash and MoneyPak. The original CryptoLocker did not use Bitcoin, so people would have to go to a gas station or local shop and pay cash for what was essentially a sort of gift card with a scratch-off code and input that code to get their files back.
Bitcoin typically removes costly intermediaries, so now 100% of a ransom could be recovered in a manner perceived to be pretty much secure. To make things less traceable, Bitcoin laundry services could be hired, where an algorithm will send a bunch of Bitcoin through millions and millions of wallet addresses back and forth and then out the end, minus a small percentage for the launderers. Bitcoin has thus been something of a boost to ransomware authors and it's an area of business that continues to grow at a rapid click.
However, governments, law enforcement and crypto technology companies have created tools that can figure out the algorithms, so it's not surprising there is a lot of interest in Monero.
Webroot by virtue of its machine learning capabilities is sensitive to all kind of trends and behaviours in this space. It can detect malware threats that perhaps have never been seen before, but which are flagged up because of certain suspicious behaviours.
Talking about typical behaviours in this running battle, Moffitt goes off like a gatling gun: "There's tons of new stuff coming out all the time and they are always changing tactics, whether it be small granular layers of changing up individual signatures, where they try and spoof Microsoft signatures or Adobe or whoever; they just sort of change the signatures like one byte or whatever they want to change.
"Another common thing we see is leaving the VSS admin, which is the volume system shadows which is actually what all ransomware do now. Ever since XP and above, the volume shadow service allows you to have files as far as to restore them, like a system restore point. Ransomware kills those and almost nothing is going touch the VSS.
"So that's one of the exact behaviours we look for, deleting the VSS admin. The command, delete shadows/all – when we see that, we are going to go ahead and flag it even if it's never been seen before."
Moffitt pointed out that the whole area of ransomware as a service (RaaS) has evolved to smooth out any frictions when making payments, such as creating Bitcoin wallet addresses, buying coins or installing layered Tor browser, which could prove challenging for the less tech savvy.
"I have seen even actual chat boxes, chat support windows inside the ransomware GUI, where you get to talk though the command and control server in encrypted messages with the actual ransomer.
"They will walk you through it, because in a lot of cases the people paying are from an older generation. We see some where they tell you that your files were encrypted by somebody else and that they are here to help you decrypt your files, just pay us our flat rate fee and we will get you files back for you.
"I have even seen a just straight through email where you have these links to these websites that have secret messages that are unique basically only to the receiver and they only display once and then you can never view it. It's sort of like self-destructing messages, where they tell you how to do everything you need to do and they still can't get caught."
Ransomware as a service allows prospective ransomers with no coding experience to go to darknet portals and webpages, where they can start right away to input the few required bits of info. This typically would include: how much you want to charge, how long before stuff is erased, how much you want to charge where it's late, and your Bitcoin wallet address.
Moffitt said: "You can make your own ransomware samples; just generate the binaries right there. So let's say somebody who is maybe renting a botnet and just doing phishing scams to drain PayPal accounts; they have no coding experience really but are just renting all of the tools.
"Now they can create a malware payload and upgrade his scam to the ransomware level with really almost no knowledge whatsoever. That's sort of what we are seeing and over time I fully expect to be talking about ransomware and cryptocurrency being used five, ten years from now; it doesn't seem to be going away."
Hal Lonas, chief technical officer Webroot and an MIT graduate in Aeronautics and Astronautics, added that machine learning is the only way to keep up with emergent treats.
Lonas said most security solutions are not behaviour based. "They are out there looking for something static, an exact thing. They will kind of have a catalogue of existing ransomware and when they recognise something will say when the executable lands on my hard disk they are going to shut down.
"But if it's a new executable or it's a new exploit, a new vehicle to deliver it then they are not so good at finding it. You have to look deeper into the operating system to look for that kind of behaviour.
"If we have never seen a ransomware variant before we can detect it and we will Automatically remove it and remediate any damage it's done."
© Copyright IBTimes 2025. All rights reserved.






















